The cybersecurity landscape is becoming increasingly complex, with attackers continually…
11 results for keyword "Typosquatting"
Six Examples of Impersonation Attacks and How to Shield Your Business
Impersonation attacks are smarter and more deceptive than ever, with…
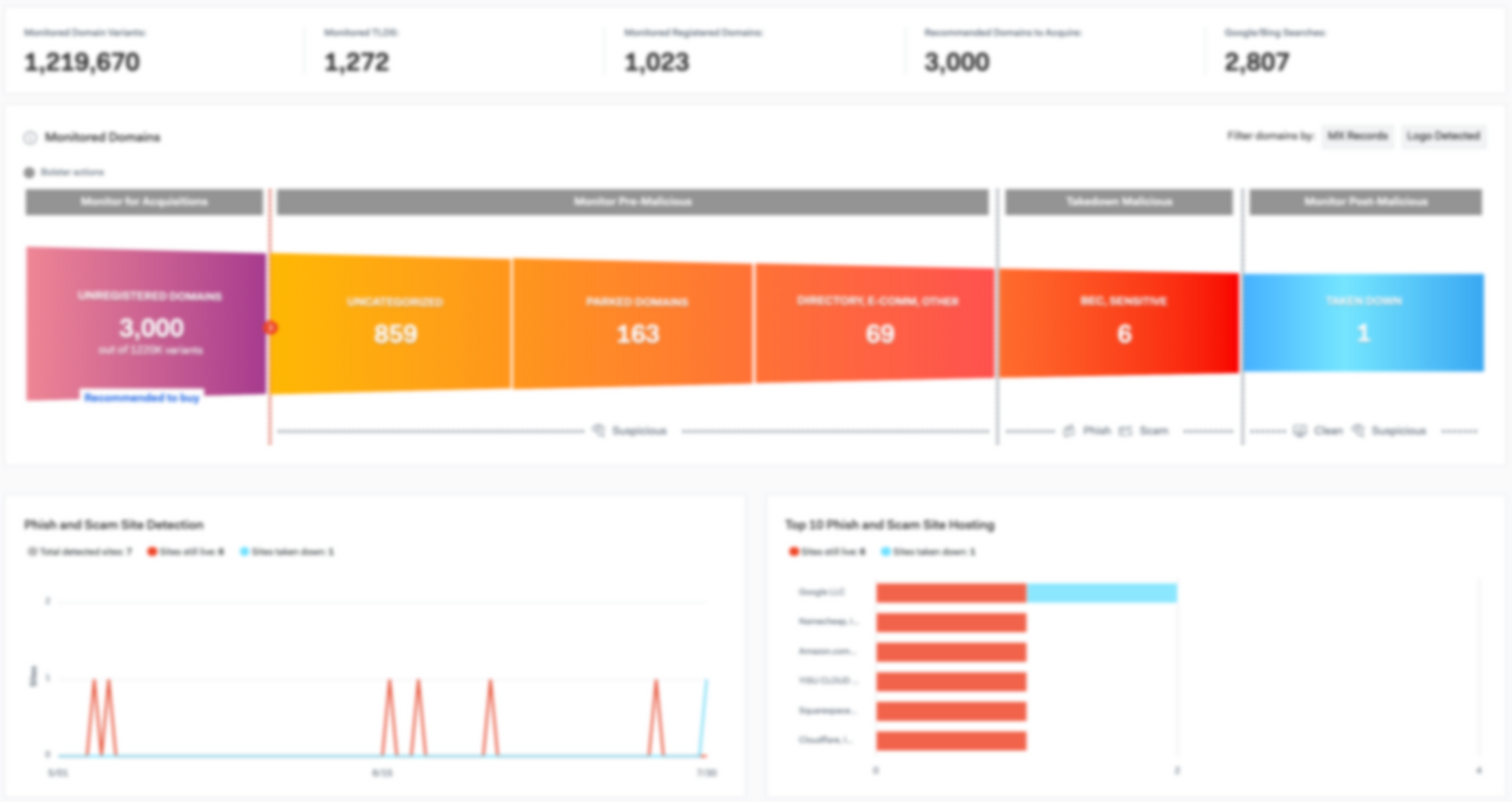
Digital Risk Monitoring Importance is Growing Faster Than Ever
In a digital landscape that seems to be changing daily…
8 Ways to Prevent Typosquatting Attacks Targeting Your Business
Typosquatting is a tactic nearly as old as the…
How to Avoid Online Shopping Scams on Amazon Prime Day
Prime Day is Amazon’s largest, most highly anticipated retail…
Embedded Secrets in Webpage DOMs (and How to Use this Data to Protect Your Assets)
The dangerous impact of typosquat domains, and how frequently…
How to Remove a Typosquat Domain Targeting Your Company, Even When the Registrar Won’t Comply
Typosquat domains can damage not only an organization’s finances,…
How SSL Monitoring Can Help Safeguard Your Brand’s Identity
Phishing and scam websites often use SSL certificates to…
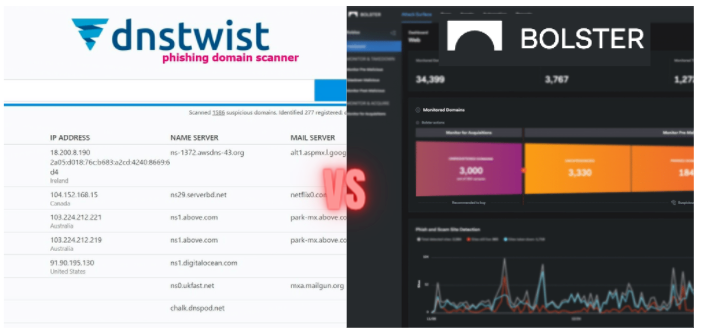
Comparing Bolster’s Typosquatting Monitoring Tool to other OSINT Tools
What is Typosquatting? Cybercriminals register look-alike domains of well-known…
What Every CISO Should Do to Fight Typosquat Attacks
Microsoft recently secured a court order to takedown ‘homoglyph’ domains…
NFT Scams Part 2: Typosquatting Attacks targeting NFT marketplace users
Before we get started, there are a couple of terms…