Dark Web AI Monitoring
Gain Actionable Insight Into Exposed Business-Critical Credentials and Potential Threat Trends
Your Fast-Path to Understanding Exposed, Compromised Accounts From Complicated Dark Web Sources
Designed for actionable insight and quick remediation, Bolster’s AI-powered Dark Web Monitoring provides our customers with instant visibility into where specific threats exist on the dark web so security teams can act quickly and accurately to protect their data.
With simple, actionable insight into specific threat exposure, you can take quick and accurate action against dark web threats.
Our technology provides upfront, simple-to-navigate insight into…
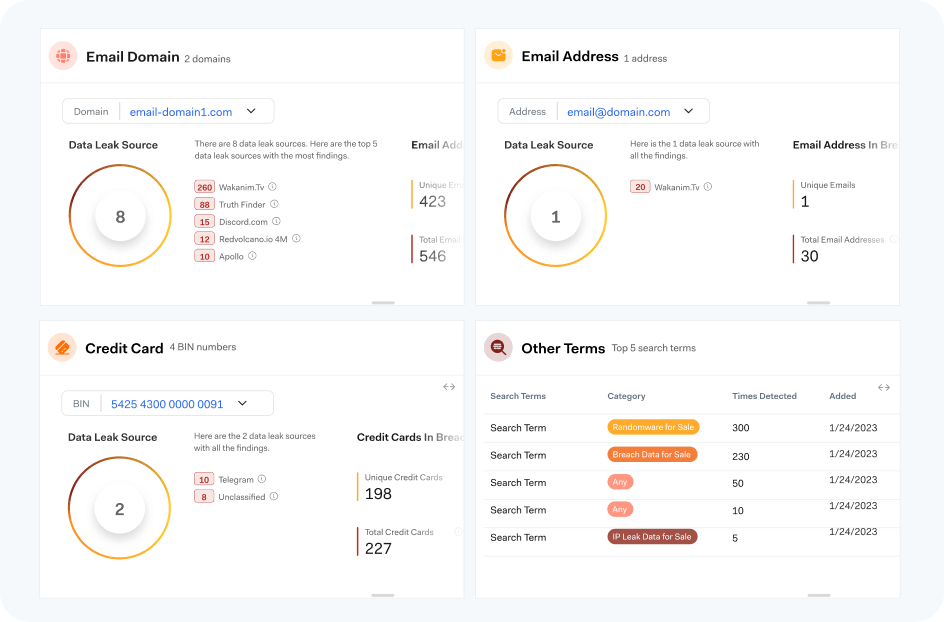
Exposed Business Credentials
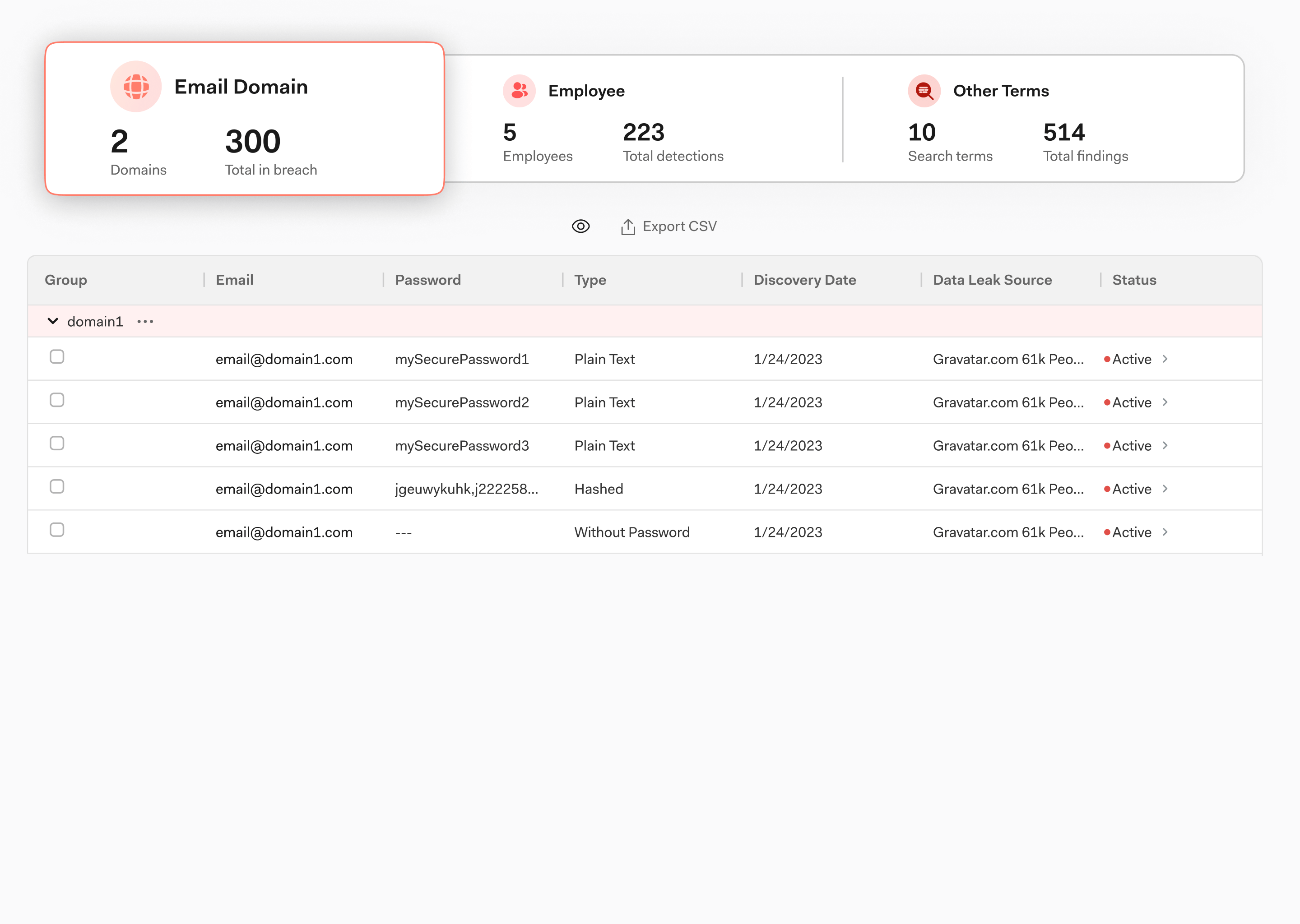
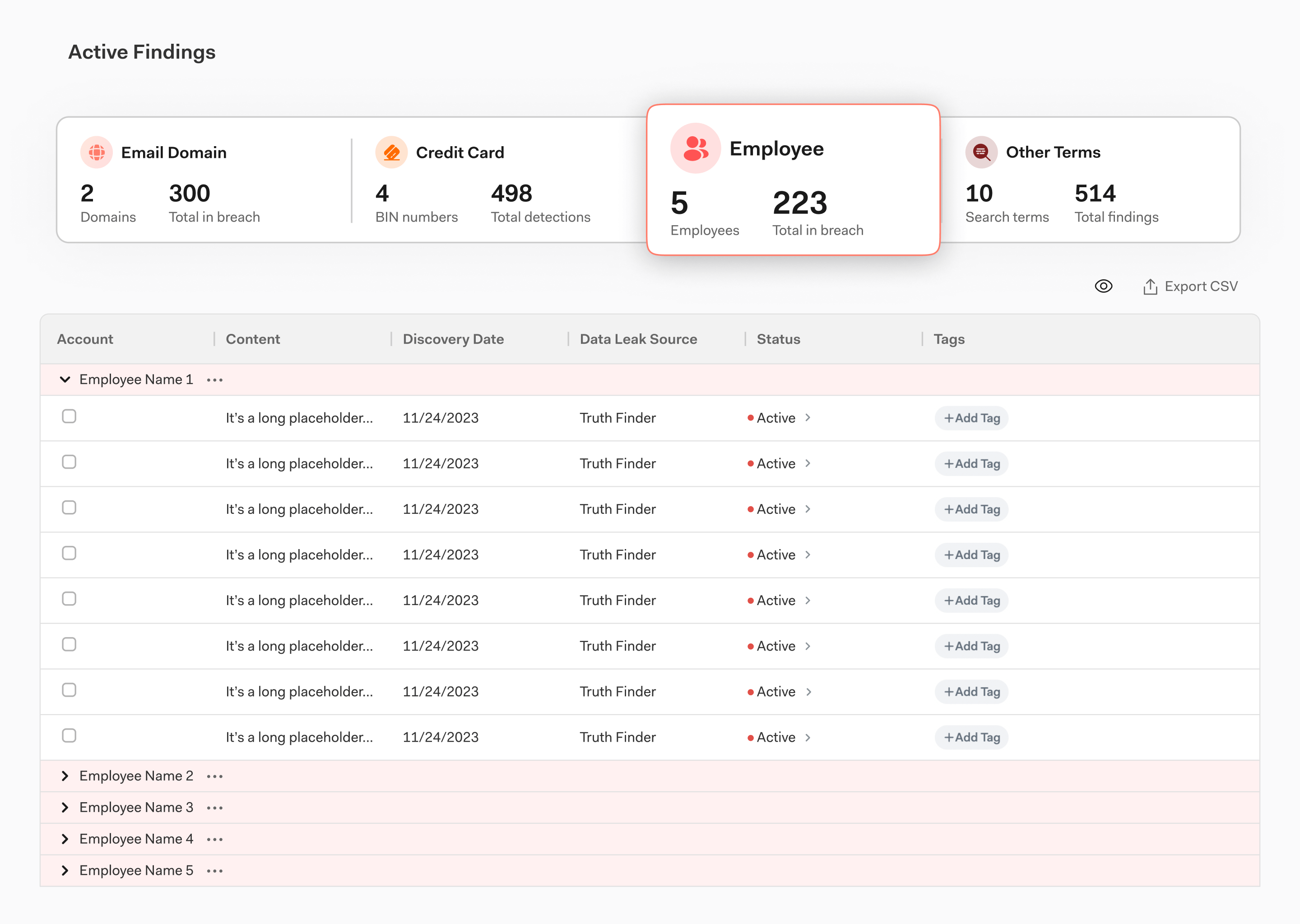
Identify the specific, business-critical credentials exposed on the dark web, including executive account info, employee passwords, and more.
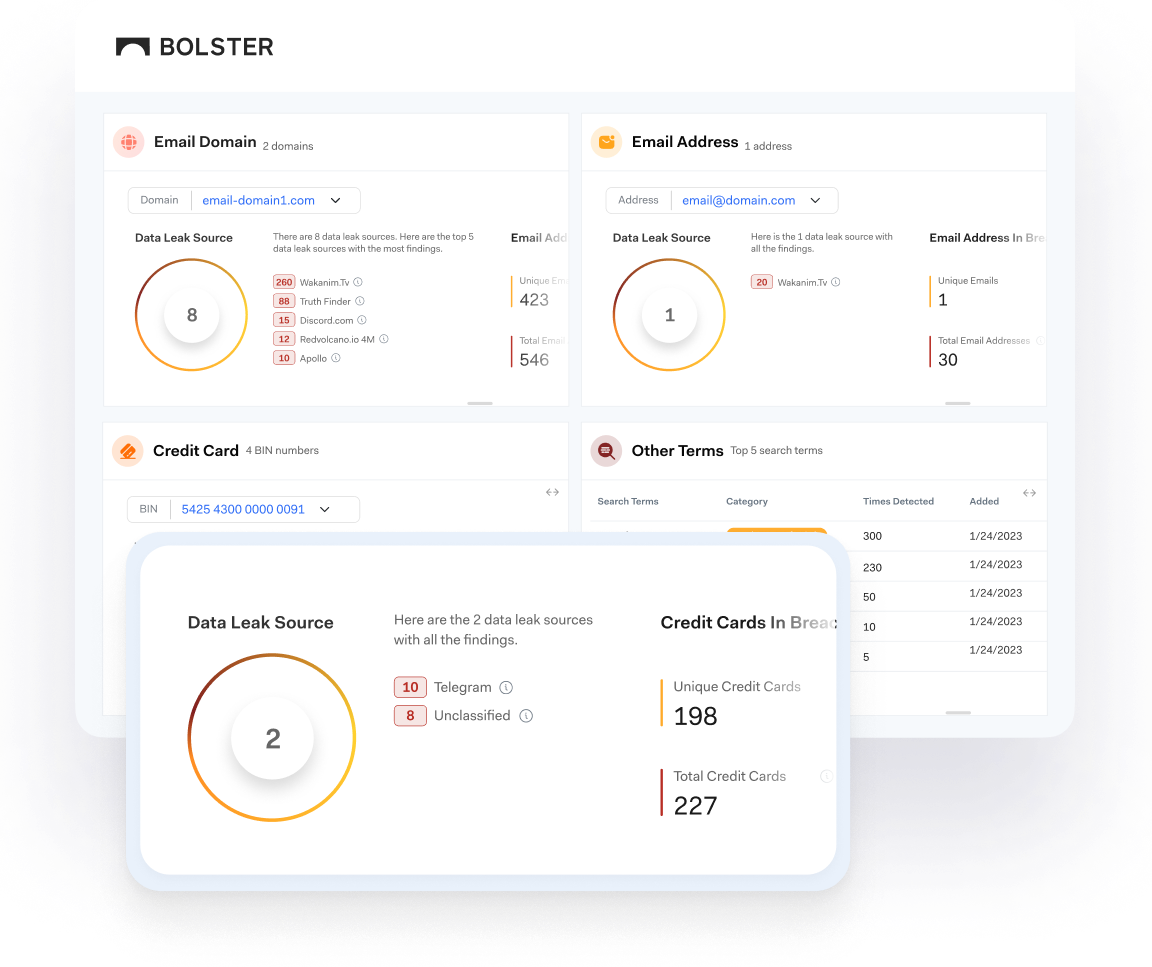
Credit Card Data
Quickly nail down exposed credit card numbers and BIN numbers accessible to criminals on the dark web.
Phishing kits for sale
See what phishing kits exist against your brand at any given moment.
Breach data
Gain visibility into what compromised company data exists on the dark web, including specific credit card numbers, PII, or passwords.

Guide to Dark Web Monitoring
Discover all you need to know to get started understanding dark web threats.

Comprehensive Coverage and Management of Dark Web Channels
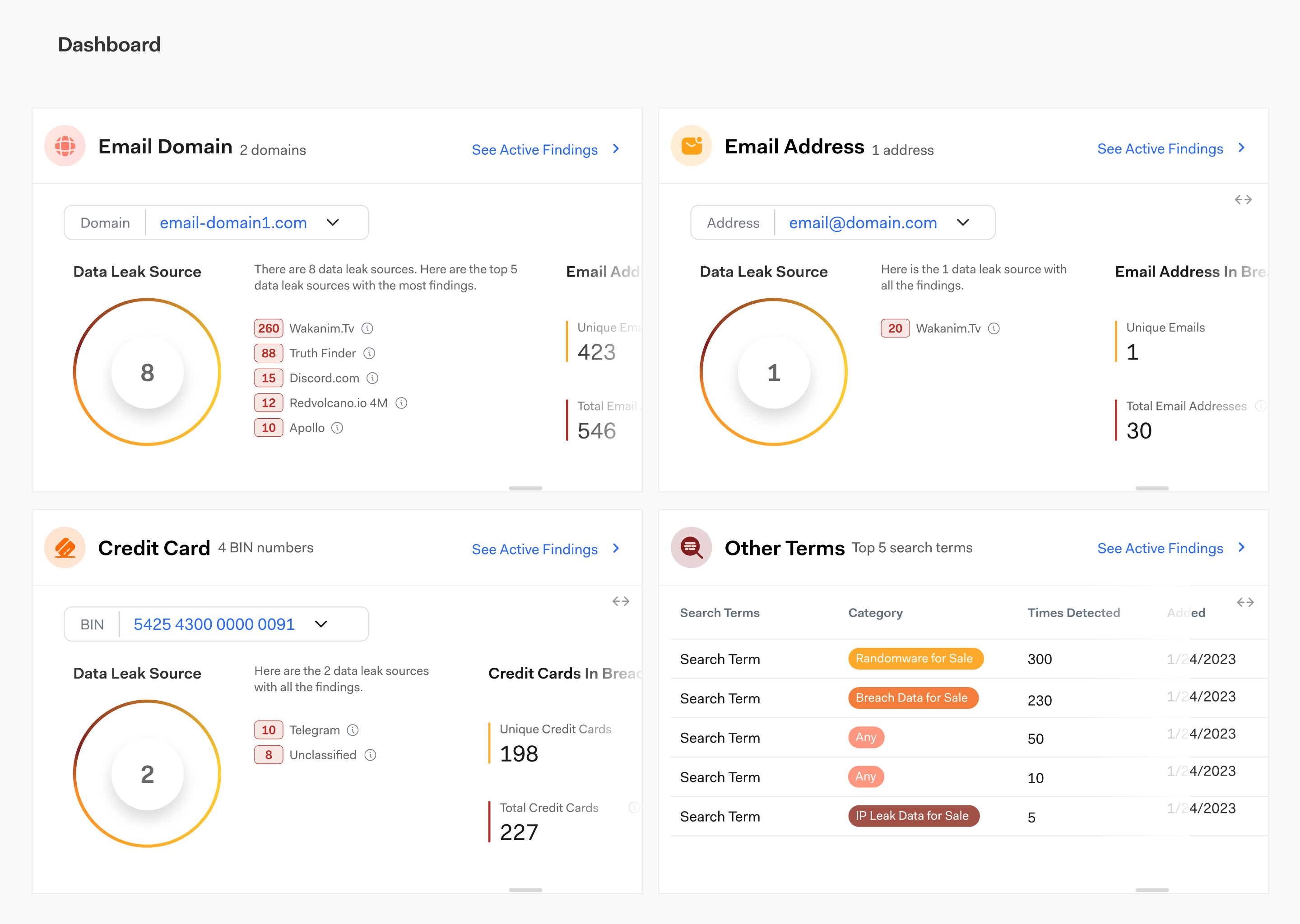
Bolster provides customers with the most expansive dark web scans on the market, simplified into actionable reports summarizing the highest priority risks for your business. With Dark Web Monitoring across four major categories, businesses can trust no stone is left unturned.
132 Monitoring Dark Web Marketplaces
117 Monitored Dark Web Forums
52 Monitored Telegram Channels
46 Monitored Ransomware Services

Guides and Resources
Bolster your digital risk protection program and learn more about industry trends and managing threats.
Navigate Evolving Threats With a Trusted Detection and Exposure Management Tool
Don’t Let Threats Go Unnoticed
Visualize Dark Web Data Exposure Better Than Before
Protect Your Brand Reputation
Bolster’s Dark Web Solution Capabilities
Bolster collects, analyzes, and summarizes data quickly to provide a fast-track to understanding exposed, compromised accounts and business credentials so businesses can make quick decisions.
Expansive coverage
Continuous Scanning
Remediation Workflow
Take Back Control of Your Data With a Fast-Track to Understanding Exposed Credentials
Bolster’s customizable Dark Web Monitoring dashboard and AI scanning technology make managing dark web threats an efficient process for businesses of all sizes.
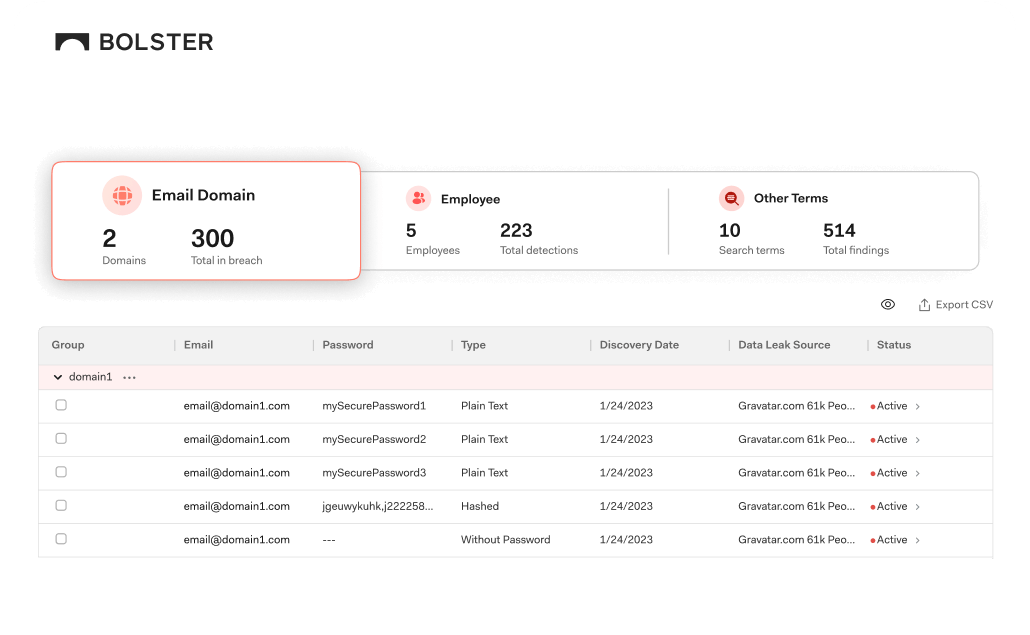
Your Exposed Credentials, Front and Center
Grant your security and threat intel teams quick access to the specific individual or entity exposed and the source of exposure. With immediate access to the exact details as soon as you log in, customers can remediate threats (think executive passwords, email logins, and more) faster than ever before.
Data Sorting and Management of Complex Sources
The breadth of data on the dark web is overwhelming, even for the most experienced security operations teams. The Bolster platform weeds through the log toil for you, merging complex sources and data logs into a simple, customized dashboard based on your business-critical credentials.
Set Up Instant and Curated Responses to Threats
With advanced alerts for granular threats, and access to differentiated playbooks based on your company-specific threat types, your team can quickly remediate dark web threats. Spend less time weeding through data, and more time taking real action to protect your business.
Customization for Your Specific Business Needs
Select which business-critical data to display in customized reports and dashboard layouts that work for your team. With intuitive, risk-prioritized data, your team can stay on top of threats and more-easily connect business-critical assets and entities that may be targeted from a wider Bolster lens.
Ready to get started?
Explore what Bolster AI can do for you with a custom demo for your online business to understand existing online threats and how Bolster can take them down. Contact our sales team for pricing and packages today.
Easy Product Guides
Frequently Asked Questions
What is the dark web?
The dark web refers to a hidden part of the internet that is not accessible through traditional search engines or browsers. It is often used for illicit activities, where users can remain anonymous and transactions can be conducted using cryptocurrencies. There is a great deal of privacy and anonymity that comes with using the dark web compared to traditional websites, which makes it a prime space for malicious actors.
How can the dark web be dangerous for businesses?
The dark web can pose significant dangers to businesses. Criminals operating on the dark web have the ability to access powerful information that can cause considerable harm, including data breaches and financial losses. Here are a few reasons why the dark web can be dangerous for businesses:
**Data Breaches**: The dark web has become a marketplace for leaked and stolen company data. If your organization experiences a data breach, there is a high likelihood that the sensitive information will end up on the dark web. This can lead to reputational damage, regulatory fines, and potential legal consequences.
**Sale of Hacking Tools and Services**: The dark web provides a platform for cybercriminals to sell various hacking tools, malware, and services. These tools can be used by attackers to exploit vulnerabilities in your business’s systems, leading to unauthorized access, data theft, or operational disruptions.
**Stolen Credentials**: Criminals frequently target individuals and businesses, attempting to obtain login credentials and user information. These stolen credentials can then be sold on the dark web, allowing cybercriminals to gain unauthorized access to your company’s systems, networks, or accounts. This can lead to further data breaches, financial fraud, or even identity theft.
**Ransomware Attacks**: The dark web is often used as a platform for ransomware attacks. Cybercriminals can deploy ransomware that encrypts your business’s critical data, demanding payment in exchange for its release. These attacks can result in significant financial losses, operational disruptions, and reputational damage if not mitigated effectively.
Dark web monitoring services, like Bolster’s , play a crucial role in helping businesses detect and respond to threats originating from the dark web.
What is dark web monitoring?
Dark web monitoring is a service that tracks and monitors the dark web for any instances of data breaches or stolen credentials that may affect your business. By monitoring the dark web, you can proactively identify potential security breaches and take measures to protect your sensitive data. Effective dark web monitoring tools find stolen or leaked information, such as compromised passwords, credentials, intellectual property, and other sensitive data being shared and sold among criminals operating on the dark web.
Why does my business need dark web monitoring?
With cyber threats becoming increasingly prevalent, businesses need a proactive approach to cybersecurity. Dark web monitoring is an essential tool for identifying any data breaches or stolen credentials that may affect your business, allowing you to take swift action before any significant damage is done.
What types of threats target businesses on the dark web?
Businesses face a range of threats on the dark web, including the sale of sensitive data, hacking tools for targeted attacks, and ransomware attacks. These threats can lead to severe reputational damage, financial losses, and legal consequences if not detected early on.
How does Bolster’s Dark Web Monitoring work?
Bolster’s dark web monitoring service uses advanced algorithms to scan the dark web for any instances of stolen credentials or data breaches that may impact your business. Our platform aggregates data from multiple sources and analyzes it to provide a comprehensive overview of any threats to your business. Bolster leverages patented machine learning and natural language processing so organizations can not only get an easy-to-use, intuitive, and consumable dashboard, they can also get risk level recommendations and see predict future threats.
Does Bolster provide dark web threat takedown services?
While Bolster’s expansive monitoring and detection technology will identify and track threats that exist on the dark web, we aren’t able to engage with threat actors on the dark web to have your company data removed. Removing data from the dark web is complicated strategy because there is no way to verify whether or not a threat actor has been true to their word in removing that data. In fact, most companies have policies against meeting threat actor demands such as paying for decrypting ransomware.
Instead, Bolster helps you mitigate the risk that you can control by identifying threat data on the dark web, categorizing the threat, and giving your organization actionable insight into how to prevent that dark web data from further exposing your organization to risk of a breach. For example, if we detect a business credit card information is being sold on the dark web, we will give you the BIN numbers and allow your team to address that problem with mitigation strategies such as freezing accounts and/or sending out new credit cards to your impacted consumers.