Executive Impersonations and Fake Accounts
Protect Your Brand, Employees, and Customers from Fictitious Executive Accounts
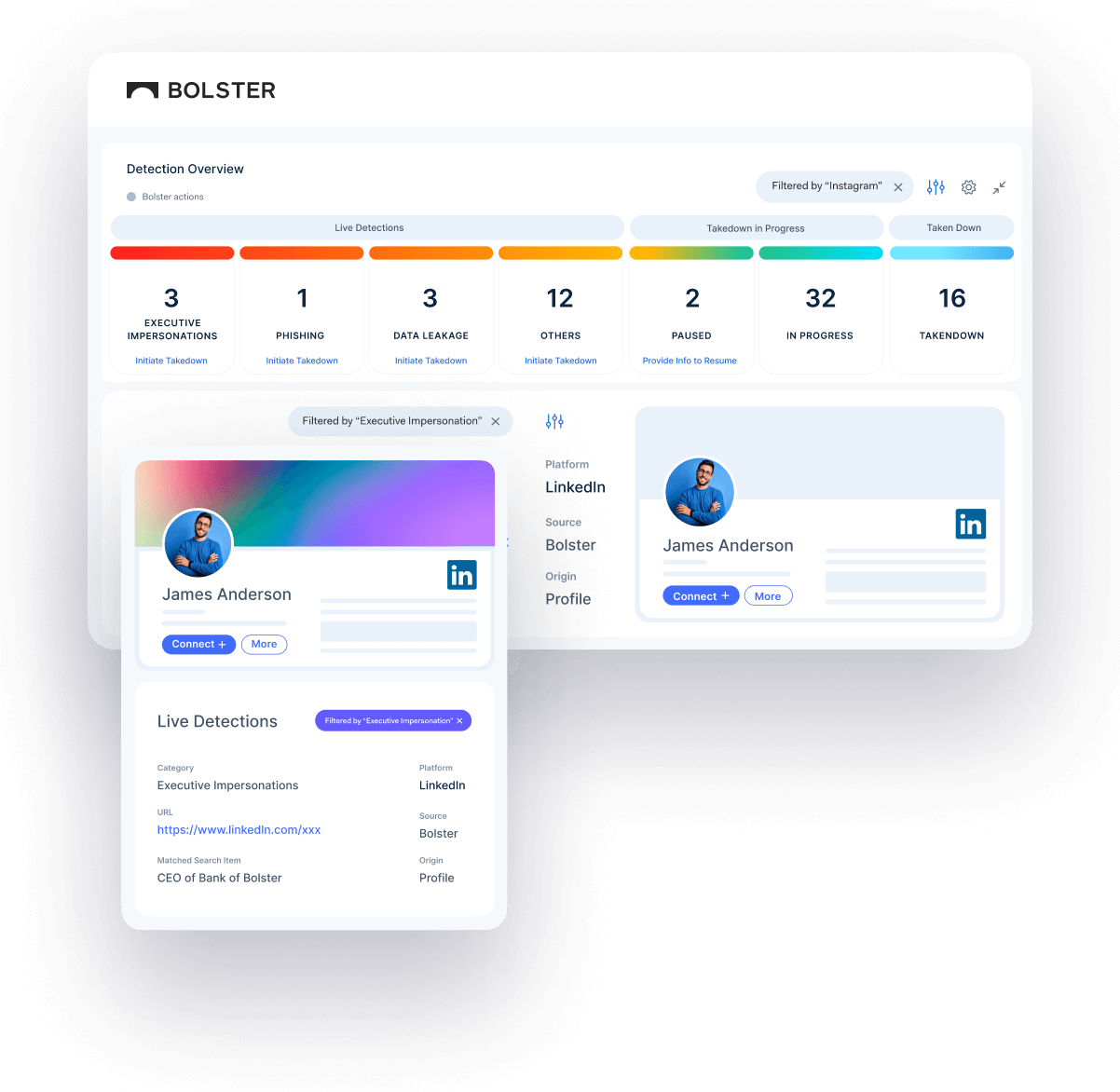
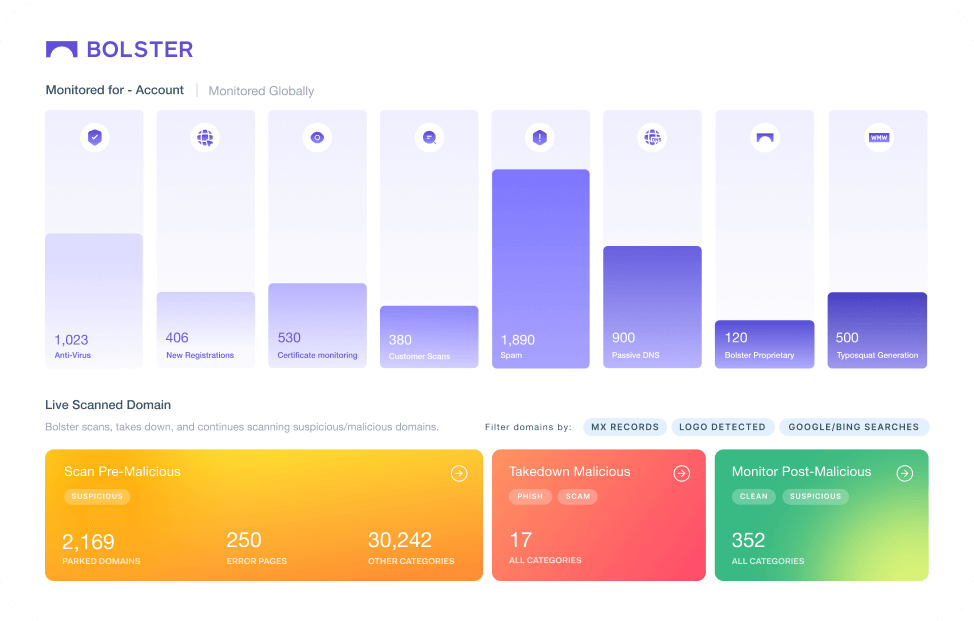
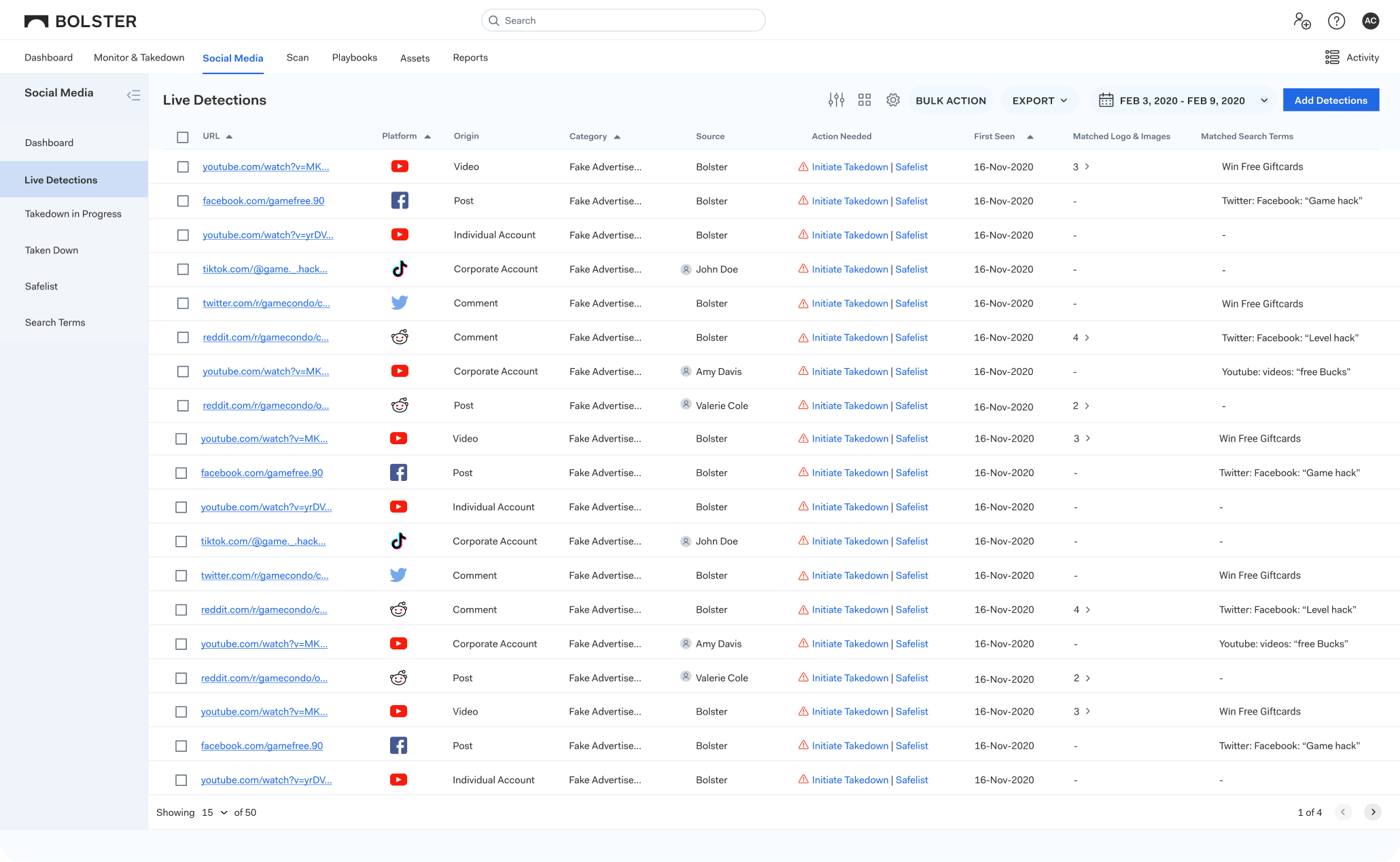
Automatically Weed Through the Malicious Accounts & Protect Your Employee PII Data
Social media has become a business tool for executives but is often subject to phishing scams for financial gain.
Hackers also target potential employees with fake recruitment campaigns, including fraudulent job posts and interview processes that damage your legitimate brand reputation; whatever it takes to get PII.
Businesses need a trusted tool to identify instances of executive impersonation scams and remove threats before reputational and financial damage is done.
Discover a solution that works with your business to automatically scan for executive impersonation accounts, and remove threats before damage is done.
Maintain Control of Executive Profiles With the Right Technology
Bolster’s Executive Impersonation technology highlights efficiency for your business. With industry-leading machine learning technology and language learning AI to work directly with social media platforms, our platform identifies threats and requests takedowns without any effort from your business.
Works fast
Analyzes accounts with a human eye, but machine-level speed.
Intelligent
Detects misuse of your executive’s details even if specific names or images aren’t used.
Easy to decipher
Provides your team with images of what we see, giving detailed access to threat types.
Leaves no gaps
Detect activity on over 18+ popular social media channels including Telegram

Our Numbers Speak For Themselves
Increase authorization rates, optimize your checkout conversion, and offer local payment methods in every market.
99.999% Accuracy
60 Seconds
98% Takedowns
278% ROI

Guides and Resources
Bolster your digital risk protection program and learn more about industry trends and managing threats.
Implement the Technology that Works With You, Customized to Your Business Needs
Detect executive impersonations across the board
Leave the takedowns to us
Dedicated support team
The Benefits of Using Bolster’s Executive Impersonation Technology
Increase authorization rates, optimize your checkout conversion, and offer local payment methods in every market.
Strengthen your toolbox without breaking the bank
Bolster can fit seamlessly into your digital risk protection program, working alongside other tools, or as the sole threat detection software. Our impersonation detection capabilities take the pressure off your internal team, freeing up manpower resources.
Protect your brand’s reputation
Reacting to events after they happen isn’t enough; your business must proactively prevent fake online accounts and malicious interactions. Promote your status as a trusted business partner by ensuring all uses of your brand online are legitimate.
Protect employee data and security
With the right monitoring technology tools on your side, your employee data and company credentials will only be accessed by those meant to see them. Maintain top talent when you effectively defend against impersonation scams.
Reducing manual hours for your team
Using continuous monitoring technology to prevent time-consuming investigations, damage control, and potential legal or regulatory repercussions. With Bolster’s ongoing eyes, your team can focus their work hours on other priorities.
Ready to get started?
Explore what Bolster can do for you with a custom demo for your online business to understand existing online threats and how Bolster can take them down. Contact our sales team for pricing and packages today.
Get 24/7 Support
Start Your Integration
Frequently Asked Questions
How does an executive impersonation attack work?
An executive impersonation attack often involves the impersonator using social engineering tactics to trick the victim (usually company employees, customers, or partners) into divulging sensitive information or carrying out unauthorized actions. These tactics may include masquerading as a high-level executive through a fake email address or social media account, sending urgent or unexpected requests that require the victim to respond quickly, or using intimidation or other forms of pressure to compel the victim to comply with their requests.
By impersonating an executive, attackers can gain access to sensitive information, authorize fraudulent transactions, or compromise company systems in a variety of ways.
An executive impersonation attack often involves the impersonator using social engineering tactics to trick the victim (usually company employees, customers, or partners) into divulging sensitive information or carrying out unauthorized actions. These tactics may include masquerading as a high-level executive through a fake email address or social media account, sending urgent or unexpected requests that require the victim to respond quickly, or using intimidation or other forms of pressure to compel the victim to comply with their requests.
By impersonating an executive, attackers can gain access to sensitive information, authorize fraudulent transactions, or compromise company systems in a variety of ways.
What is an impersonation attack?
Executive impersonation refers to the act of pretending to be a high-ranking executive of a company or organization in order to deceive others. This can involve using the executive’s name, email address, pictures, or even creating fake social media accounts to carry out phishing or fraudulent activities.
How can you prevent an executive impersonation attack?
Businesses can prevent executive impersonation attacks in many ways, including by implementing multi-factor authentication, educating employees about the tactics used by attackers, establishing clear company policies for handling sensitive information, monitoring company accounts and systems for suspicious activity, and using email authentication protocols to prevent email spoofing. These measures can help protect businesses from the potential consequences of executive impersonation attacks.
How are fake accounts created?
Fake accounts can be created in various ways, including the use of stolen personal information, automated bots, or social engineering techniques. Attackers may gather personal details from data breaches, social media platforms, or other sources and use this information to create realistic-looking profiles. They also might use a person’s publicly available information, like their name and image, to create an account mimicking them,
Automated bots can also be used to generate a large number of fake accounts quickly.
Additionally, attackers may employ social engineering tactics, such as phishing emails or deceptive websites, to trick individuals into providing their personal information, which can then be used to create fake accounts.
What kind of cyberattacks does Digital Risk Protection protect my organization from?
Preventing the creation of fake accounts can be challenging, but there are some measures that organizations can take to reduce the risk of executive impersonation attacks.
DRPS scans the entire internet to protect your company’s identity as you grow and become an ever-more-tempting target for attackers.
One crucial step is to implement multi-factor authentication, which can help prevent attackers from gaining access to sensitive information or systems even if they have obtained login credentials. Additionally, security teams can educate executives and other employees about how attackers use social engineering tactics to impersonate them and provide them with clear company policies for handling sensitive information.
Finally, monitoring or flagging for suspicious activity on company accounts and systems can help detect and prevent fake accounts from being successfully created or used in an attack.
Should I use technology to combat executive impersonation attacks?
Using technology to combat executive impersonation attacks is a crucial aspect of protecting executives. Implementing advanced email security solutions, such as email authentication protocols like DMARC, SPF, and DKIM, can help verify the authenticity of incoming emails and prevent spoofing or phishing attempts.
In addition, employing email filtering and spam detection systems can help identify and block suspicious or malicious emails.
Advanced threat detection technology like Bolster, as well as security awareness training for executives can also aid in identifying and mitigating potential threats.