Phishing and scam websites often use SSL certificates to create a false sense of trust and security for their victims. By displaying the padlock icon and the “https” protocol in the URL, these websites try to appear legitimate and secure. However, SSL certificates alone do not guarantee a website’s safety or legitimacy.
Anyone can obtain an SSL certificate for free or at a low cost, including many phishing websites. A website may display a the padlock icon and “https” in its URL but it doesn’t necessarily mean that it is safe or trustworthy.
Using SSL certificate is a double edge sword for threat actors. On one end, SSL certificates can help dupe victims. On the other end, if targeted organizations are monitoring a newly-issued SSL certificates stream, then phishing campaigns can be identified early on and mitigated efficiently.
Why Monitor SSL Certificates
Brands can leverage SSL certificate monitoring capabilities to detect phishing and typosquatting websites. Monitoring for SSL certificates revolves around accurate detection of certificates that are issued to suspicious or unusual domain names, specifically domains that closely resemble the legitimate brand’s name. By proactively monitoring SSL certificates, organizations can detect these malicious websites early on, and take swift action to protect their brand and customers from potential harm.
When we look for any commonly targeted brand names in the real-time SSL certificate issuance data, phishing trends quickly emerge.
Organizations can identify SSL certificates issued to typosquatting domains almost immediately after they’re live, especially if it’s a popular brand often targeted by fraudsters.
In the example below, a SSL monitoring tool was able to detect same day issued SSL certificates and upon closer inspection, the certificate belonged to a spoofed site:

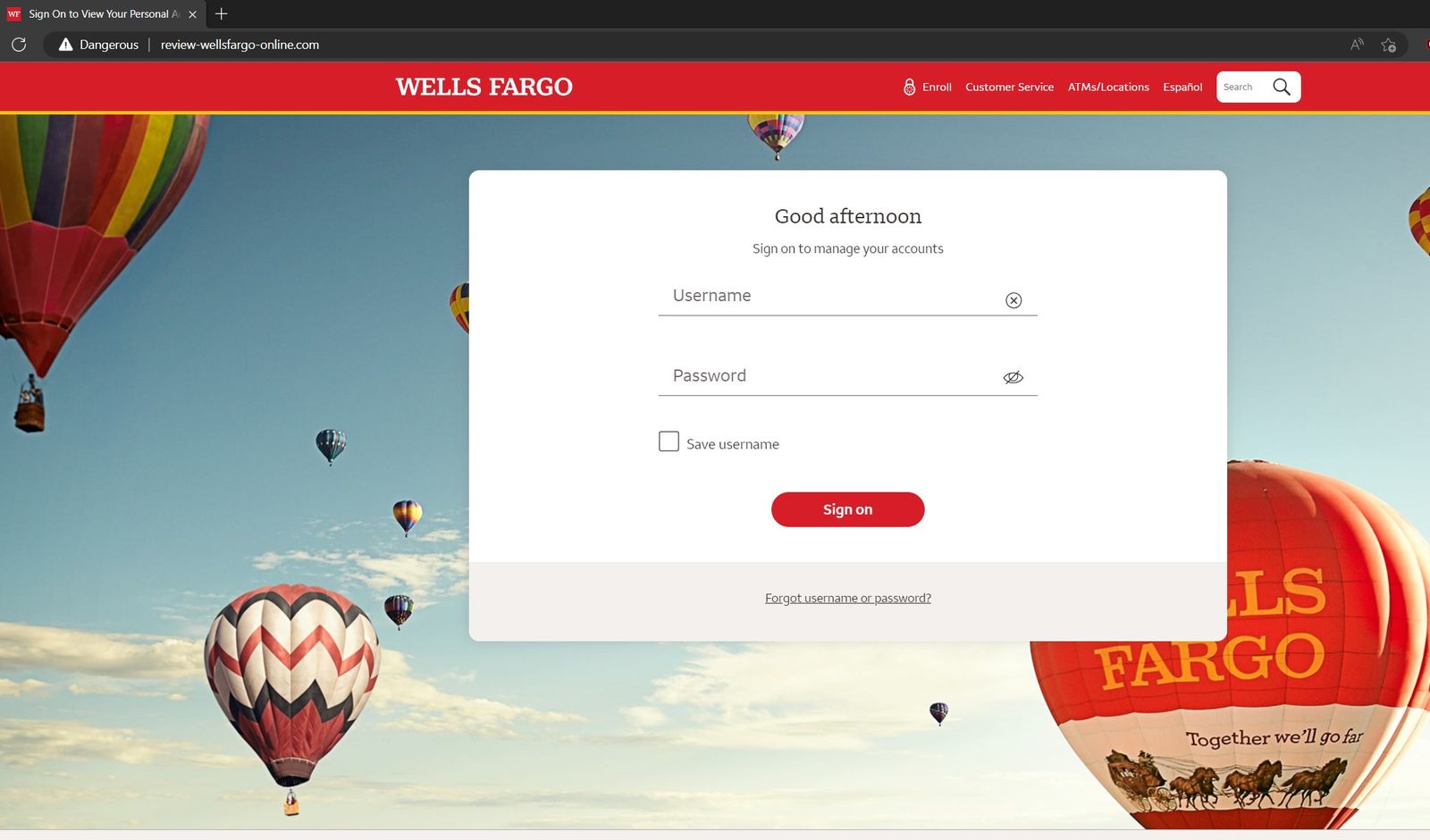
Key Fields For Identifying SSL Certificate Scams
Common Name
The Common Name (CN) in an SSL certificate refers to the server’s name or Fully Qualified Domain Name (FQDN) being protected. It is specified by the commonName field in the X.509 certificate and allows for wildcard entries covering a domain and all of its’ subdomains.
Subject Alternative Names
The Subject Alternative Name (SAN) field allows for the specification of additional host names (such as sites, IP addresses, and common names) to be protected by a single SSL certificate, such as a Multi-Domain (SAN) certificate.
While this extension was a part of the X.509 certificate standard before 1999, it wasn’t commonly used until the launch of Microsoft Exchange Server 2007, which simplified server configurations by utilizing Subject Alternative Names. Today, SANs are widely used for securing multiple sites (names) across different domains or subdomains.
Threat actors sometimes make the mistake of adding all the domains and subdomains that are included in their phishing campaign to the same SSL certificate’s SAN, making it easier for security tools to detect and mitigate the threat.
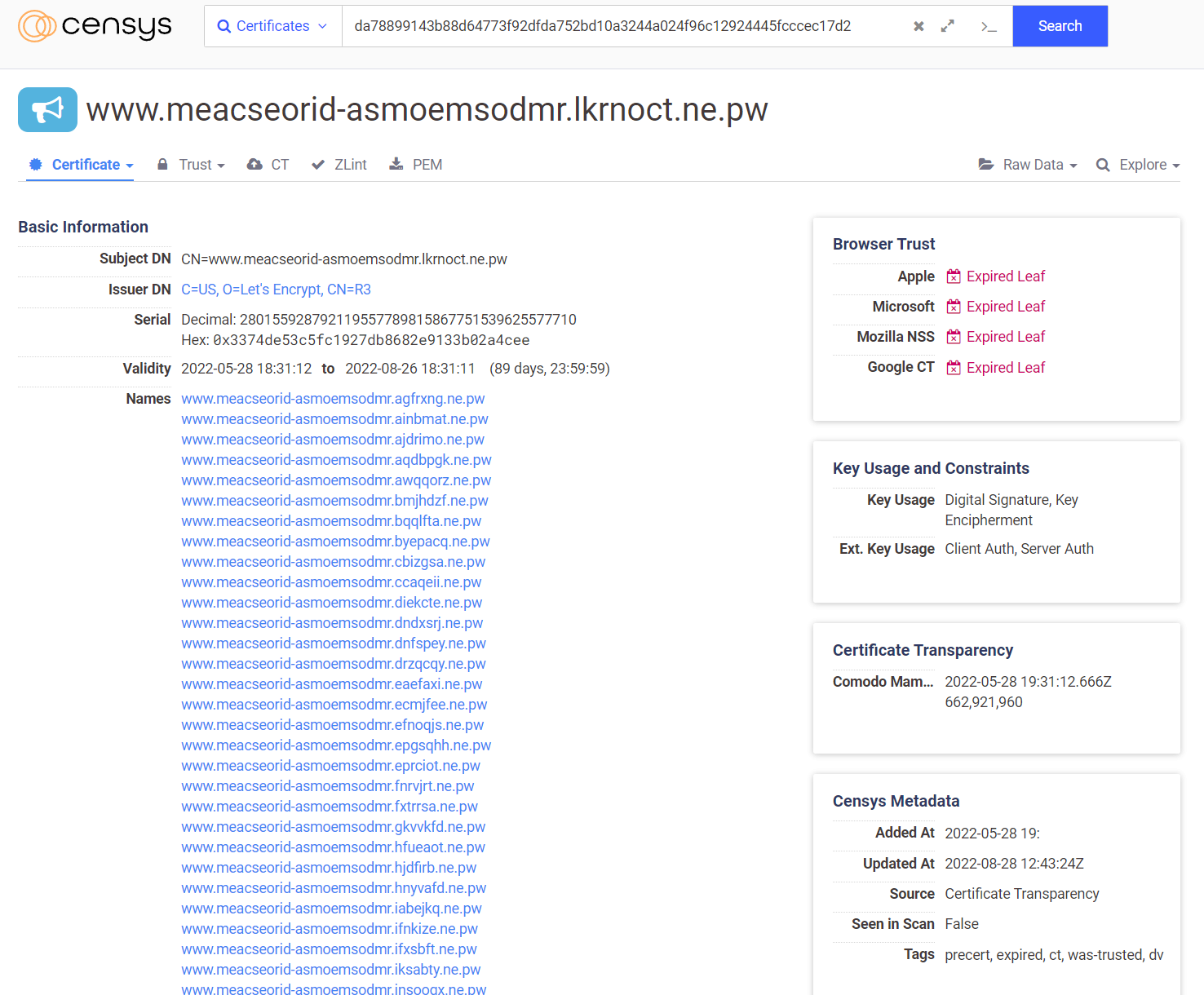
For example, the SSL certificate for the domain www.meacseorid-asmoemsodmr.lkrnoct.ne.pw includes all other domains used in the phishing campaign as DNS Alternative names. This campaign targeted Mastercard Japan on all of the following domains:
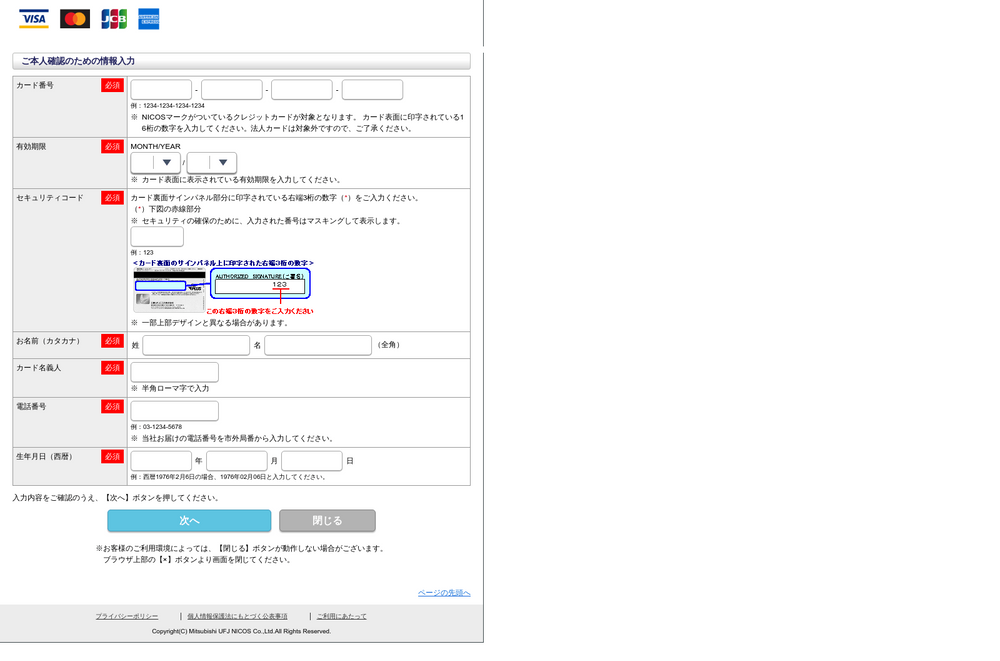
Below is another example of an SSL certificate with multiple subdomains in the Subject Alternative Name field, where each subdomain targets a different crypto project:

How to Monitor SSL Certificates
Effectively monitoring SSL certificates to detect fraudulent domains is difficult for an organization to manage internally. In our rapidly expanding digital economy where attackers are finding new ways to dupe victims online, the best way to actively detect and take down malicious sites is through automation. Here are a few options to consider when monitoring for fake SSL certificates:
Certstream
Certstream is a free, publicly available stream of SSL certificates populated as they’re being issued in real-time. Certstream collects data from multiple certificate transparency logs and offers an Application Programming Interface (API) for streaming the data. Certstream is frequently used for threat intelligence, helping organizations detect and prevent cyberattacks.
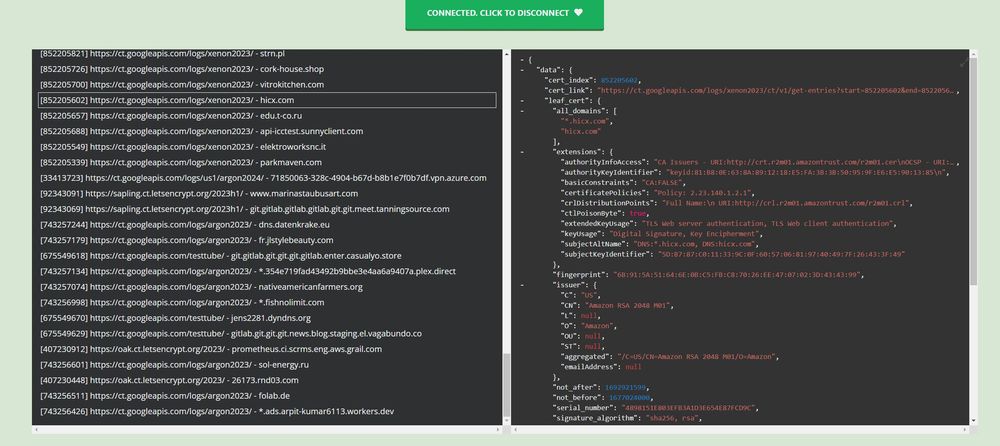
Censys SSL Search
Censys provides one of the most robust SSL search experiences in the market. Along with keyword and wildcard searching, the Censys platform offers the ability to search for SSL certificates based on specific issuers and date ranges.
Censys does, however, have a limit on the number of free queries per month.
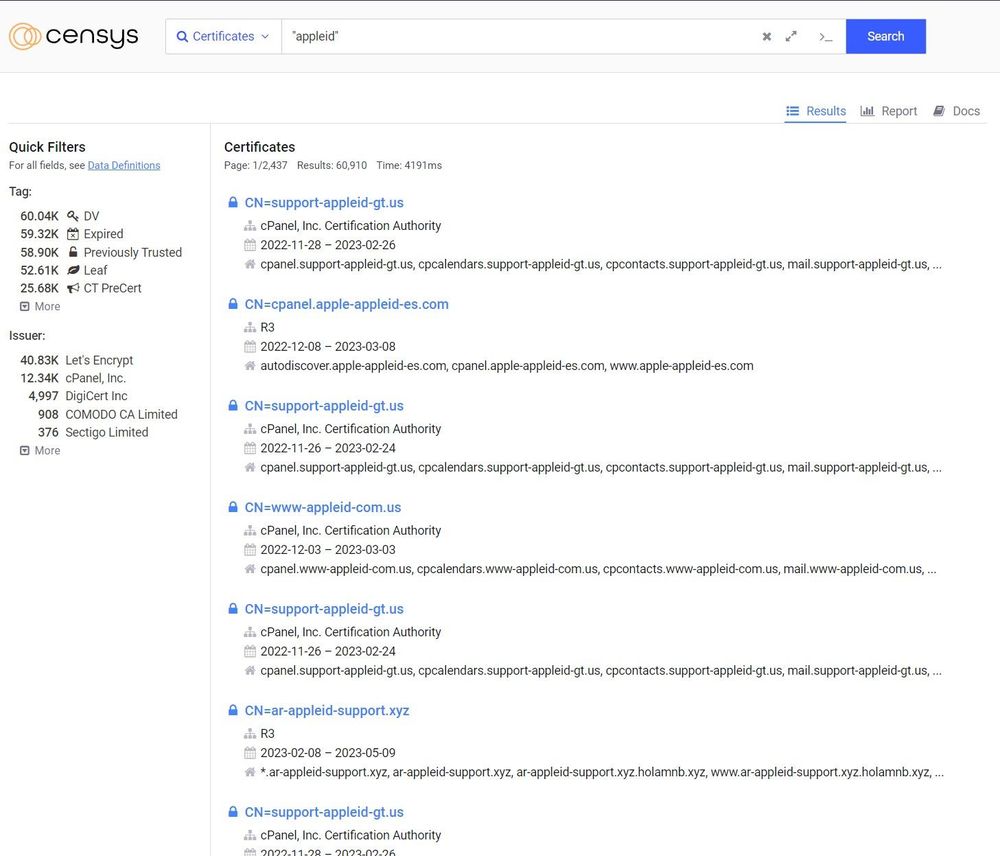
Crt.sh
Crt.sh is a web-based tool that allows users to search and analyze SSL/TLS certificates for free. It is maintained by a group of volunteers and offers a comprehensive database of certificate transparency logs from multiple certificate authorities. With crt.sh, users can search for SSL/TLS certificates associated with a specific domain or subdomain, track changes in certificate lifecycle, and access advanced search options such as wildcard searches and certificate fingerprints.
The free tool has been known to experience downtime and timeout issues, and response time can be slow. Despite these limitations, crt.sh is a valuable resource for security teams seeking to monitor certificate issuances and detect fraudulent certificates.
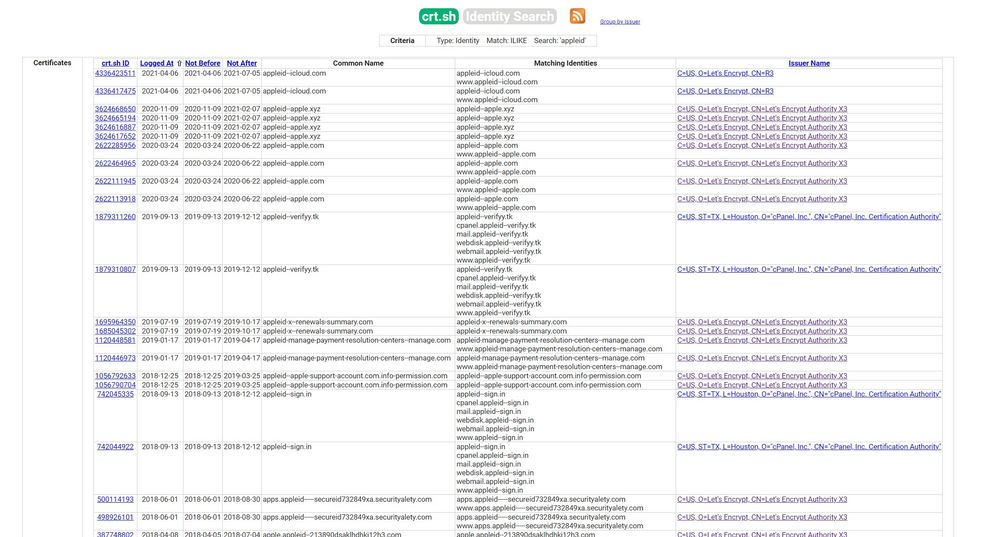
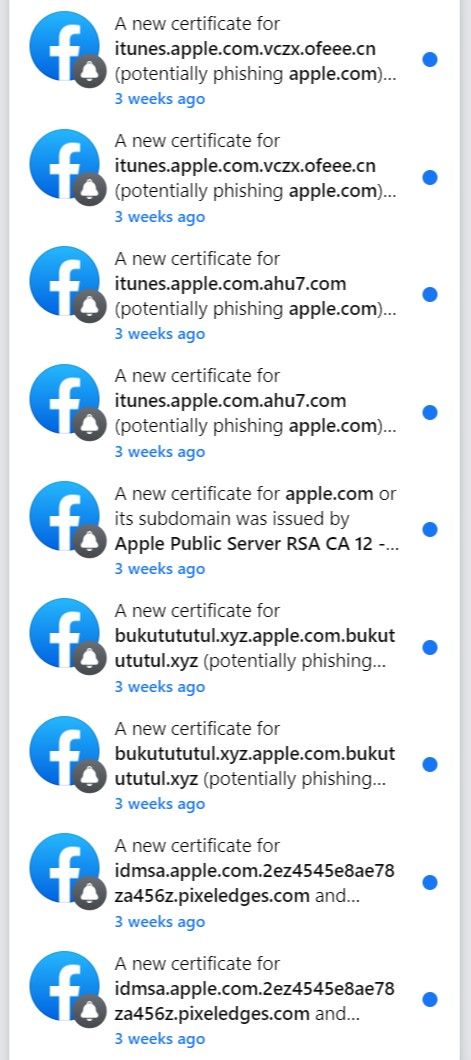
Facebook Transparency Monitoring
Facebook Certificate Transparency is a free and open framework that logs, audits, and monitors publicly-trusted SSL certificates on the internet. With this tool, users can search for certificates issued for a specific domain and subscribe to notifications from Facebook regarding new certificates and potential phishing attacks.
The platform can be set up to provide email and Facebook notifications, alerting users when a suspected phishing, homograph, or typosquatting variant of their domain is seen in issued SSL certificates. The alerts are near real-time, however, the platform only supports lookups by domains and not keywords with wildcards.
Certspotter by SSL mate
SSLmate provides a free certificate data API called CertSpotter, which provides up to 100 queries per hour. However, the free version does not support keyword or wildcard searches, and only provides results related to a specific domain.
SSLMate also offers a paid, real-time firehose option for more advanced users.
Bolster Platform
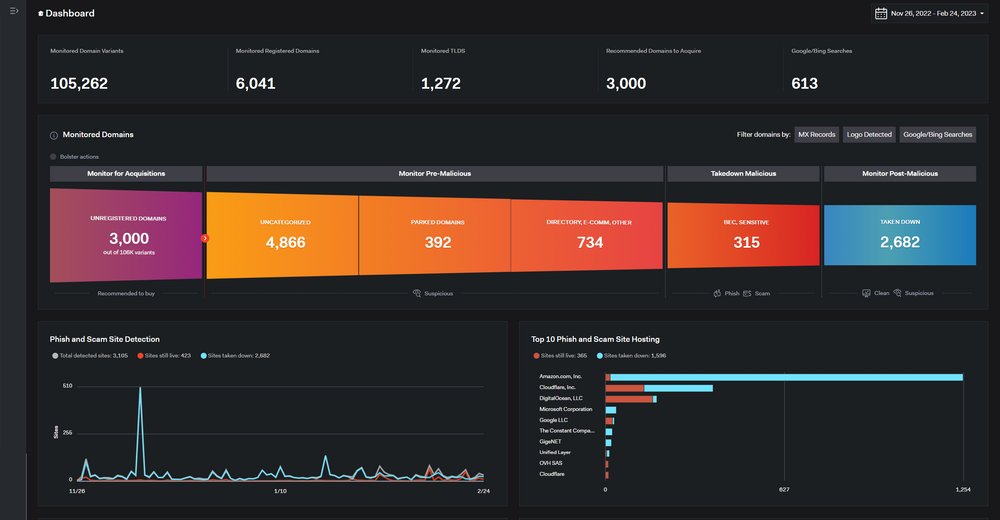
Bolster continuously monitors SSL certificates, including historical and real-time certificate streams, to detect potential typosquatting, phishing domains and malicious domains. With the ability to scan millions of domains from SSL certificates, newly registered domains, and subdomains, Bolster is able to identify phishing attempts, scams, and brand impersonation in near real time, and offers takedown services to act fast when threats are detected.
Unlike the aforementioned SSL monitoring tools, Bolster is the only platform that can not only detect spoofed sites using SSL certificates but take them down in matter of minutes. Bolster’s dashboard also offers a seamless, intuitive experience to track pre-malicious and post-malicious site activity.
Get your free trial for Bolster Platform here
Supporting Links
To get started monitoring your network, and protecting your organization and customers from falling victim to SSL Certificate scams, request a demo of the Bolster platform.









