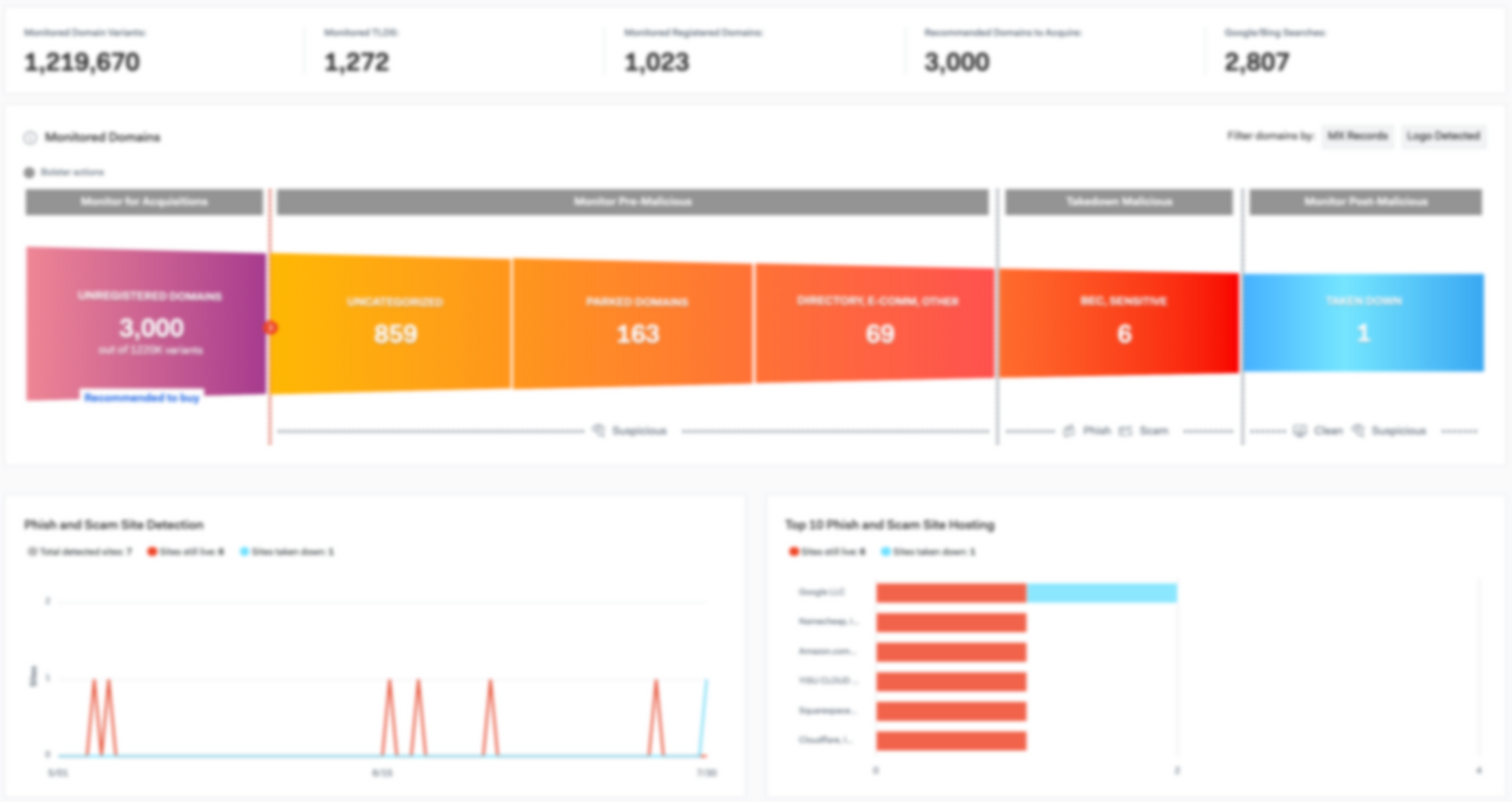
Microsoft recently secured a court order to takedown ‘homoglyph’ domains that impersonate one of their brands. In a statement they released on July 19, they said that these imposter domains were targeting Office 365 customers. This court order is a huge win! Not just for Microsoft, but the entire cybersecurity industry.
In this blog, we will take a look at what homoglyph domains are, how are they are related to the problem of typosquatting before jumping into how you can protect your brand from these attacks.
What are homoglyph domains?
Homoglyph domains look very similar to the brand’s legitimate domain and are hard to tell apart. For example, Bolster’s legitimate domain is bolster[.]ai. If we replace the ‘o’ with ‘0’ (zero), it is very hard to spot the difference. Similarly, we can generate any number of combinations.
Legitimate Domain: bolster[.]ai
Replacing ‘o’ with the number zero: b0lster[.]ai
Replacing ‘o’ with ‘ò’: bòlster[.]ai
Replacing ‘l’ with the number one: bo1ster[.]ai
The problem of typosquatting
Anyone can register the domains we showed in the above example and this could include attackers with malicious intent.
In a homoglyph attack, the attackers register these domains and start using them for malicious purposes. Homoglyph attacks are a part of a larger group of cybersecurity threats called the typosquatting attacks. The problem of typosquatting has been ever-existent in the world of online fraud. We have seen almost every well-known brand targeted by typosquatting attacks. The reason – these domains are easy to register and effective at deceiving users.
Recently the San Diego Hospital was hit by a similar attack. The attacker created phishing pages on typosquatting domains and tricked the staff to enter their login credentials. This led to theft of financial and medical information of the patients.
Attackers can use typosquatting domains to host a wide variety of scams. Based on the data we collected, we identified three groups a typosquatting domain can be a threat to – customers, employees, and vendors. Here are the most prolific types of scams hosted on typosquatting domains:
- BEC (Business Email Compromise): Attackers register MX Records on typosquatting domains & start sending out email impersonating an executive/ employee of the brand. They try and deceive employees into transferring money into their accounts. Every brand needs to monitor active MX Records on their typosquatting domains along with their active typosquats. Target Group: Employees & Vendors
- Phishing pages: This is the most common threat hosted on typosquatting domains. These phishing attacks can quickly transcribe into BEC scams once the attacker has access to the target’s account. Target Group: Customers, employees & vendors
- Customer Support/ Tech Support scams: Fake customer support/ tech support pages not only affect the brand financially but also cause a loss in reputation. Target Group: Customers
Possible ways to mitigate the risk from active typosquatting domains
As a brand, you can take steps on your end to mitigate the risk from typosquatting domains. We listed them below:
- Proactively generate typosquats and monitor them for DNS (Both A record and MX record) changes continually.
- Report malicious typosquats to global blocklists and them to your SIEM/ SOAR platforms
- Defensively acquire high-risk typosquatting domains
- If a typosquatting domain is being used to host phishing/ scam, take them down via hosting provider and domain registrar
- Notify your partners and suppliers of these high-risk typosquatting domains and active MX records
Current solutions for tackling this problem
Almost all the solutions in the market currently are reactive. Most of the solutions start taking action against a typosquatting domain after a cybersecurity incident. Here is how the process looks like:
- Cybersecurity incident on a typosquatting domain
- The Security operations team starts investigating the incident
- Involves the legal team for a takedown
- The domain in question gets added to blocklists
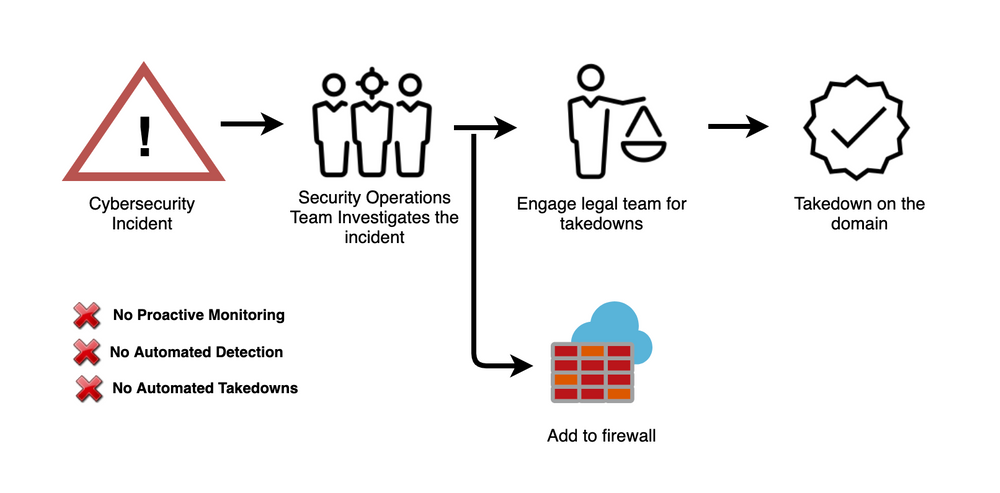
The problem with this approach is that the damage is already done and your brand is still not protected against future typosquatting threats.
Some solutions offer checking typosquatting variants generated by open-source tools like dnstwist. This is what we call a ‘point-in-time’ approach. It cannot monitor active typosquatting domains or mx-records continually over a period of time.
Tackling typosquatting at Bolster
At Bolster, we proactively monitor active typosquatting domains and active MX records for a brand’s internet domains. This process involves generating possible combinations of typosquats, resolving for A/ MX records, understanding the content on each typosquatting domain, and reporting malicious domains for a takedown.
Generating & resolving typosquatting domains
For every brand’s domain, we generate millions of typosquatting variants (or domains). We perform DNS resolutions on all these domains. We consider typosquatting domains with an existing A record and/ or an MX record to be active.
For each of the active domains:
- We launch a headless browser
- Resolve the domain
- Extract the content on the domain, including DOM of the webpage, natural language text, a screenshot of the webpage.
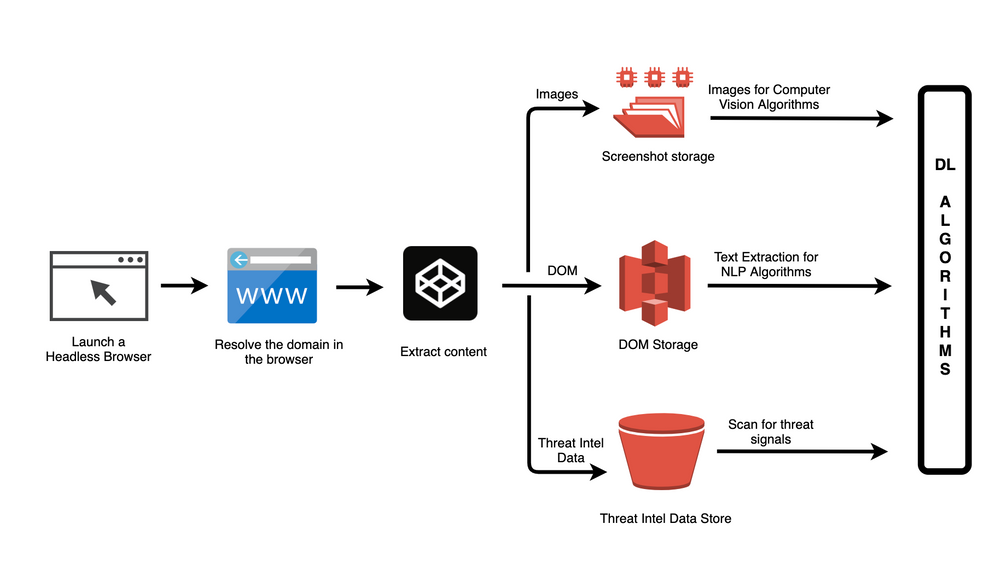
This information is passed onto the next stage of the process – Understanding the content.
Understanding the content on a typosquatting domain
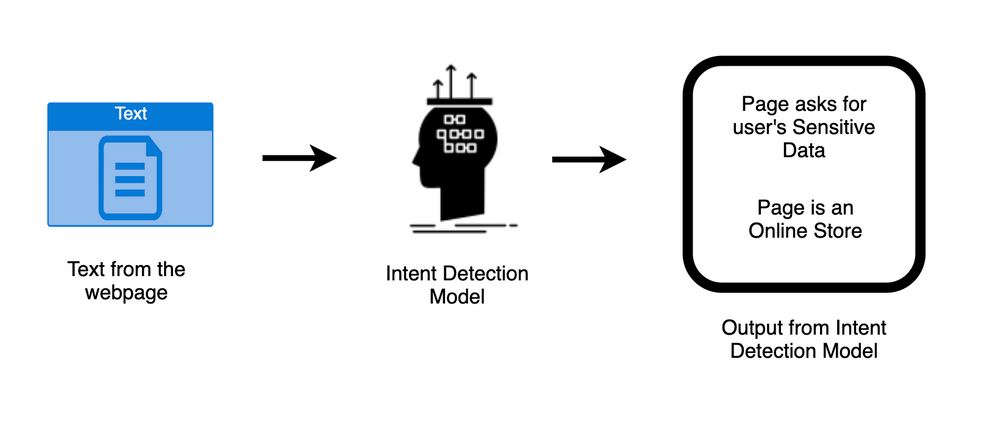
Once we have the required content from the webpage, our machine learning algorithms come into play. These algorithms help us understand the intent of the webpage and assign a risk score to each active typosquatting domain.
The algorithm that detects intent on a webpage uses natural language processing and deep learning. It takes in text from the webpage and determines whether the webpage is asking for sensitive information like login credentials/ credit card details or luring the user into an elaborate gift card scam. Currently, our algorithm can detect 25 such intents on a webpage.
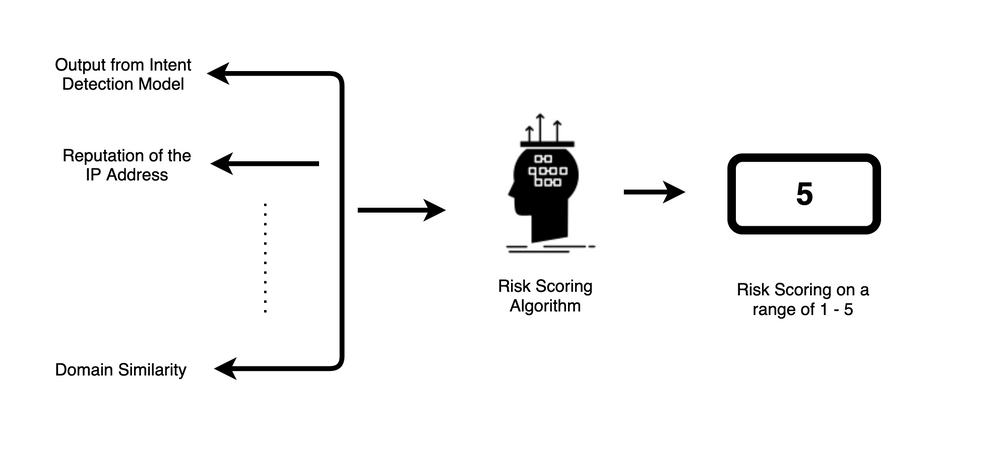
Our risk scoring algorithm is an effort to help brands prioritize their efforts on active typosquatting domains. For instance, let’s consider there are 1000 active typosquatting domains potentially targeting your brand’s internet domain. If two of them were hosting phishing targeting your brand, ten others were hosting tech support scams, and the rest were newly registered and don’t host any content yet. You would want to know about domains hosting phishing and tech support scams first.
Our risk scoring algorithm considers these phishing/ tech support domains as high-risk to the brand. It assigns a risk score on a scale of 1 – 5 to each domain, with 5 being the highest risk. The algorithm takes several threat signals into consideration including the intent of the webpage, and the number of past phishing sites hosted on the resolving IP of the typosquatting domain along with others.
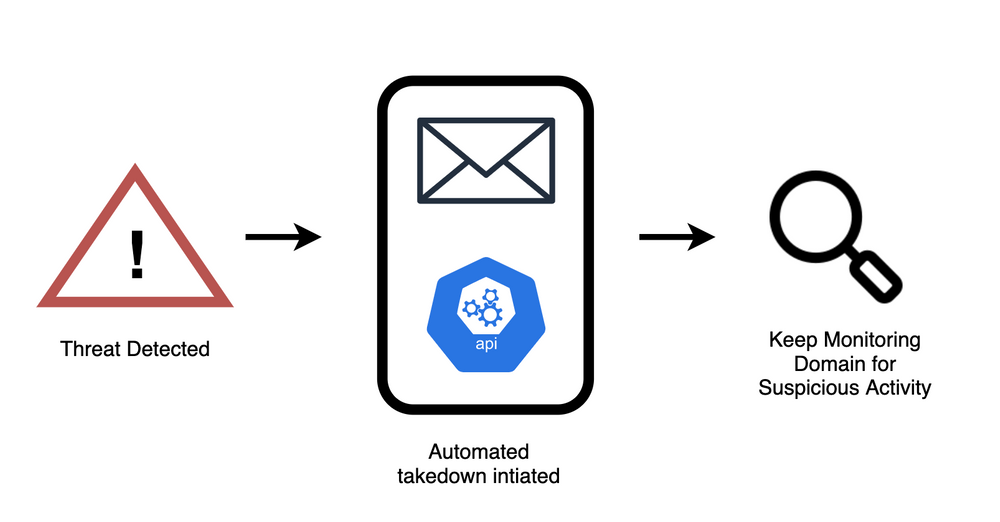
Taking the bad ones down
When we resolve a typosquatting domain in the headless browser, we also extract the information regarding the registrar and hosting provider. We use this information to send out automated takedowns as soon as we see a phishing or scam page hosted on the domain. This reduces the amount of time a brand’s security operations team spends on investigating the domain and the legal team spends on taking it down.
Our system also monitors domains that have been taken down to warn us if they come back up.
Repeating the process
This process of generating, detecting & taking down bad ones is continual and automated. We also provide easy integration into SIEM/ SOAR platforms to continually update a brand on its active typosquatting domains. These integrations also help brands keep up with the latest active MX records & protect their employees/ customers from BEC scams.
We also devised an algorithm to help brands prioritize the domains they can defensively acquire. This will be a part of the Typosquatting Dashboard (more on it coming soon) along with many other cool features.
To learn more, read our whitepaper: Guide to Domain Monitoring and Remediation
Request a Free Trial today: https://bolster.ai/start-trial