Bolster is excited to share a major landmark in our path to making the internet a safer place…

The Bolster Blog
Thought provoking blogs discussing recent trends on digital risk protection services, phishing protection, threat intelligence, artificial intelligence, machine learning, brand protection and more!
Recent Posts
How to identify fake CAPTCHA that initiates malware
In today’s digital world, online security measures like CAPTCHAs (Completely Automated Public Turing test to tell Computers and Humans Apart) have become a crucial part.
How scammers use AI to create investment fraud traps
Imagine this: You’re offered a once-in-a-lifetime investment opportunity by someone who seems like a seasoned financial expert. They speak with confidence, use impressive jargon, and.

Phishing in Focus: Bolster's 2024 Mid-Year Phishing and Online Scam Update
With the unprecedented surge in phishing attacks sparked by AI, protect your business with data into key phishing and scam trends including election fraud, industry-targeting, and consumer interest scams.
How to Safely Open a Suspicious Link in 4 Steps
Imagine a world without hyperlinks—navigation between web pages, emails, and…
The Click That Stole Holidays: Black Friday and Cyber Monday Scams Unmasked
The onset of Cyber Monday and Black Friday deals is…
Phishing & Online Scams Targeting the 2024 Election
As the 2024 U.S. presidential election draws near with discussions,…
Understanding Domain Reputation Attacks and How to Protect Your Brand
Without even defining the term, you could probably guess that…
Understanding Prepending and Its Role in Cybersecurity Threats
Another day, another cybersecurity threat you should be aware of…
In-Session Phishing is Becoming An Advanced Cybersecurity Threat
Phishing remains pretty much synonymous with “cyber attacks” as bad…
Stopping Wire Fraud Scams Targeting VCs and Limited Partners
Everyone in the world knows if you need money for…
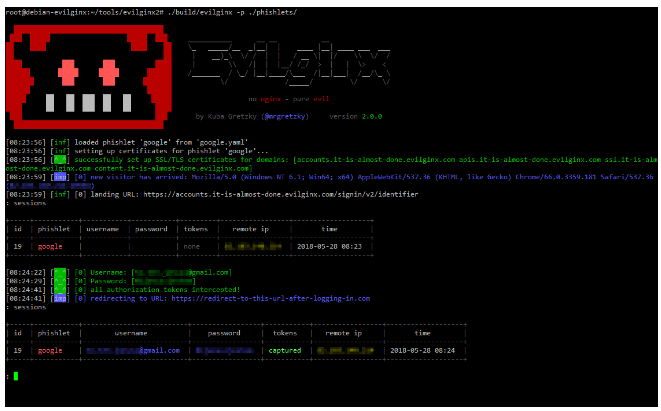
Understanding Man-in-the-Middle Phishing: A Deep Dive into Evilginx
Phishing continues to be one of the most popular ways…
Understanding Telegram Carding: The Dark Side of Digital Transaction
In the huge evolving rolodex of cybersecurity threats, carding remains…
Unpacking the Risks: Understanding the Dangers of .zip Domain Phishing & .mov Malware TLDs
New top-level domains (TLDs) like .zip and .mov have brought…
Understanding CEO Spamming and Its Threats
CEO spamming is a significant cybersecurity threat that can impact…
Proactive Defense Against BEC Attacks: How to Stay Ahead of the Scammers
Business Email Compromise (BEC) has become a significant threat to…