Bolster is excited to share a major landmark in our path to making the internet a safer place…

The Bolster Blog
Thought provoking blogs discussing recent trends on digital risk protection services, phishing protection, threat intelligence, artificial intelligence, machine learning, brand protection and more!
Recent Posts
DeepSeek Under Attack: How Scammers Are Using Fake Domains & Phishing to Target Users
Introduction: The Rise of DeepSeek & Emerging Threats DeepSeek has recently gained significant traction in the market, becoming a go-to solution for many users. However,.
How to Safely Open a Suspicious Link in 4 Steps
Imagine a world without hyperlinks—navigation between web pages, emails, and text messages would be cumbersome. Hyperlinks have become indispensable in our digital lives, offering convenience.

Phishing in Focus: Bolster's 2024 Mid-Year Phishing and Online Scam Update
With the unprecedented surge in phishing attacks sparked by AI, protect your business with data into key phishing and scam trends including election fraud, industry-targeting, and consumer interest scams.
How to Conduct a Website Takedown In 3 Easy Steps
Malicious website domains are a headache for organizations to…
Embedded Secrets in Webpage DOMs (and How to Use this Data to Protect Your Assets)
The dangerous impact of typosquat domains, and how frequently…
Widespread Brand Impersonation Scam Campaign Targeting Hundreds of the Most Popular Apparel Brands
Bolster’s threat research team recently uncovered a widespread brand…
Types of Cybercrime: A Comprehensive Guide to Uncover and Prevent Digital Attacks
The concept of using the Internet for criminal activity…
The Most Critical Domain Security Risks & Five Ways to Prevent Attacks
Security professionals are concerned about the security of their…
Web Beacons: How To Effectively Use Them For Phishing Detection
Phishing attacks are the most common attack vector for…
SEO Poisoning Attack Linked to 144,000 Phishing Packages
Introduction In a recent incident involving the NuGet, PyPI, and…
24 Security Lessons to Remember This Holiday Season
Cybercriminals run rampant during the holiday season. For them,…
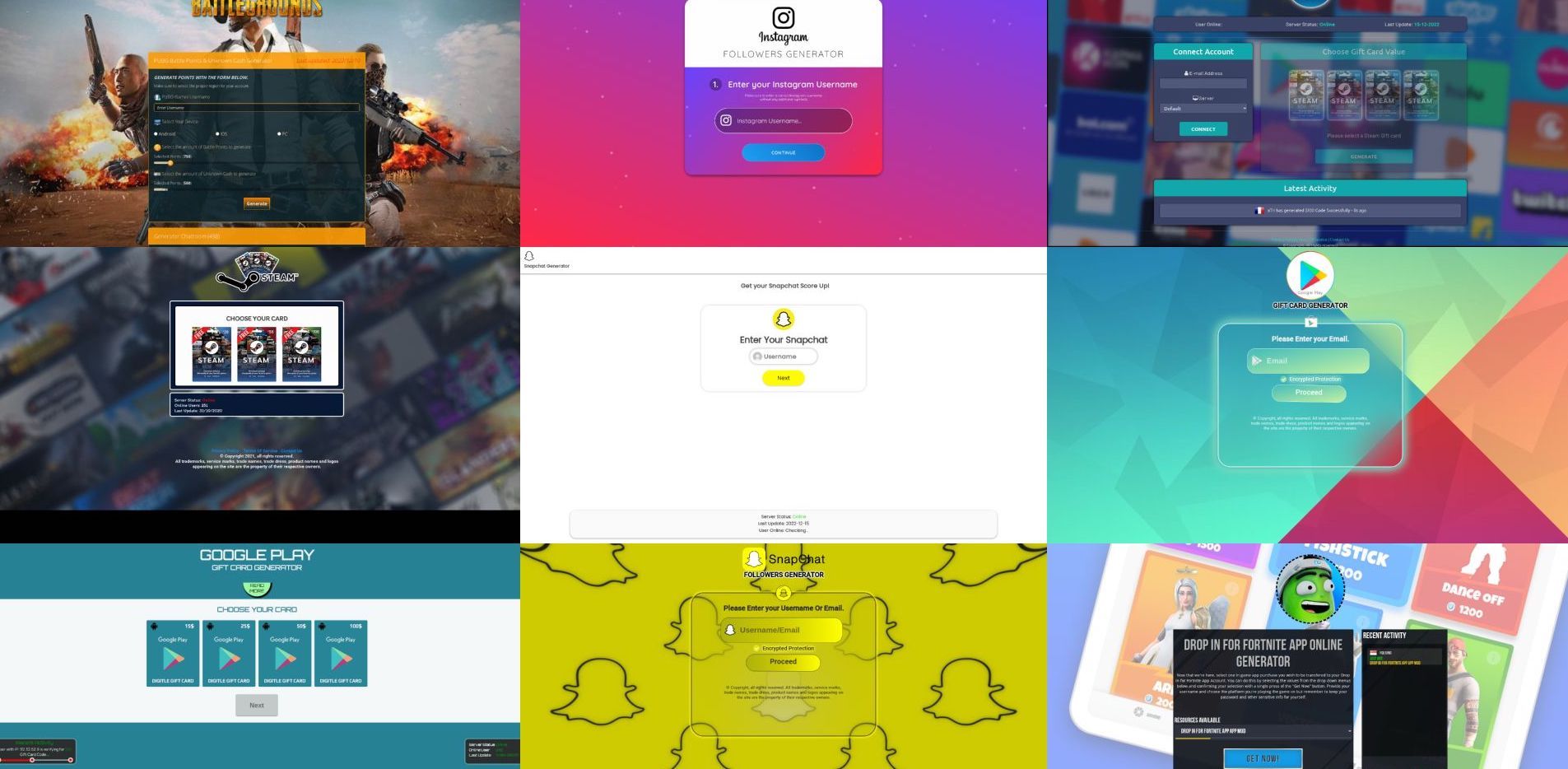
Elon, Bots, and Rampant Fraud on the Web
Elon Musk recently highlighted a big problem with Twitter:…
Web Automation with NodeJS
[Part 2] – Understanding/Evaluating Web Scraping, Crawling, and Automation…