Introduction
Before we jump into the world of subdomain hijacking/ takeover, let’s try and understand what a subdomain is: A subdomain is an extension to your primary domain name. It helps you organize the content of your websites into different sections. Think of it as a folder with subfolders on your laptop to organize your data.

In the image above, you can see two examples of subdomains on the primary domain yourdomain[.]com. blog[.]yourdomain[.]com can be used to redirect users to your blogs, and shop[.]yourdomain[.]com can be used to host your shop. You can also have a sub-subdomain on your website (example: tshirt[.]shop[.]yourdomain[.]com). DNS does not impose limits, and you can go as deep as you want, as long as your entire hostname is within the 255 character limit.
What is Subdomain Hijacking?
Subdomain hijacking is an attacker having control of your subdomain even though you own the domain is called a subdomain takeover. This can happen due to us hosting our domains on hosting providers like AWS, GitHub, Shopify, and Zendesk and having incorrect configurations. One example of incorrect configurations is Dangling CNAME Records. Admins make DNS records but never claim them.
Let us go through an example to understand this better. You want to start selling merchandise for your brand and decide to use Shopify’s services. Here is what you would be doing:
- Create your shop on Shopify – yourbrand[.]shopify[.]com
- Now, create a CNAME record that points shop[.]yourdomain[.]com to yourbrand[.]shopify[.]com
Every time a user tries accessing shop[.]yourdomain[.]com they will start seeing the online store you created using Shopify. It is all good until you cancel Shopify’s subscription and forget to remove the associated CNAME. Once you cancel Shopify’s subscription yourbrand[.]shopify[.]com becomes available for anyone to purchase and host their shop. And because you forgot to remove shop[.]yourdomain[.]com, every time a user tries to access it, they will still be redirected to yourbrand[.]shopify[.]com, which you don’t own anymore. Shopify is just an example. Think about the subdomains of a brand using multiple third-party services like AWS, GitHub, Zendesk, and more.
There are two stages of subdomain hijacking:
- Discovering the subdomains on a given domain
- Scanning each domain for an outstanding threat
In this blog, we will be going through each of the stages in detail
Discovering the subdomains on a given domain
Multiple free and open-source tools are available to discover subdomains on a given domain and help protect against subdomain hijacking. Two of the most common subdomain discovery tools are Sublist3r and Findomain. Both are easy-to-use open-source intelligence to gather subdomains. Once you enter a domain into one of these tools, they search on multiple sources, including VirusTotal, Threatcrowd, Google, Yahoo, and DNSDumpster.
Sublist3r
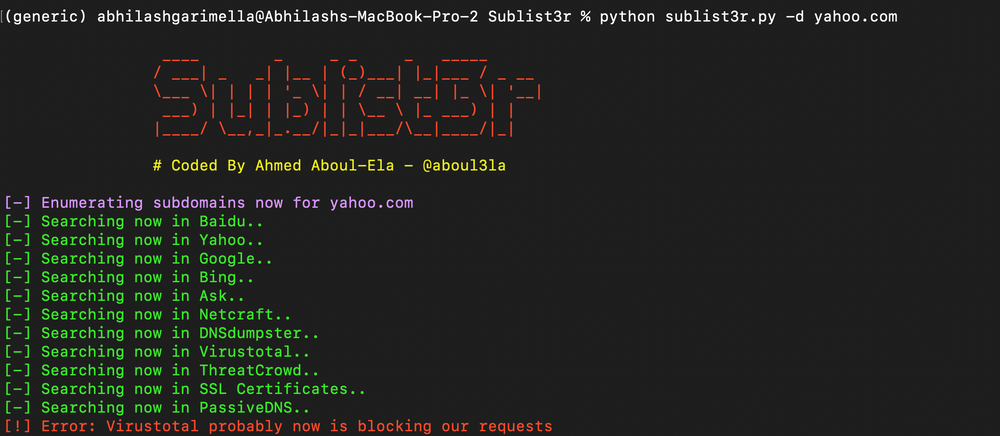
It is available as a terminal version. You can download the Sublist3r git and execute it in your terminal. If you are a Python user, Sublit3r can also be downloaded via pip using ‘pip install sublist3r’. Below is the screenshot of an example run for searching subdomains on yahoo[.]com. It detected 101,168 subdomains in under a minute.
Findomain
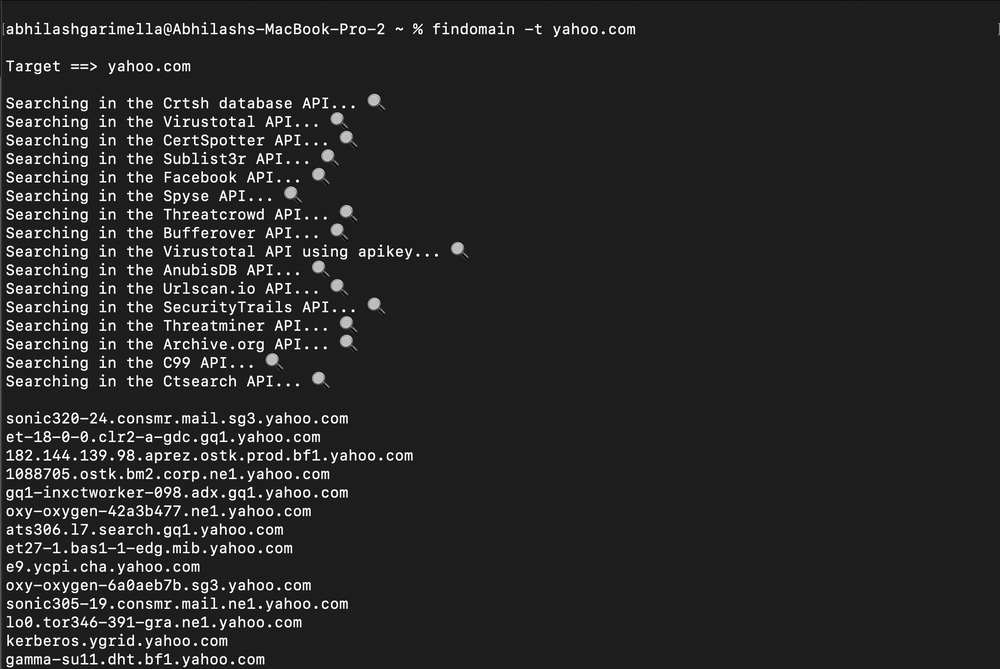
Findomain can also be run via a terminal. Mac users can install it using ‘brew install findomain’. Here is a sample run for yahoo[.]com. It discovered over 113,055 subdomains in 15 seconds.
Detecting subdomains at risk of Subdomain Hijacking
One, you have a list of these subdomains; it’s easy to find which are at risk of subdomain hijacking. We can determine if a given subdomain is a threat for hijacking by a simple regex matching on the webpage’s content.
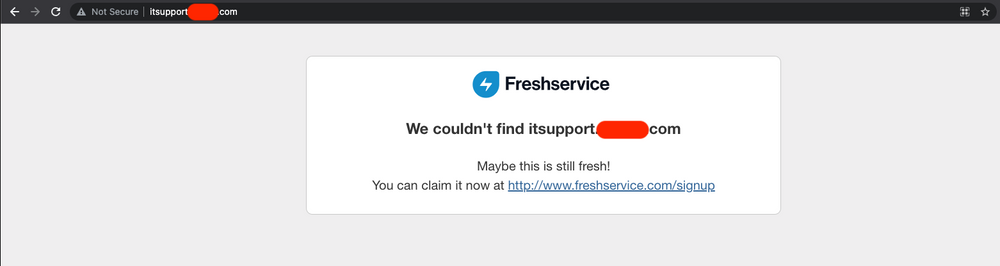
Here is an example of a subdomain using Freshservice to host its services. An attacker can now claim this subdomain and use it to host a phishing/ scam page.
Here is another example of a subdomain using Acquia Cloud to host its services.
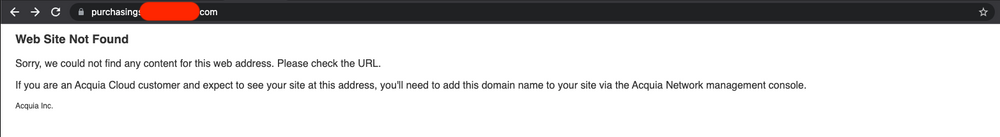
We compile a list of CNAMEs and Fingerprints associated with them. For example, from the Freshservice example: ‘Maybe this is still fresh!’ is the fingerprint, and ‘freshservice.com’ is the CNAME. Similarly, for the Acquia Cloud example: ‘If you are an Acquia Cloud customer’ can be a fingerprint.
There are multiple open-source GitHub repositories out there that maintain a list of these fingerprints and keep updating them daily. All an attacker needs to do is combine the discovery and fingerprinting tools to find subdomains at risk of subdomains hijacking
Here are a few
https://github.com/EdOverflow/can-i-take-over-xyz
https://github.com/haccer/subjack/blob/master/fingerprints.json
https://github.com/anshumanbh/tko-subs/blob/master/providers-data.csv
https://github.com/ArifulProtik/sub-domain-takeover/blob/master/subdomain.py
https://github.com/SaadAhmedx/Subdomain-Takeover/blob/master/ItsOver.py
https://github.com/Ice3man543/SubOver/blob/master/providers.json
https://github.com/m4ll0k/takeover/blob/master/takeover.py
https://github.com/antichown/subdomain-takeover/blob/master/takeover.py
Conclusion
Subdomain monitoring, like typosquatting monitoring, should be done regularly to identify and mitigate threats against your domain from subdomain hijacking. There are also open-source tools that can perform both the discovery and detection of subdomains at risk.
About Us
Bolster Research Labs publish this blog. We also own https://checkphish.ai – a free URL scanner to detect phishing and scam sites in real-time.
If you are interested in advanced research, uncovering new scams, or working with cutting-edge AI, work with us at the Bolster Research Labs. Check out open positions here.
References
Sublist3r – https://github.com/aboul3la/Sublist3r
Findomain – https://github.com/Findomain/Findomain