How to Detect and Stop Social Media Fraud in 2023
In the online world, social media fraud happens fast. We know this to be true at Bolster through the threat intelligence our systems gather and the customers we serve. In 2020, we detected over 6.9 million phishing and scam pages, resulting in over $320 billion in brand losses and over $1.2 trillion in fraudulent transactions. (read the full report). And as 2021 ends, we expect the numbers for social media fraud to notch even higher.
Traditionally, much of the fraud stems from threat actors targeting companies’ websites through typosquatting attacks resulting in fake websites designed to harvest credentials or siphon off business. Recently though, threat actors have shifted to social media platforms to stage fraud and scam attacks. For Security professionals, well, they’re finding themselves once again behind the brand protection 8-ball in a highly reactive mode trying to detect and remove social media fraud and scams. Without new tools and technologies coming to their aid, security personnel will continue to struggle to get ahead of the online fraud threat curve.
Detecting Social Media Fraud – Why is it so hard?
Detecting social media fraud and scams is challenging for several reasons.
- There are a lot of social media platforms. First, and perhaps most apparent, many social media platforms exist online. There are big platforms like Facebook, Twitter, and YouTube, but much more spanning social, news, content, personal, and sharing sites. For security professionals, this means a virtually endless set of tasks continually scouring various social media platforms.
- Social media fraud and scams come in many forms. Besides many different platforms to monitor, there are many types of social media fraud, cons, and infringements to be aware of (see examples below). Sometimes it’s fake ads leading unsuspecting visitors to fake websites or offers. Other times, counterfeit product or service sales are often complete with phony celebrity endorsements designed to dupe customers. And in yet instances, it’s fake profile pages impersonating executives or celebrities or threat actors staging attacks on legitimate profile pages through malicious links posted in comment fields. Staying on top of social media scams is yet another full-time job.
- Social media platforms aren’t governed like websites. Worth noting, nonetheless. Unlike websites controlled by a global system for registering domain names and a well-understood set of organizations and policies to report abuse (hosting provider, registrar, registry, ICAAN), with social media platforms, it’s more like the proverbial wild west. Each social media platform has policies and procedures for creating accounts, posting content, and reporting abuse. For security teams, it means traditional detection techniques like scouring new domain name registration lists aren’t an option, and instead, platform-specific approaches need to be adopted to find fraudulent activities or scams.
- Taking down and removing social media fraud and scams is a pain in the a**! This is the result of each social media platform operating independently. When social media fraud, scams, or infringements are detected, the steps needed to perform takedowns or removals vary drastically from platform to platform. This means security teams not only have to learn how to report abuse or fraud on a platform-by-platform basis but also that monitoring takedown success must also be done on a per-platform basis. Compared with websites, initiating a takedown and monitoring takedown success globally by examining changes in global DNS records and SSL certificate transactions, for example, is far simpler.
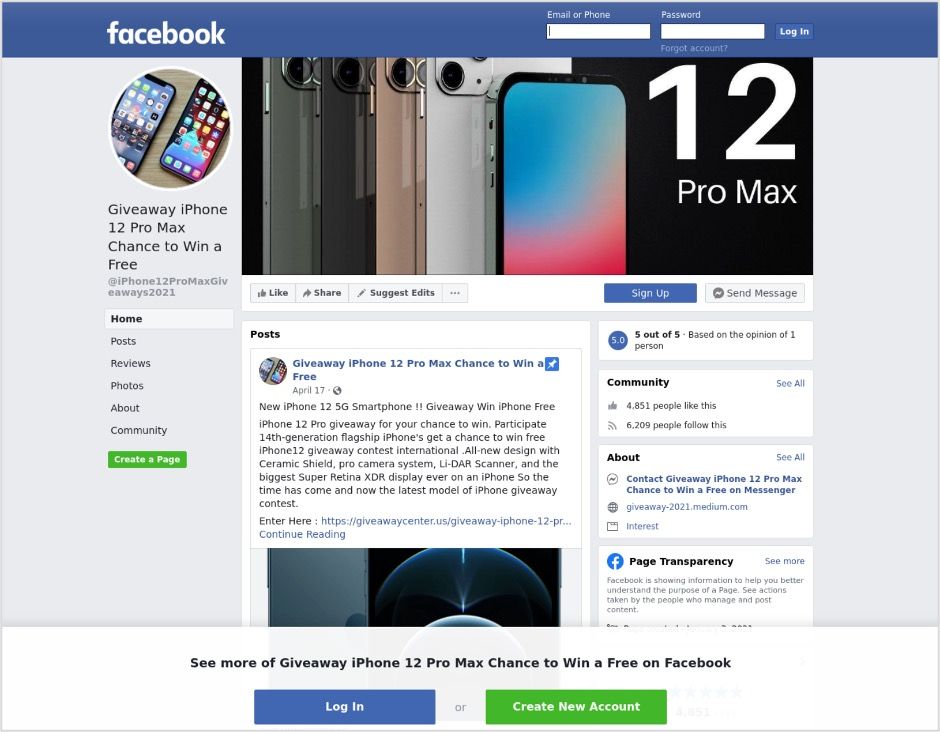
Figure 1. Fake Apple iPhone Giveaway on Facebook
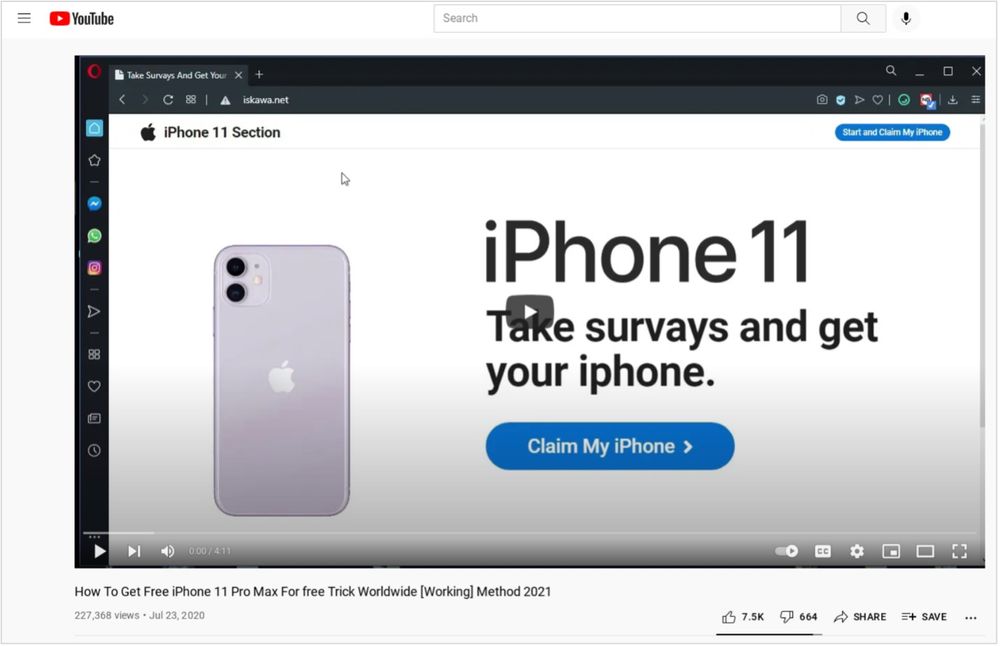
Figure 2. Fake Apple iPhone Giveaway on YouTube
Critical ingredients to eliminate social media fraud and scams
This isn’t meant to be a scare piece, but social media fraud and scams can wreak havoc on your business, brand, and security team. And one thing is for sure, if this is a problem for your business, it’s not something that can easily be remedied with SOC analysts alone. It will mostly like to grind them to the ground. The only way out, given the scope and scale of how threat actors operate, is with 1.) automation and 2.) machine learning—no ifs, ands, or buts.
- Automation – Self-driving workflows. With all the different social media platforms and the myriad scam types, manual discovery, inspection, and evidence-gathering workflows won’t scale. Instead, automated workflows are needed to scrape social media sites, retrieving and inspecting ads, content, and URLs. These workflows must be performed daily as a baseline operation for fraud and scam detection. Automating these tasks is a massive time-saver for SOC teams by moving repetitive tasks to the background allowing more focus to be applied to mitigation and remediation versus discovery.
- Machine learning – Trained eyes that scale. Machine learning is the other side of the social media protection coin. While automation serves to replace and scale repetitive human tasks, machine learning replaces and scales the trained eyes for detection and inspection. Done right, machine learning can offload the process of detecting fake ads, counterfeit products, logo infringements, and even content abuses. And unlike a team of analysts, the machine learning processes don’t get tired over time, experience eye fatigue, or generally get tired. Instead, with machine learning, you have a detection and inspection engine running 24/7, allowing SOC analysts to assume more valuable roles in the overall security operation…and avoid burnout.
Bolster Social Media Protection solution
At Bolster, we recently extended our automation and machine learning capabilities to address social media fraud and scams. With the new capabilities, customers can automatically monitor many social media platforms for fake ads, counterfeit products, trademark infringements, impersonations, phishing campaigns, and content abuses. Bolster’s automated workflows can be spun quickly, enabling machine learning algorithms to detect real-time social media fraud and infringements.
As with other modules in the platform, social media threat data is presented in an intuitive dashboard, making it easy to track social media threats throughout the complete lifecycle from discovery to takedown and removal. Bolster’s detection engine, powered by natural language processing, computer vision, and deep learning models, can detect fraud in less than 100 milliseconds with an astonishingly low false-positive rate of 1 in 100,000.
Detailed evidence is supplied when malicious activities are detected, including high-resolution screenshots with logo detection to facilitate investigations and takedowns. And for any URLs detected, our system will automatically scan the URLs using our CheckPhish engine to determine disposition (clean site, phishing site, scam site). If phishing is detected, the system will issue an automated takedown request resulting in a site takedown in as little as 3 minutes.

Figure 3. Bolster Social Media Protection Dashboard
Test drive Bolster today!
Interested in learning more and seeing our social media protection capabilities in action? Our team is ready when you are. Please fill out our Request a Demo form for a 30-minute run-through of capabilities. We’re confident the demo will be eye-opening and confident that we have a social media protection solution that is right for your business and brand.
***
Request a 30-minute demo
Learn more
Bolster Social Media Protection solution page









