In 2021, FBI Internet Crime Complaint Center IC3, received 19,954 complaints of BEC scams resulting in over 2.3 billion dollars in losses to businesses and individuals in the US.
Business Email Compromise scams primarily target company employees or individuals who are responsible for transferring funds.
For these scams, attackers use either spoofed or compromised email accounts of executives, employees, or business partners to make fraudulent payment requests.
These scams are carried out by financially motivated attackers. BEC attacks are also referred to as man-in-the-email attacks. The majority of BEC scam emails do not contain any links or attachments; this allows them to quickly get past email spam and virus protection filters.
How Business Email Compromise Scams Work
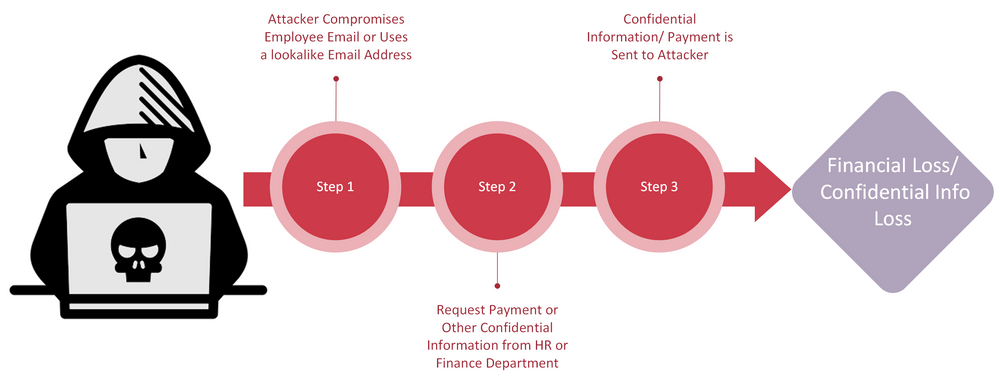
Using Similar / Lookalike or / Spoofed Emails
- Attackers acquire a domain name similar to the target company name and use email addresses from the acquired domain to send BEC scam emails.
- E.g. if the legitimate company’s email address is [email protected], the attacker may acquire examplec0mpany.com and use the email address [email protected] in scam campaigns.

- The email address looks very familiar to the company email address, but when you look carefully the letter “o” in the company domain name has been replaced with zero “0”.
- This process of acquiring similar domains is referred to as typosquatting. See [What Every CISO Should Do to Fight Typosquat Attacks]
- Attackers can also spoof email addresses by manipulating the email headers to show emails coming from [email protected] address to look like it’s coming from [email protected] Most email clients can detect spoofed header-based emails and show a warning message.
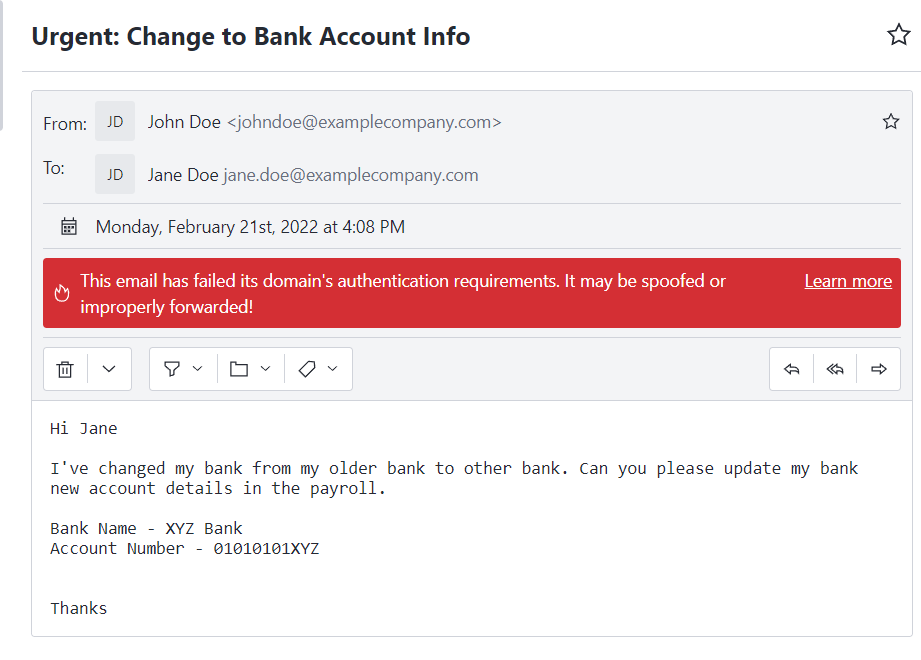
But when we take a look at the headers of such emails, we can see the actual sender of the email is different.

Using Compromised Email Accounts
- Attackers compromise legitimate accounts of company employees or executives using tactics like phishing, credential stuffing, or by infecting them with malware or keyloggers.
- These hijacked accounts are used to send fraudulent payments requests, invoices, or requests for sensitive data to the finance or HR department of that company.
- These emails are less suspicious since the email is coming from the legitimate company email address which will pass the internal spam, rule-based filters.
Ghost Spoofing
- Attacker adds the legitimate company email address as part of the sender name, so someone in a hurry might think that the sender’s email is legitimate.

Types of BEC Fraud
There are 5 common types of BEC fraud
- CEO Fraud: Attacker impersonates a CEO and makes requests for personal data or payments to a specific account
- Bogus Invoice: Attacker sends a fake invoice from a lookalike domain of partner company or contractor. It requires the attacker to do research on the products and services of a company before sending such emails.
- Account Compromise: Attacker compromises internal email accounts of the company employee and makes requests using the internal email address.
- Attorney Impersonation: The attacker claims to be the lawyer in charge of confidential issues and claims to be from a law firm.
- Data Theft: Human Resources & Accounts department employees are targeted to obtain other employees’ personal information for target enrichment. This can be used in upcoming & more targeted campaigns.
Incidents Involving BEC Scams
- Google & Facebook BEC Scam [Over 100 Million USD]: The biggest BEC scam of all time that happened between 2013 to 2015. A Lithuanian man named Evaldas Rimasauskas set up a fake company to impersonate a Taiwan-based hardware company. The fake company alias was used to send fake invoices, contracts, and letters to big tech companies. Google & Facebook ended up paying an estimated 121 million dollars over a period of years.
- Toyota [37 Million USD]: In 2019, Toyota Boshoku Corporation, a Japanese auto parts supplier, was the victim of a 37 million dollar BEC fraud. An executive of the company’s financial department was tricked into executing a wire transfer of 37 million USD by BEC scammers.
- Snapchat Employee Payroll Leak: BEC scammers are often financially motivated. But in the case of Snapchat, they managed to trick an HR person into handing over the payroll information of current and former employees by impersonating the CEO of Snapchat.
BEC scams are by far the most financially damaging cybercrime as compared to other cybercrimes. According to IC3, in the 2021 cybercrime report, over 2.3 billion USD in financial damages were reported from BEC scams in the United States.
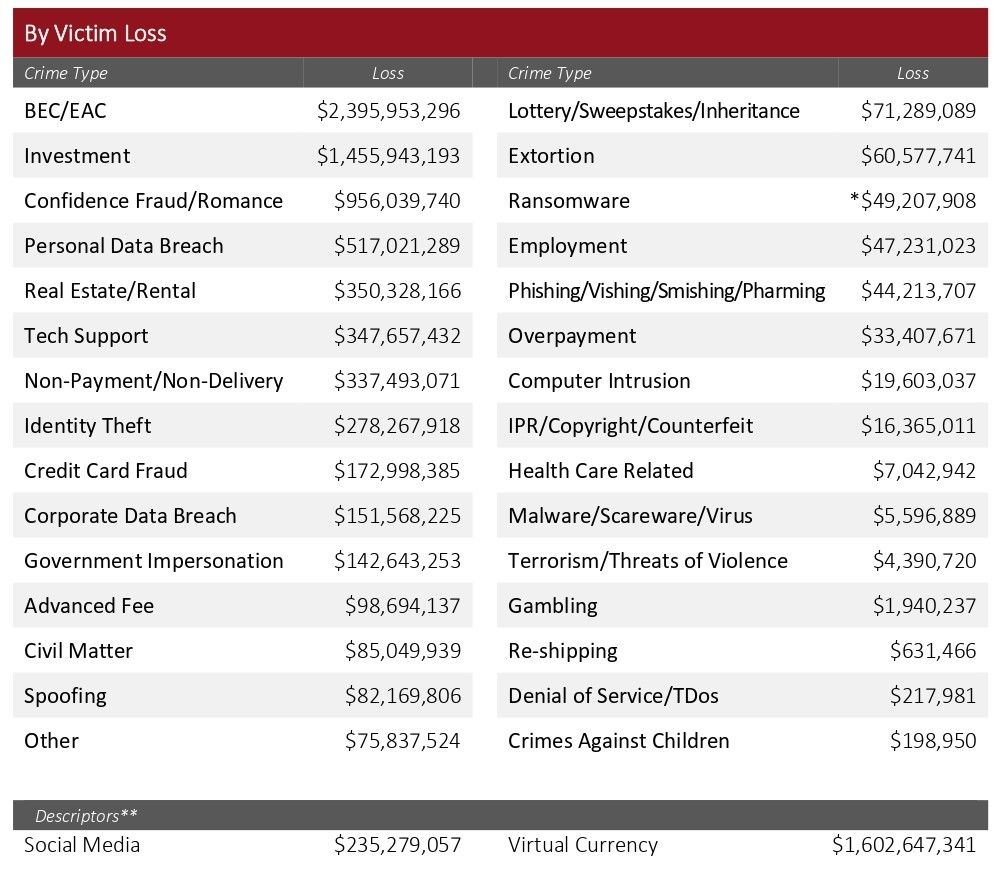
The financial damaged caused by the BEC scams have been rising every year. Attackers are becoming more sophisticated in researching companies & targeting employees.
There’s no silver bullet for stopping these scams other than following best practices. Only good security awareness training, email filtering & checking, and multiple layers of communication & verification can help in minimizing the risk of employees falling prey to such scams.
If you are trying to protect your brand from typosquatting and BEC attacks, click here for a free typosquatting report and here for a free trial.
About Us
This blog is published by Bolster Research Labs. We are also creators of https://checkphish.ai – a free URL scanner to detect phishing and scams sites in real time.
If you are interested in advanced research and uncovering of new scams or working with cutting edge AI, come work with us at the Bolster Research Labs. Check out open positions here