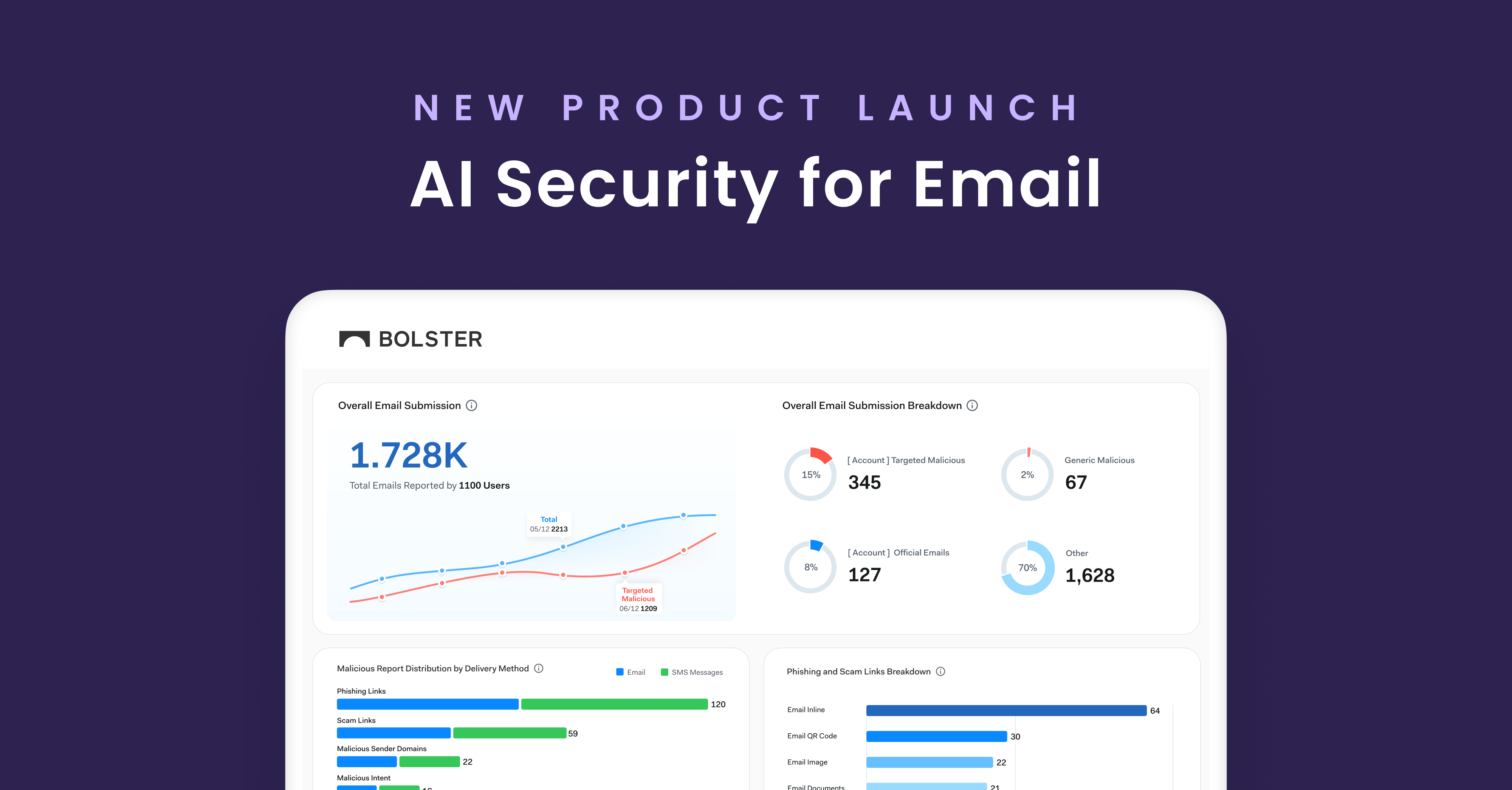
In today’s digital landscape, email continues to be a primary…
78 results for keyword "Phishing"
Credit Union Scams: How Cybercriminals Are Targeting Small Credit Unions in the US
In recent months, Bolster’s research team has identified a surge…
Understanding Domain Reputation Attacks and How to Protect Your Brand
Without even defining the term, you could probably guess that…
Is This a Phishing Link? How to Limit Risk Before Clicking.
Can you imagine a world without hyperlinks? They have become…
Understanding Prepending and Its Role in Cybersecurity Threats
Another day, another cybersecurity threat you should be aware of…
Social Engineering: The Gateway to Phishing Attacks
Cybersecurity threats continue to be an ever-present danger, and among…
In-Session Phishing is Becoming An Advanced Cybersecurity Threat
Phishing remains pretty much synonymous with “cyber attacks” as bad…
Cracking the Shield: Methods Hackers Use to Bypass MFA
Multi-Factor Authentication (MFA) has emerged as a fundamental element in…
Stopping Wire Fraud Scams Targeting VCs and Limited Partners
Everyone in the world knows if you need money for…
Cracked Code, Stolen Data: The RisePro Threat on GitHub
Have you ever downloaded “free” software online? If so, you…
Weekly News Roundup: Ransomware Skyrockets, Proofpoint Phishing Emails, and More
This week, we’ve seen some big headlines in terms of…
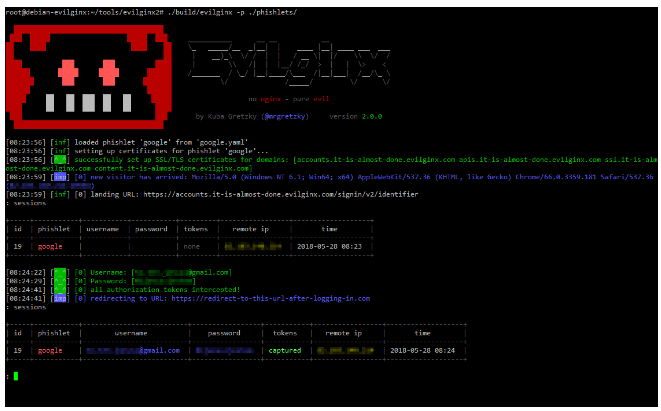
Understanding Man-in-the-Middle Phishing: A Deep Dive into Evilginx
Phishing continues to be one of the most popular ways…