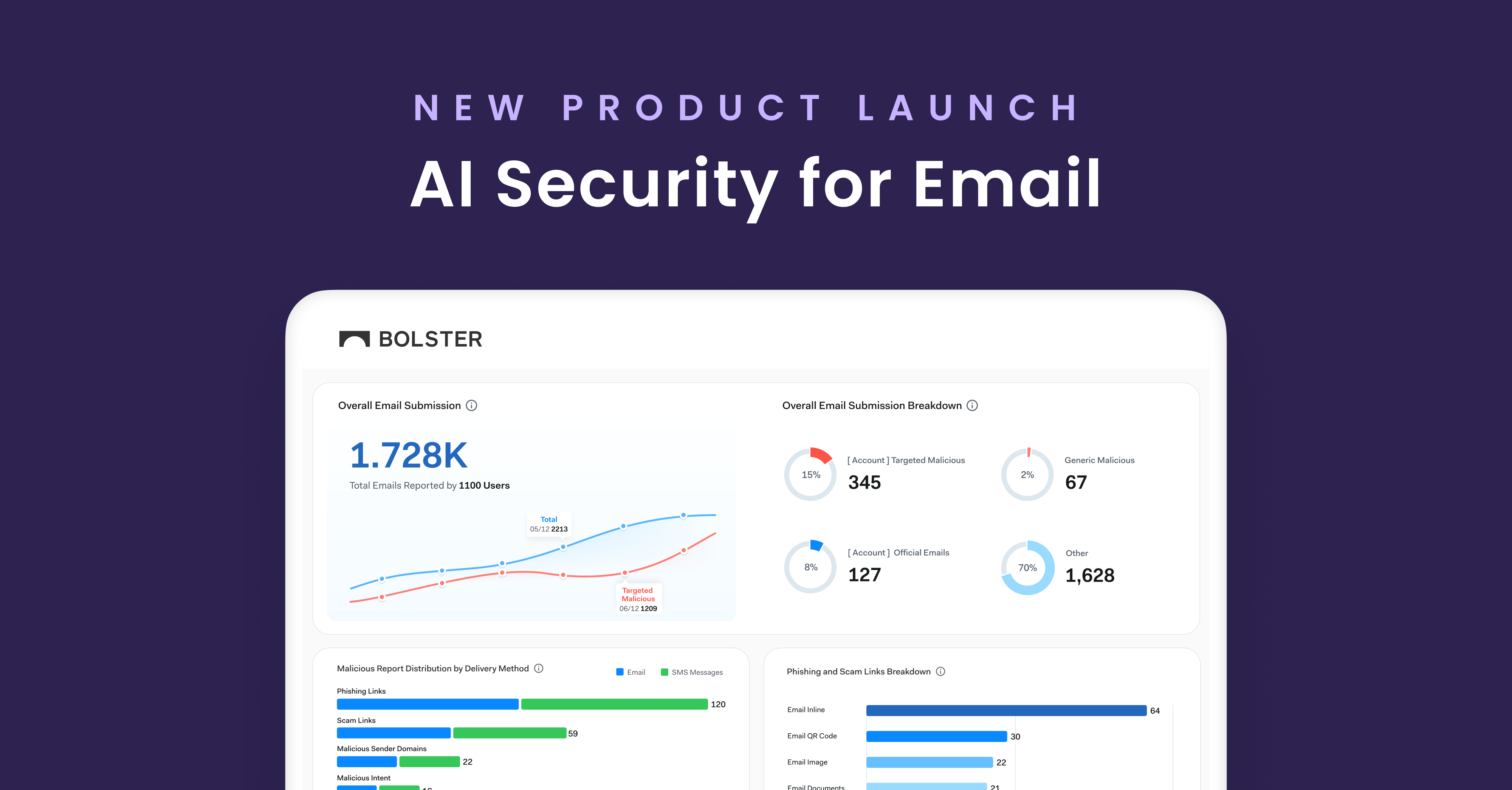
Organizations are making strides to better defend against cyber threats with effective tools and technology to protect their attack surface. While they might be better equipped to identify phishing attacks and typosquat domains, but when it comes to summarizing their program status or how their budget is being used, many organizations struggle to prepare effective reports.
We launched Bolster Insights to help facilitate cybersecurity reporting, making program decisions and conversations more efficient. With instant visibility of performance analytics across your digital risk landscape, cyber risk teams can concretely determine how your budget allocation is performing, visualize where your greatest cyber risks are hiding, and present program findings and company risks to stakeholders.
What is Bolster Insights?
To break it down, Bolster Insights is our newest product feature which provides customers with access to customizable reports based on their program data. Bolster Insights is configurable reporting and analytics that can quickly show a wide array of reports based on a company’s needs.
Our newest product feature offers a variety of reports to provide customers with information like:
Insight into Threat Origination
Bolster Insights provides data on what threat feeds are most prevalent to help organizations identify their biggest cyber threats. With access to data source analysis, including breakdowns of threats by each Bolster data feed, users can prioritize remediation decisions easier, and trust that the data their acting on is coming from an accurate source. Reports showcasing threat types based on type of feed scanned help effectively summarize the types of attacks your organization faces and can be compared overtime.

Analysis of Remediation Effectiveness
A key piece of information executives and company stakeholders want to see is how quick your security and risk team is remediating given cyber threats. Bolster Insights provides multiple report views of your organization’s takedown speeds, including breakdowns as specific as your average time to takedown a phishing attack vs a typosquat domain or spam social media account. Your time-to-remediate can be indicative of how likely your organization is to be impacted by a potential attack, so highlighting quick remediation speeds and reporting on your time to takedown is often important for security teams.

Historical Data to Predict Future Risks
With our industry-leading AI and machine learning technology scanning data points daily, we keep historical data and past threat trends in our corner to help defend against future hacker activity. Customers can use historical phishing, typosquatting, and dark web data to keep track of and predict hacker’s moves, facilitating smarter defensive decisions.

Why Does Your Organization Need Better Reporting Capabilities?
It might not seem like a top priority on the surface, but when your threat detection and takedown capabilities are summarized in effective reports, your organization can operate more smoothly with data-backed decisions. Without customized reports, CISOs and security teams often struggle to clearly communicate their program status.
Here are a few common pain points security and risk professionals can solve for with effective reports from Bolster Insights:
1) Teams struggle to identify where threats originate: Identifying the root cause of the problem and stopping threats before they are acted on can be time-consuming, and a bit of a guessing game without effective reporting. Organizations often struggle to identify the total view of types of threats being detected, and how those threats compare over time.
With effective reporting technology from Bolster Insights, users can access a breakdown of threat types impacting their network, what sources (ie spam feeds, anti-virus feeds, etc) threats are being detected with, and historical data on how those threat reports have evolved over time.
2) Security teams can’t clearly determine their threat remediation time: One of the most helpful indicators of security program effectiveness is how quickly your program remediates cyber threats. But without a trusted solution in place to summarize average takedown speed, it’s difficult to evaluate if given cybersecurity tools or decisions are effective. Without data on remediation times, it can also be harder to learn from historical threat activity and avoid using ineffective practices again in the future.
Bolster Insights provides detailed views of your organization’s remediation effectiveness, including average takedown times for phishing attacks versus typosquat domains, and how your program compares from month to month (or whatever timeframe your organization prefers).
3) Organizations aren’t able to proactively prevent future threats: Without access to trusted, data-backed trends reports, security teams are often missing a potentially crucial trend or suspicious web activity surfacing in their network. Security professionals might not have access to data to compare how different types of web threats versus suspicious email activity are targeting them and are choosing to distribute resources and scanning capabilities in general ways, instead of what could proactively protect them better.
With access to reports generated by Bolster Insights, security teams can quickly identify the most likely avenues for hackers to act on (typosquat domains, parked domains, email phishing, etc) as well as which web hosting providers are the riskiest. This can allow for better proactive budget allocation and monitoring efforts towards riskier avenues.
Program Improvements With Bolster Insights
Our Bolster mission is to help facilitate safe access to the internet for everyone, which means constantly targeting different customer pain points when it comes to defending against bad actors and evolving hacking strategies.

With access to accurate, easy-to-decipher cybersecurity reports, Bolster customers can better:
- Increase business and operational value, including better use of potentially limited resources and more effective cybersecurity reporting to company stakeholders, C-suite, and board of directors.
- Gain visibility into their digital risk landscape by understanding historical threats and potential new risks, promoting quicker, effective decision making, and helping target the cause of cyber attacks at the source.
- Align and efficiently report on security practices for audit or compliance requirements based on industry, geographical, or reputational needs. Common compliance requirements where organizations need to show how they safeguard sensitive data include the Gramm-Leach-Bliley Act for financial institutions, PCI DSS for retailers, and HIPAA for healthcare, DORA for many European organizations, and more.
Get Started Today With Bolster Insights
Whether you’re new to Bolster’s threat detection and takedown technology, or already using our capabilities to defend against typosquat domains and phishing attacks, Bolster Insights can be an effective tool to compliment your cyber monitoring and takedown program.
To learn more about Bolster Insights, or to see what reports we can provide for your organization, request a free Bolster demo today. For current customers, please reach out to our customer support team at [email protected].