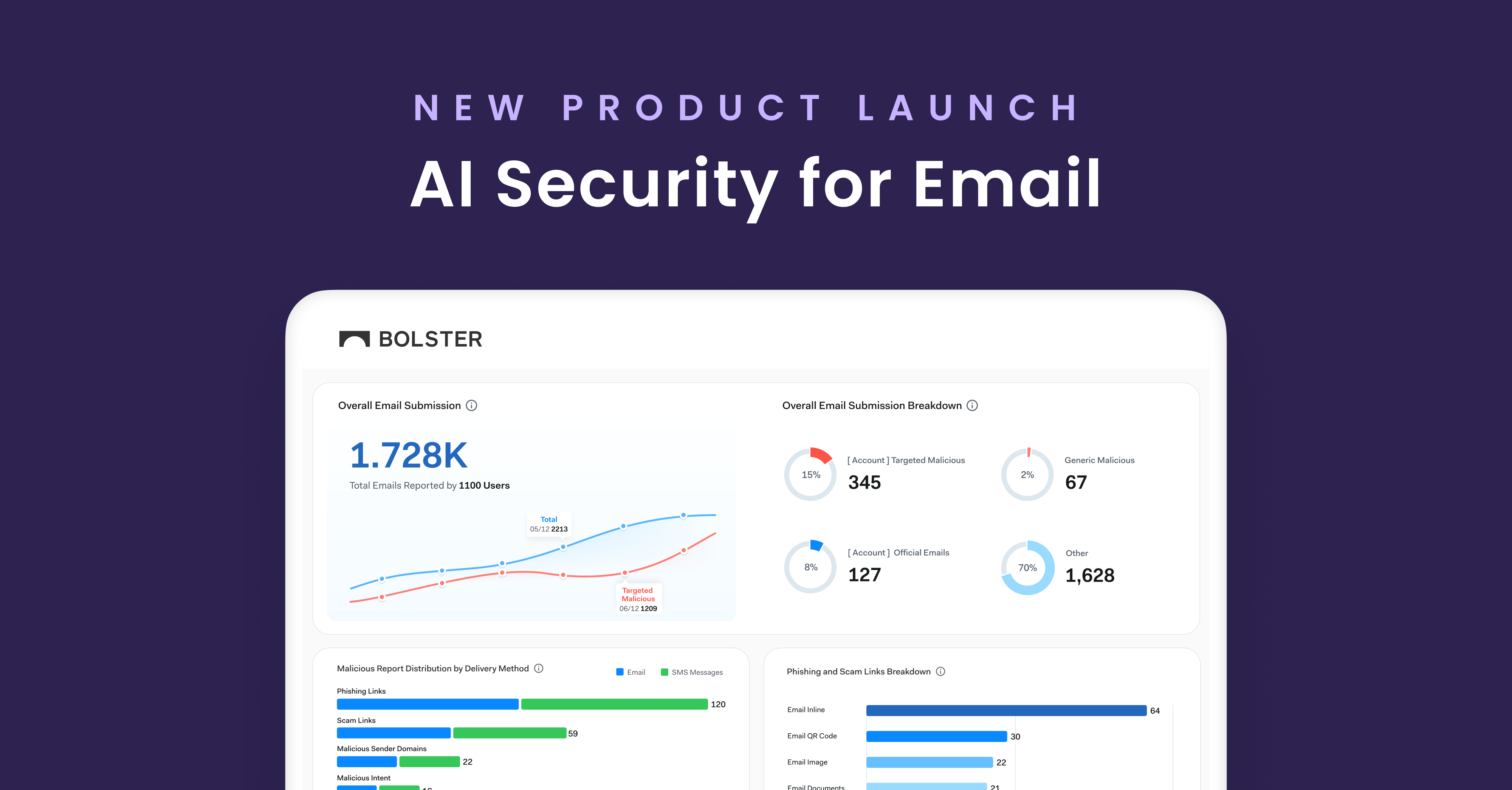
Phishing threats evolve and adapt quickly. Even before one phishing domain is taken down, many more emerge. It can become a game of whac-a-mole for security and IT teams with a lot on their plates.
Keeping track of newly emerging phishing threats is necessary to protect users. As more and more processes go digital, bad actors are becoming more and more sophisticated to access wanted data. Phishing sites are becoming more and more lucrative in terms of cyber attacks, making them a popular choice for hackers.
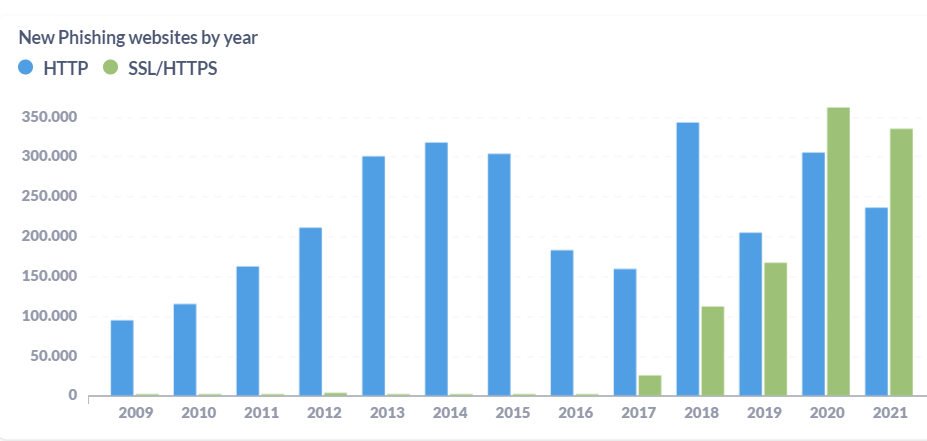
There are many phishing threat intel solutions on the market that track phishing URLs, domains, IPs associated with them. Some of them offer free or inexpensive Phishing URL feeds, where some are more restrictive on what users can access before hitting a paywall.
Here is a list of a few such projects which keep track of phishing threats and are updated regularly.
1. CheckPhish
All the feeds mentioned above can be used for blocklisting URLs/ Domains. If you see a suspicious/ unknown URL we recommend gathering insights on it before accessing it. You can gather insights using open sourced tools like CheckPhish.
CheckPhish is powered by deep learning models that can determine whether an input URL is hosting a phishing or scam page in real time. Here is an example scan from CheckPhish:
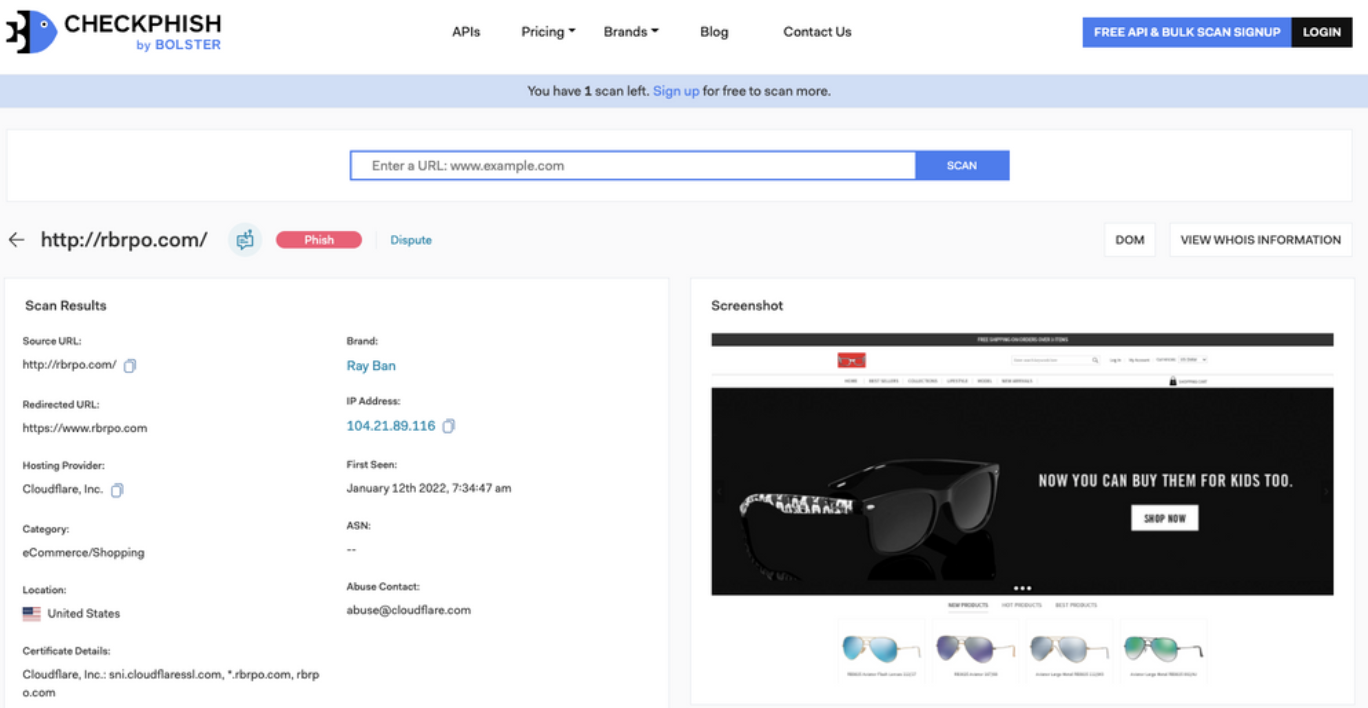
CheckPhish users are able to access a real-time URL and website scanner. Once a URL is submitted in CheckPhish, the engine spins up an automated headless browser to capture a live screenshot, natural language content on the webpage, DOM, WHOIS, and other essential information.
See CheckPhish in action be visiting the website.
CheckPhish Plugin for Outlook
CheckPhish also has a Microsoft Outlook Plugin to identify phishing and scam links embedded in emails and protect you from these attacks. (Learn more about how to check for spoofed emails in Outlook.)

2. PhishStats
PhishStats is a real-time phishing data feed. It collects and combines phishing data from numerous sources, such as VirusTotal, Google Safe Search, ThreatCrowd, abuse.ch and antiphishing.la.
PhishStats has a real-time updated API for data access and CSV feed that updates every 90 minutes.
PhishStats also provides interactive public dashboards that help in visualizing the data and getting an insight into the bigger picture.
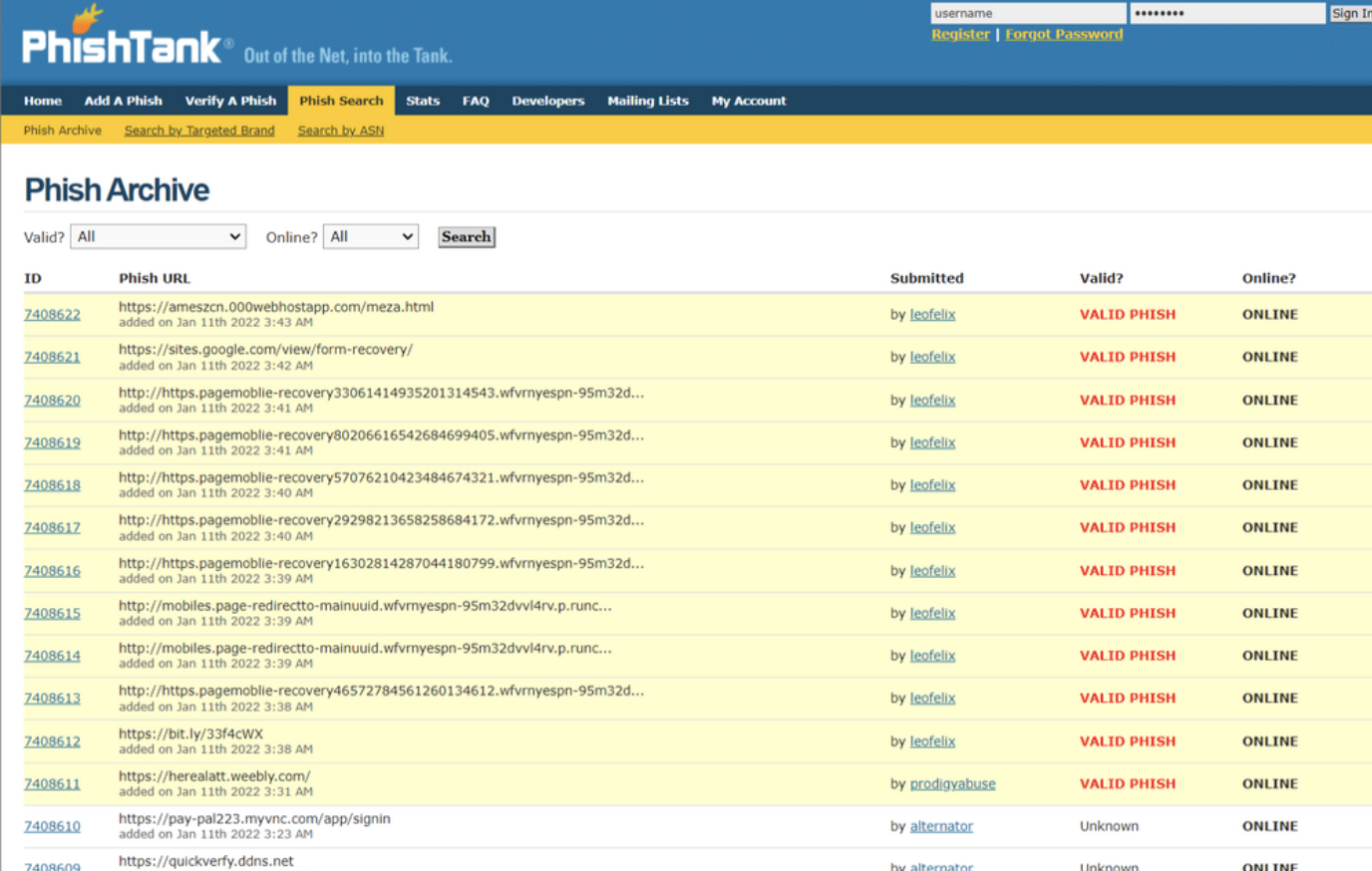
3. PhishTank
PhishTank is a free community site where anyone can submit, verify, track and share phishing data. It provides accurate, actionable information to anyone trying to identify bad actors, whether for themselves or others (i.e., building security tools). PhishTank is operated by Cisco Talos Intelligence Group (Talos).
PhishTank allows users to submit phishing URLs or access phishing archive data via API or using the search on their website.
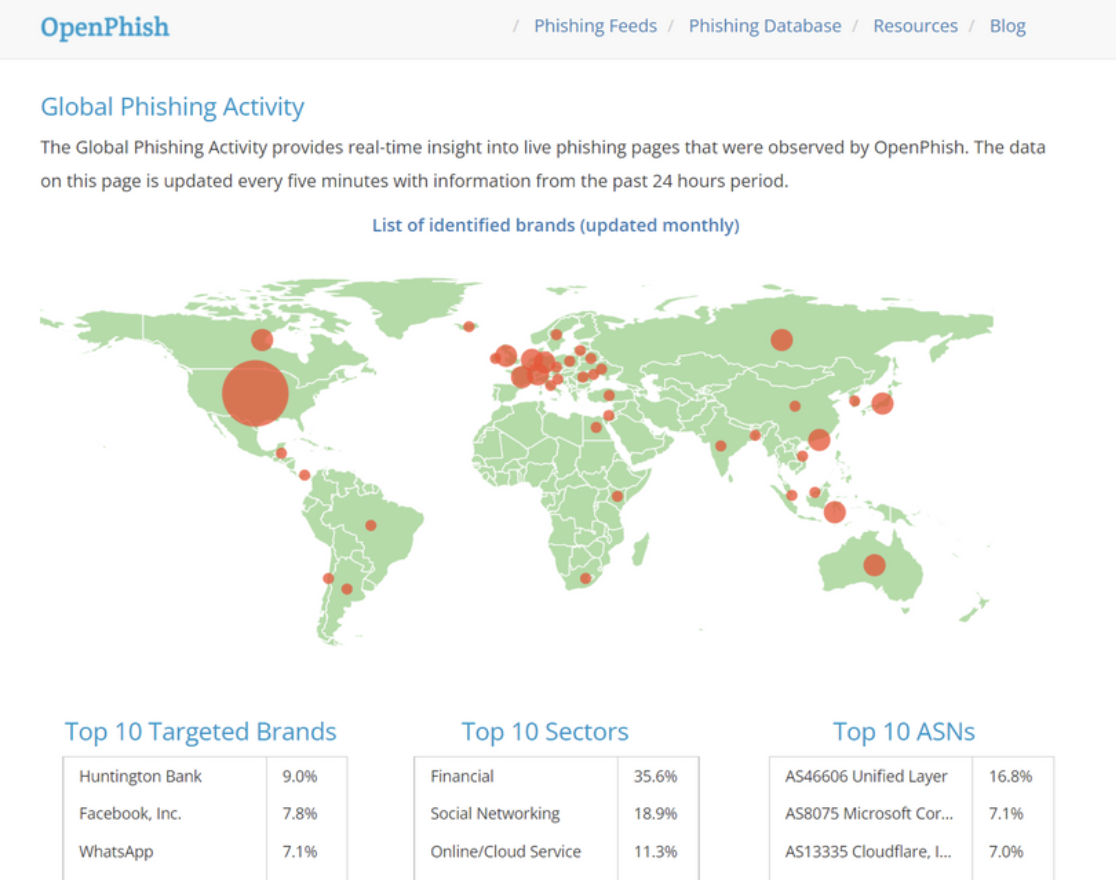
4. OpenPhish
OpenPhish is a service that delivers actionable intelligence about active phishing threats. It includes a restricted free community feed that offers a list of phishing URLs updated every 12 hours. Premium feeds from OpenPhish are updated every 5 minutes and includes additional data points such as targeted brand, industry, page language, country, and more.
The global phishing activity dashboard from OpenPhish provides real-time perspective into live phishing pages that OpenPhish has identified. The data on the dashboard is updated every five minutes with information from the past 24 hours period.
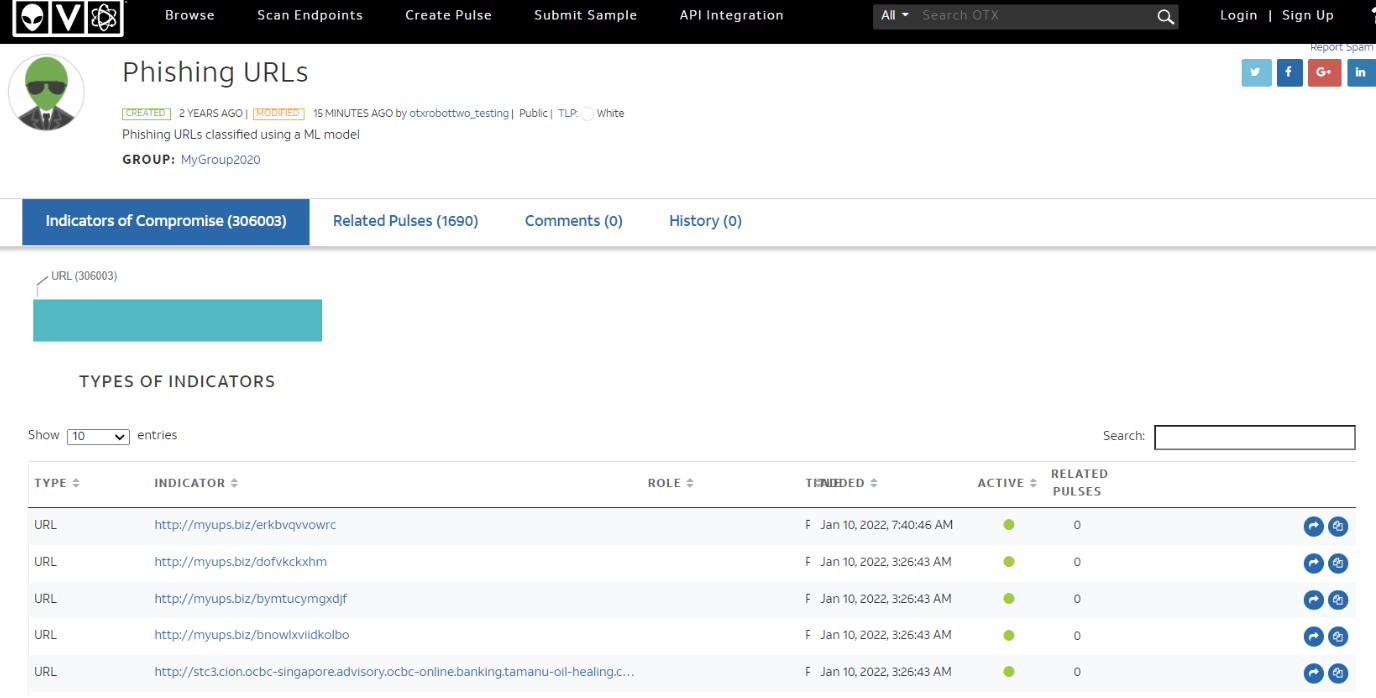
5. AlienVault OTX
AlienVault OTX is a threat intelligence community that enables collaborative defense with actionable, community-powered threat data. AlienVault OTX provides open access to a global community of threat researchers and security professionals.
Threat data is shared in form of Pulses on OTX. To stay up to date with other OTX contributors’ threat research, you can subscribe to their pulses. You can find pulses for phishing, IOC, domains / IP’s hosting malware, and much more on the AlienVault platform.
6. The Spamhaus Project
The Spamhaus Project is a non-profit organization that tracks spam and related cyber threats like phishing, malware, and botnets. It provides real-time actionable and highly accurate threat intelligence. Spamhaus also collaborates with law enforcement agencies to identify and pursue spam and malware sources.
Spamhaus offers various blocklists to detect and block domains with a poor reputation, IPs used in spam campaigns and IPs of hijacked PCs.

7. Phishing.Database
Phishing.Database is a repository for phishing domains, websites and threats.
Phishing.Database tests sources of phishing attacks to keep track of how many of the domain names used in phishing attacks are still active and functioning. The lists are updated hourly.

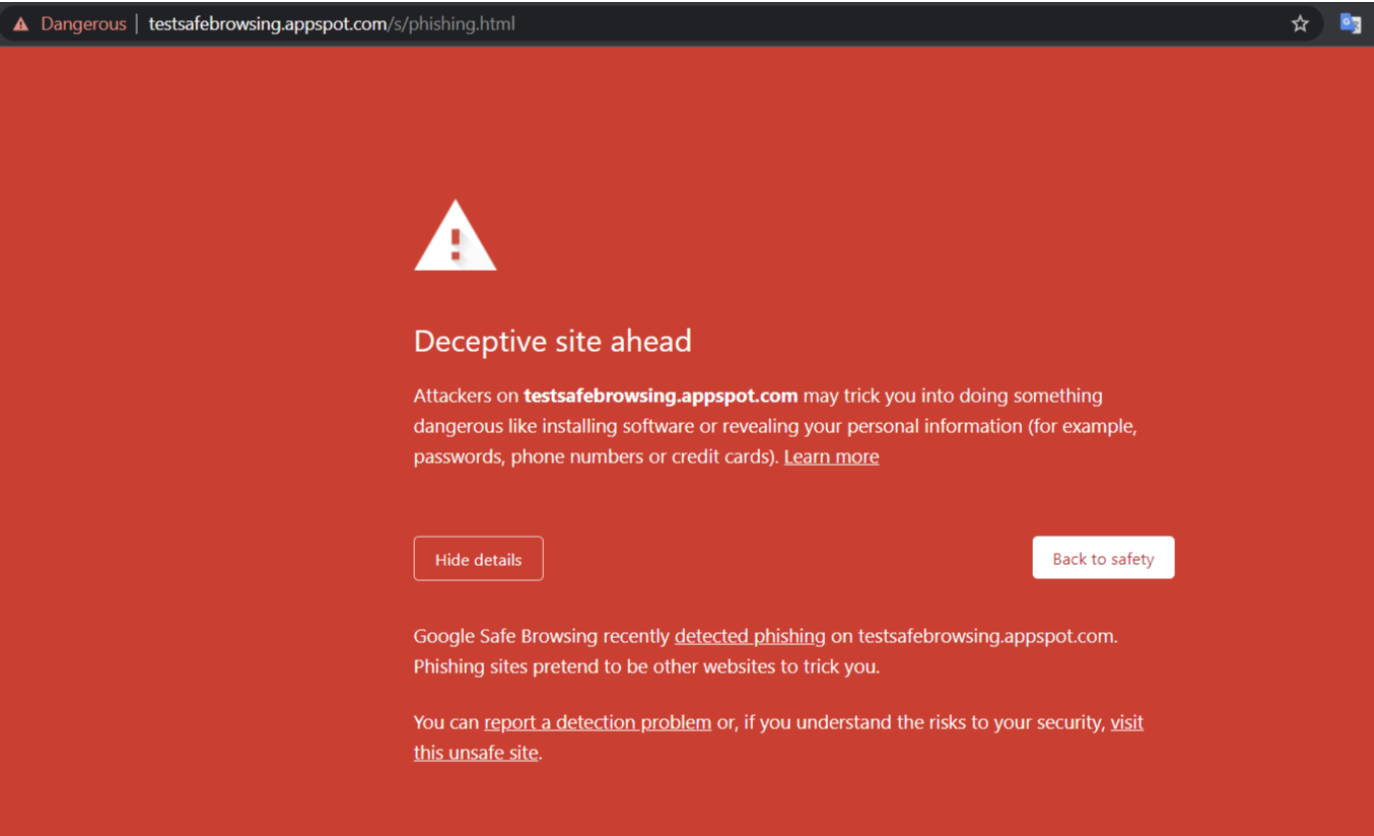
8. Google Safe Browsing
Every day, Google Safe Browsing protects over four billion devices by displaying warnings when users attempt to navigate to risky sites or download dangerous files.
Safe Browsing protection comes pre-built in the Google Chrome web browser. The Safe Browsing Lookup API can be used to verify if a site is possible phishing, hosting malware or scams.
Safe Browsing APIs are for non-commercial use only. For commercial purposes, such as sales or revenue-generating purposes available under the name of Web Risk API.
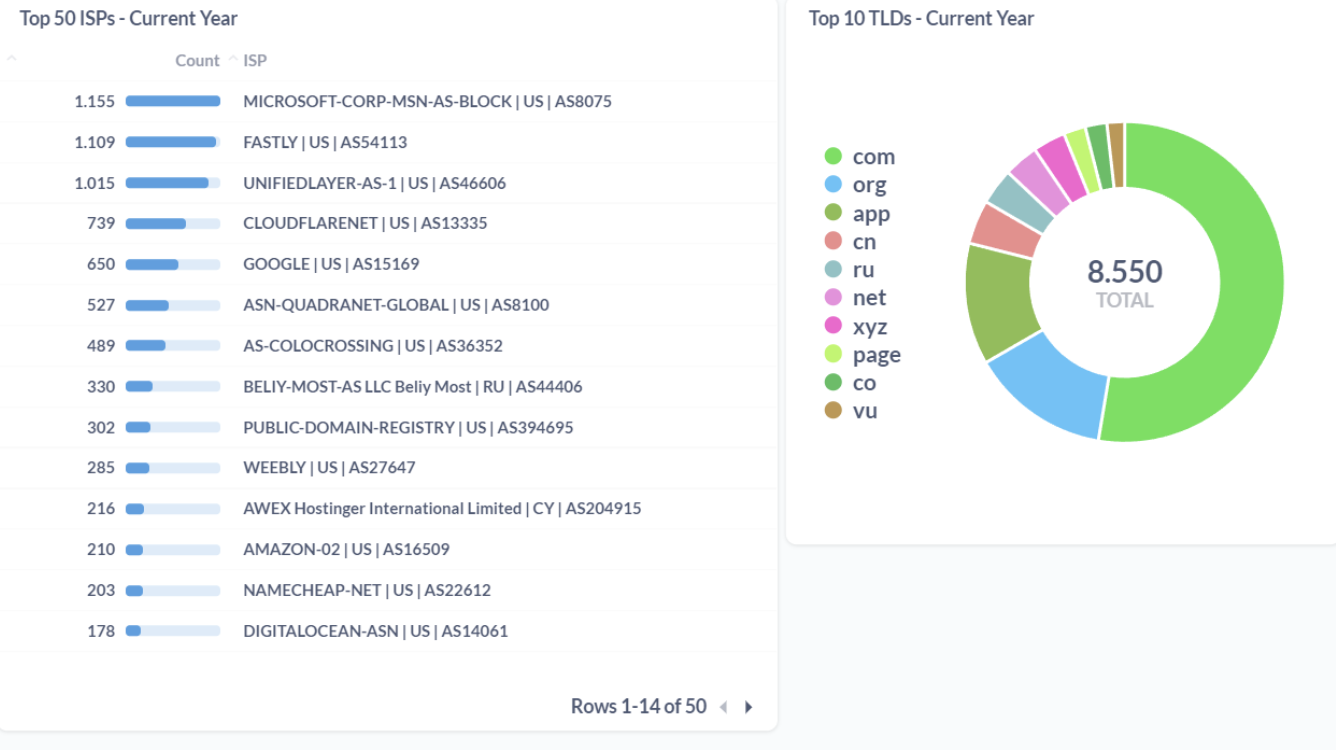
Comparing Phishing Threat Intel Data from Common Feeds
Data from PhishTank, OpenPhish Community Feed, PhishStats, Phishing.Database repo and 4 popular phishing AlienVault Pulses were collected to perform the below comparison. Collected URLs were then looked up in Google Safe Browsing API to check what percentage of URLs get flagged. Similarly, Collected domains were looked up in Spamhaus Domain Block List (DBL) and the results are as follows:
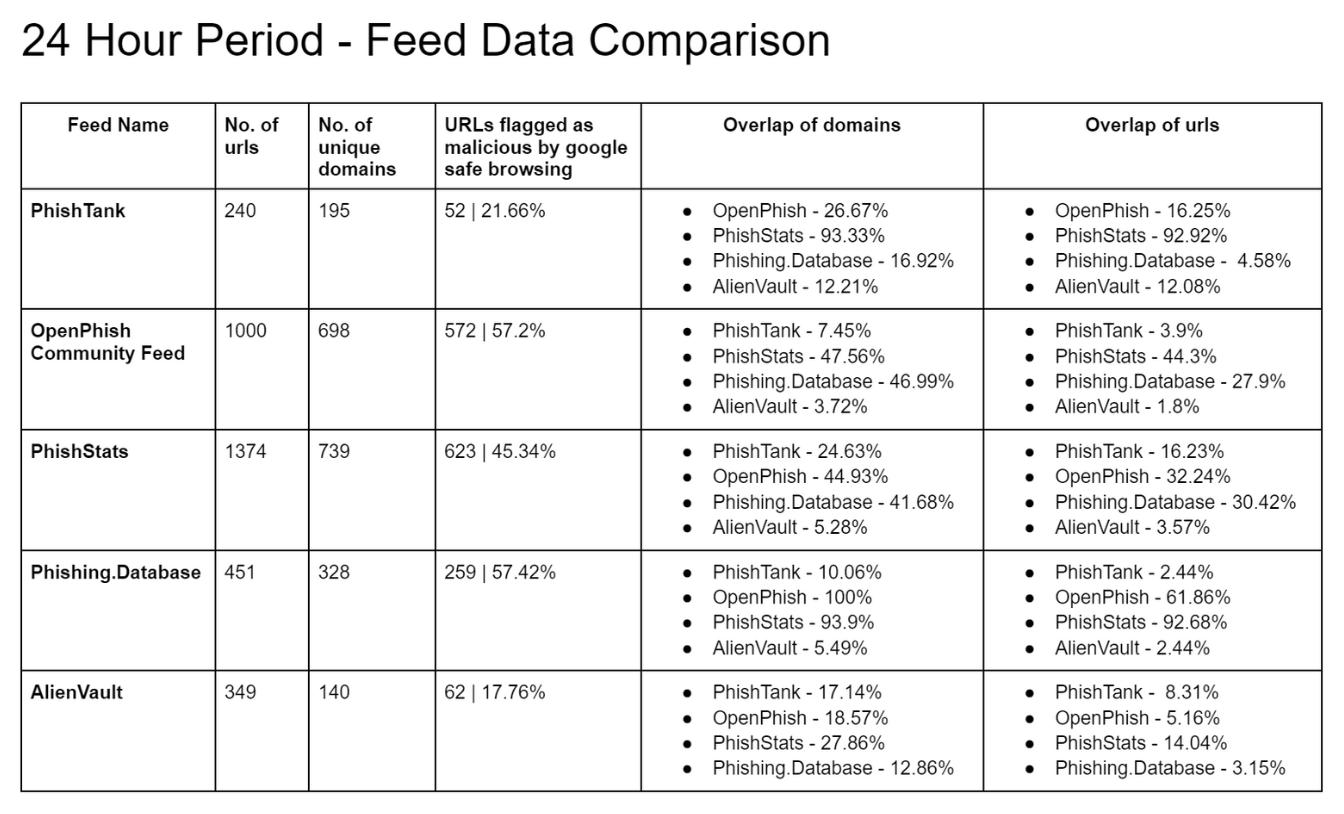
It’s noticeable from a comparison of feed data that data between certain feeds overlaps significantly. Implying that some common phishing detection techniques are being used by some feed operators. Phishing.Database has 92.68% URL overlap with PhishStats feed which is significantly higher.
Google Safe Browsing API was able to flag only 57.42% of URLs in case of data from Phishing.Database which was the highest detection rate for a feed. And for AlienVault phishing pulses data, only 17.76% of URLs were flagged as malicious.
Below are references for the collected data:
- PhishStats , Dashboards [1] [2]
- PhishTank, API
- OpenPhish, Global Phishing Activity
- AlienVault OTX
- The Spamhaus Project, DBL, XBL, PBL
- Phishing.Database
- Google Safe Browsing, API, Web Risk API
For more information on how a phishing threat intelligence program can protect your business from phishing threats, visit bolster.ai. Bolster provides a robust domain protection capability to monitor for threats targeting your brand, while also providing tools to monitor against threats on the dark web, social media scams, app store threats, and more. Learn more today.