New top-level domains (TLDs) like .zip and .mov have brought…
24 results for keyword "Phishing Attacks"
Personalized URL Phishing: Understanding the Threat of Email-Based Content Modification
In the ever-evolving landscape of cybersecurity threats, phishing remains one…
JavaScript-Enabled Phishing Attacks: Unmasking the Deceptive Layers of Malicious Sites
In the digital age, over 76% of businesses reported falling…
Credential Phishing Prevention & 10 Steps to Safeguarding Your Digital Identity
There might not be a word that hits harder in…
Six Examples of Impersonation Attacks and How to Shield Your Business
Impersonation attacks are smarter and more deceptive than ever, with…
How AI Email Security Safeguards Your Organization’s Communication Efforts
Even with the many apps, social media platforms, and other…
Crypto Deceit: Fending Off The Phishing Nets Targeting Digital Assets
The growing allure of cryptocurrencies draws both investors and cybercriminals…
Scamming the Scammers: Phishing Kit Creator is Stealing the Telegram Token from Scammers
At Bolster Research Labs, we recently observed that phishing kit…
2024 State of Phishing & Online Scams: Statistics, Facts, Trends & Recommendations
From prompt responses to self-driving cars, 2023 felt the significant…
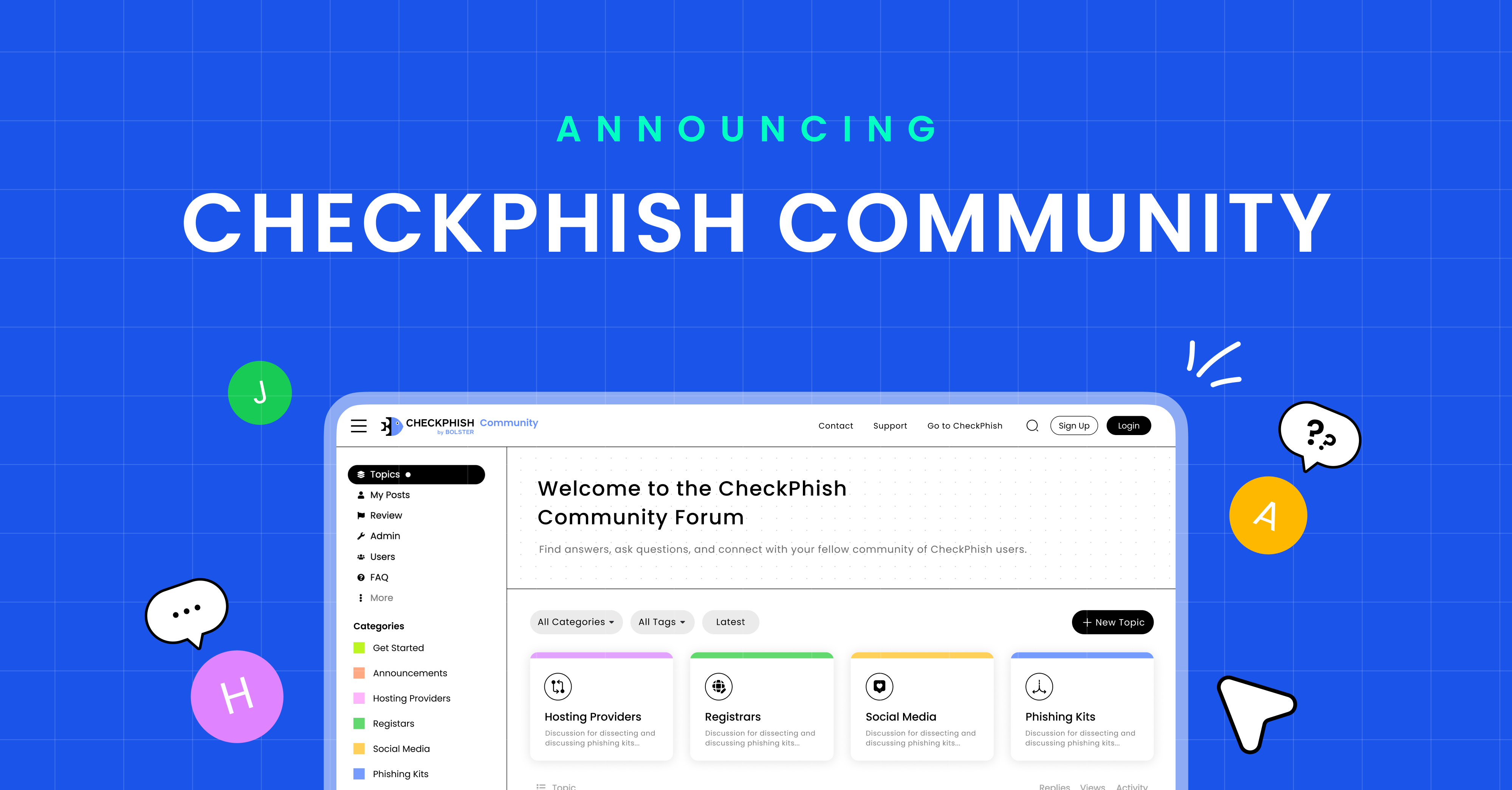
Announcing Bolster Community Forum
In the rapidly changing digital landscape, the cybersecurity community confronts…
What is Vishing and Is It A Threat to Your Business?
What Is a Vishing Attack, and What Does It…