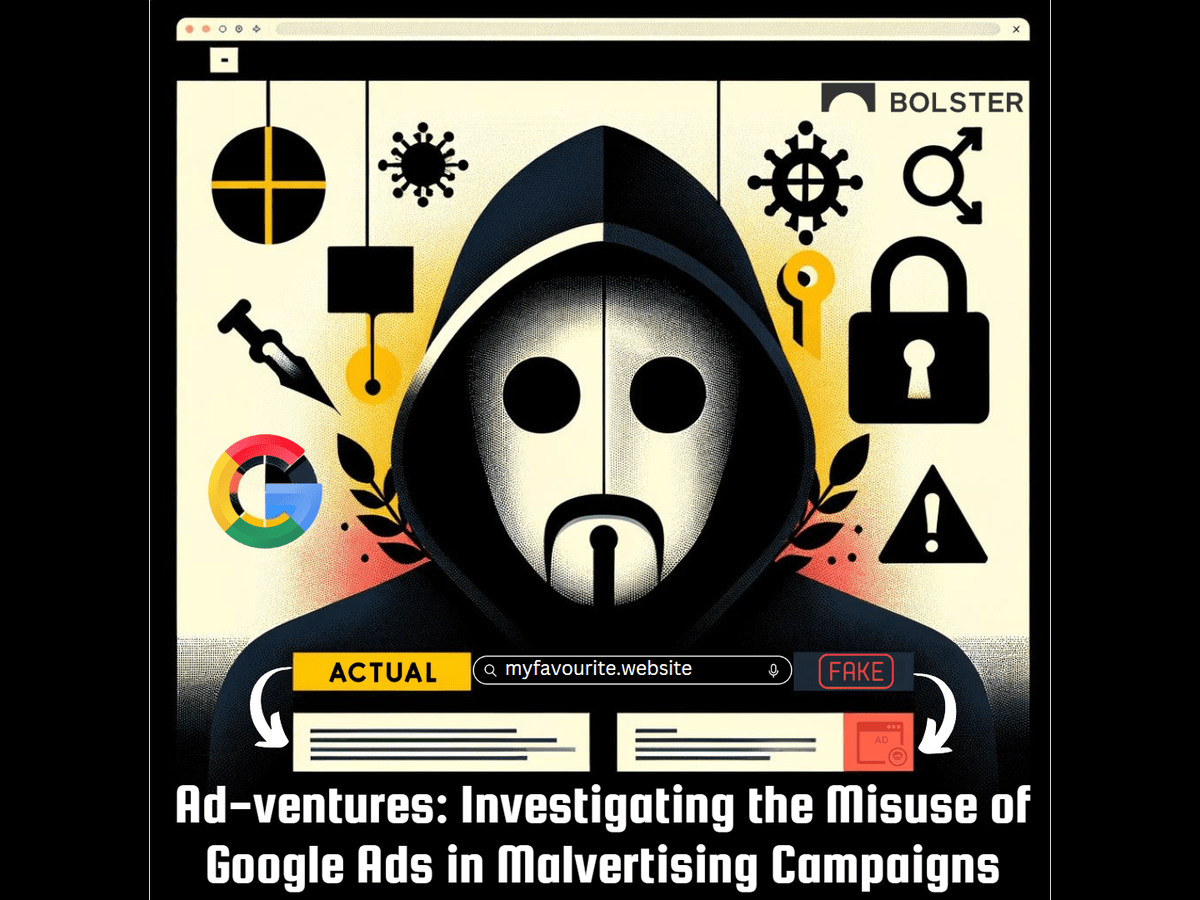
In the sprawling extent of the internet, Google Ads has…
67 results for keyword "Research Labs"
Beyond Phishing: The Rising Threat of Stealer Logs Compromising Security
The arms race between cyber defenders and attackers is becoming…
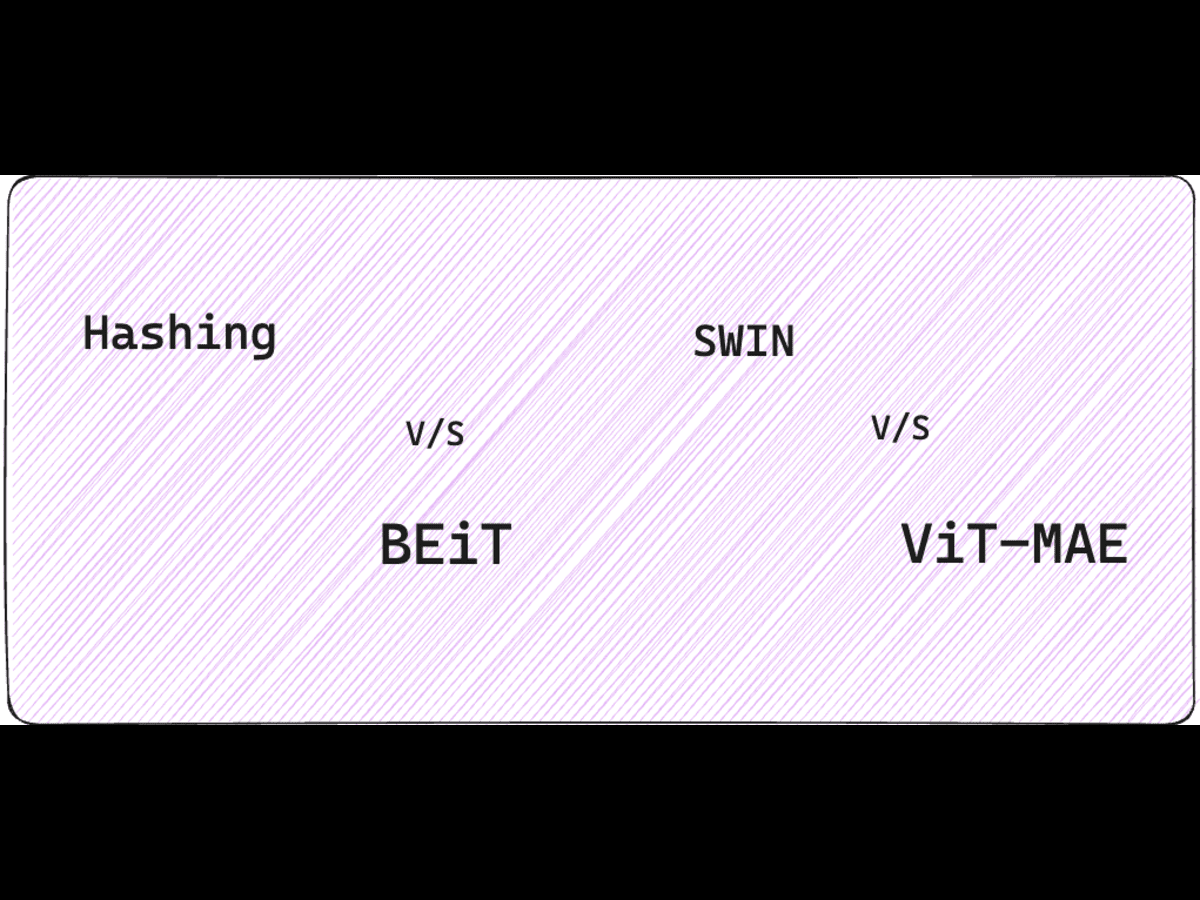
Image Similarity for Brand Detection: A Comparison Between BEiT, SWIN and ViT-MAE
Brand detection is a critical component of Bolster AI, gathered…
Phishing in Disguise: Threat Actors Turning Legitimate Sites Into Antivirus Traps
Antivirus vendors have significantly been impacted by the latest phishing…
Dissecting the Phishing Kit behind the Axis Bank Reward Points Campaign
Phishing campaigns targeting banking and financial institutions have always been…
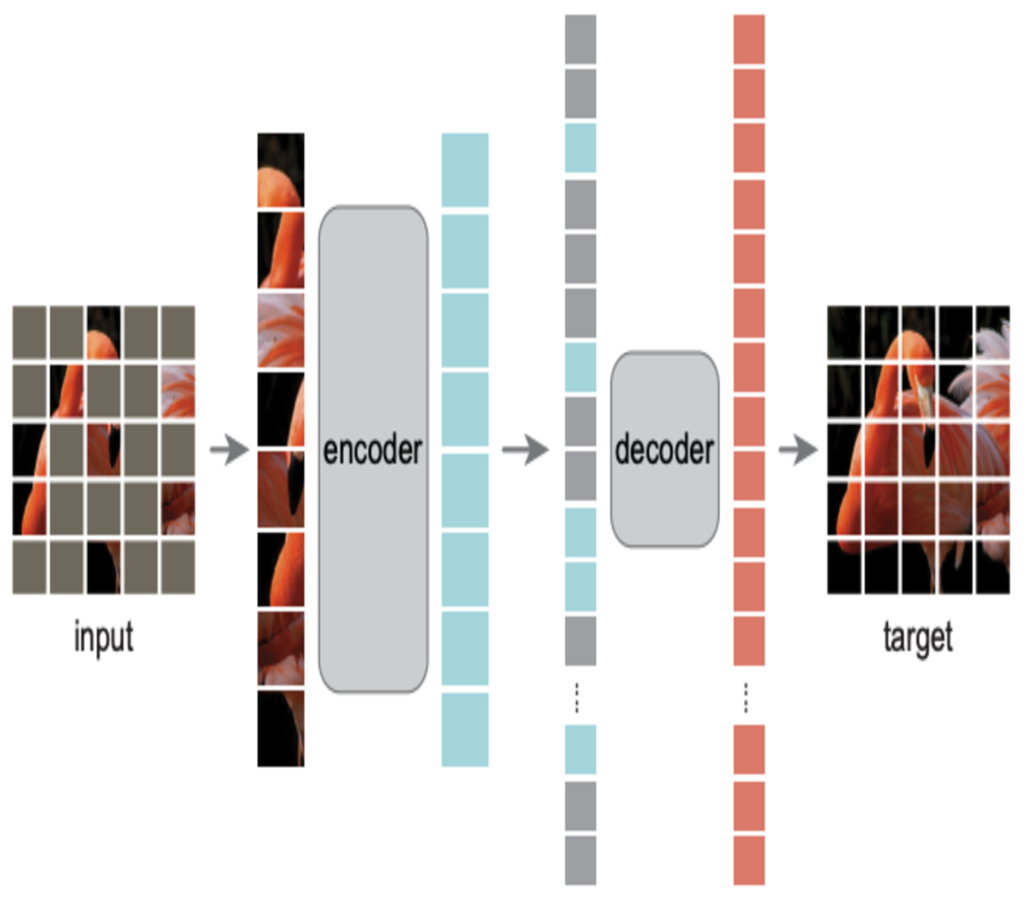
VIT-MAE: Scalable Learning for Vision Transformers
Unprecedented gains in hardware capabilities and model sizes have compelled…
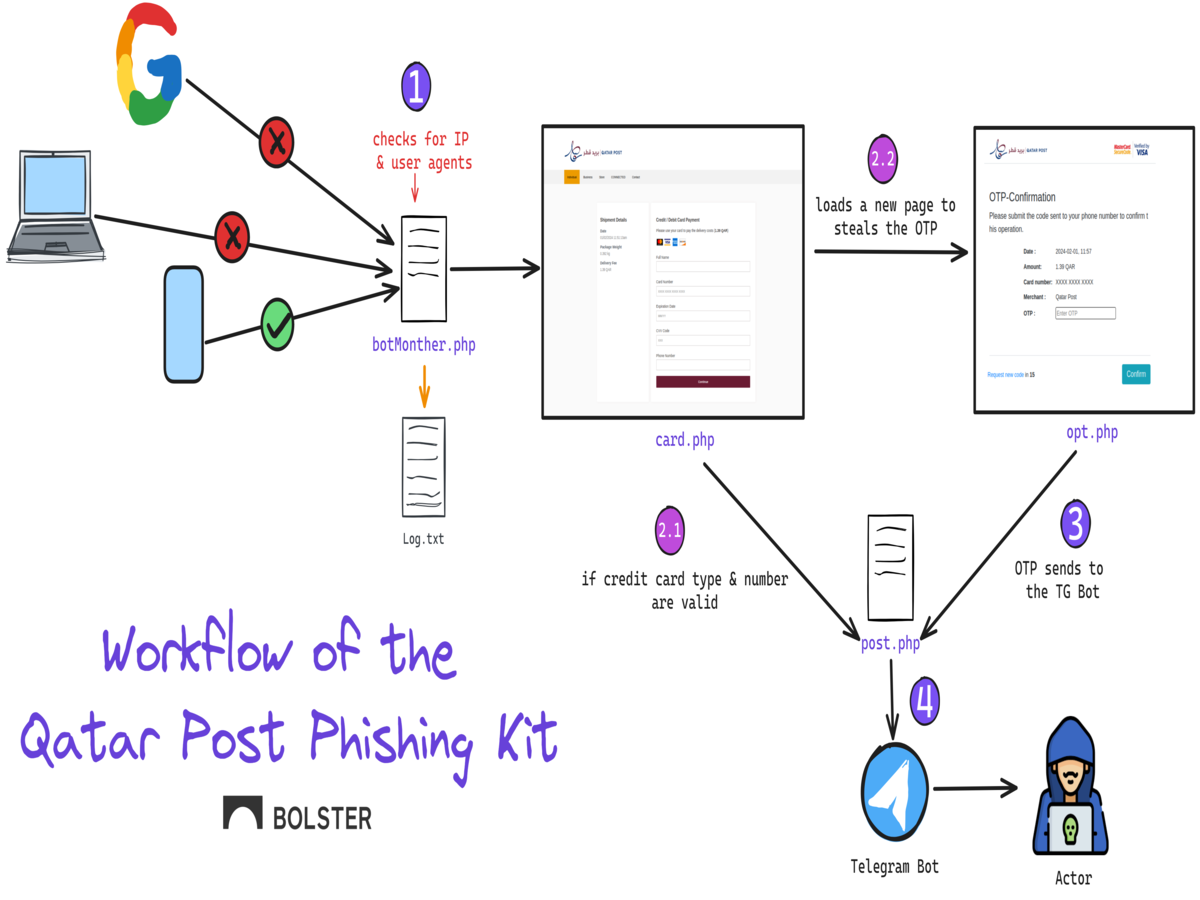
Dissecting the Newest Phishing Kit Targeting the Qatar Post
Name brand postal services have been increasingly targeted by phishing…
The Dark Underbelly of the Internet: Bulletproof Hosting and Phishing Epidemic
What is Bullet Proof Hosting [BPH]? Within the digital community,…
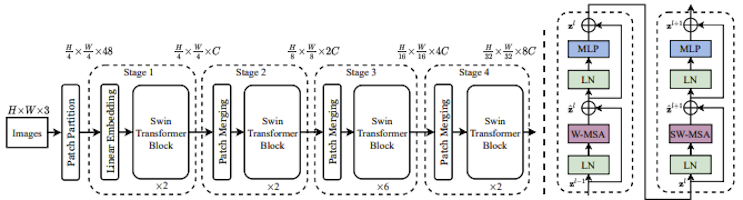
SWIN Transformers: The Best of Two Worlds
The search for a transformer based backbone model suitable to…
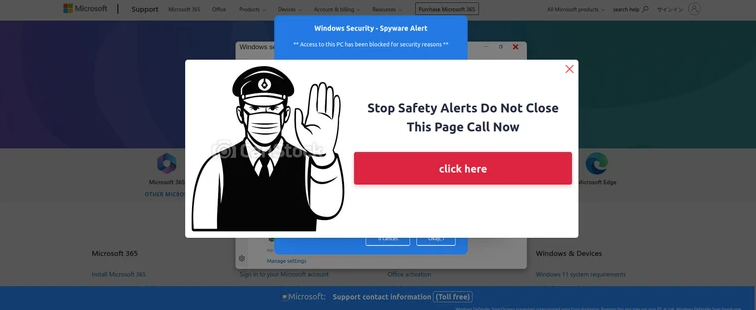
Analyzing Advanced Multi-Lingual Tech Support Phishing Kits Hosted on SaaS Providers
The Tech Support Scam consistently remains in the spotlight due…
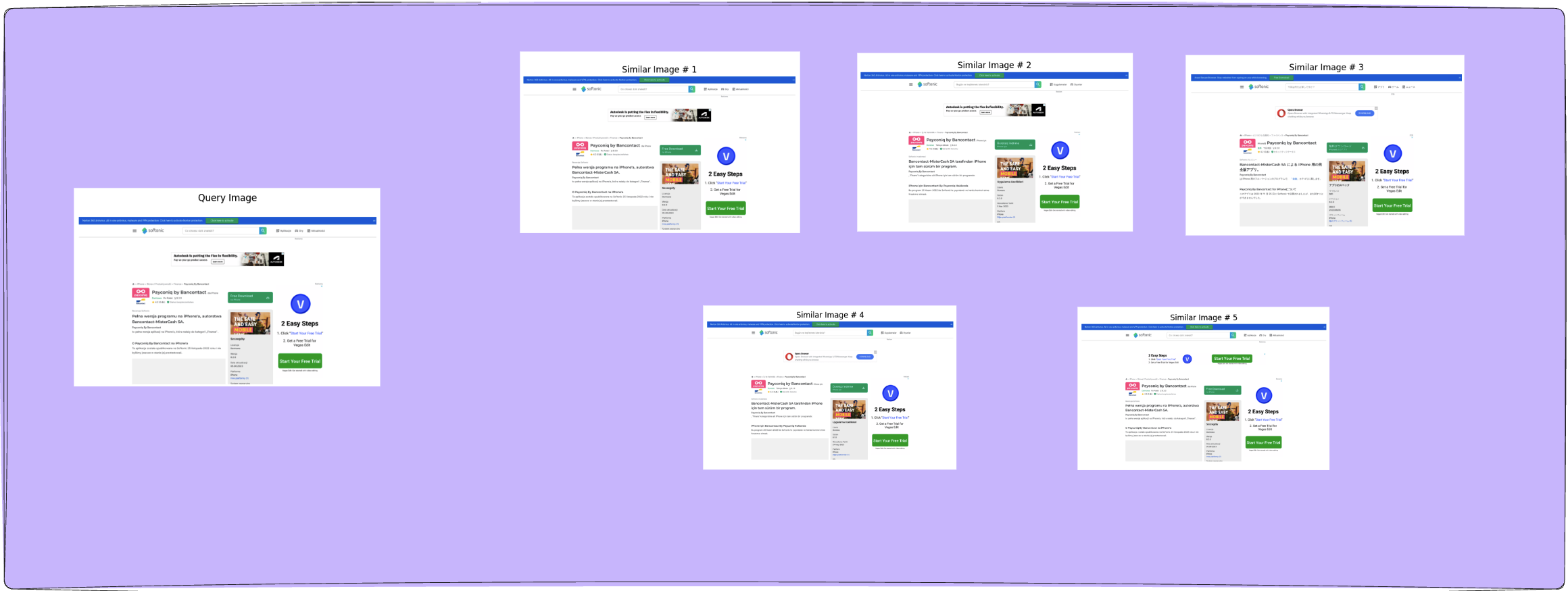
Beyond Hashing: The Future of Anti-Phishing is Image Similarity Search
Computer vision modules are a critical component in a cybersecurity…
BERT for Image Transformers (BEiT) : A Definitive Guide to Computer Vision Breakthrough
Convolutional Neural Networks (CNNs) have dominated the computer vision landscape…