If you have an online presence, chances are your brand, or more specifically your Internet domain, is a target for cybercriminals. Cybercriminals have a distinct advantage using typosquatting techniques to stage high-volume web-based attacks. This makes for a tricky website takedown process for businesses trying to combat typosquat domains quickly, while new ones are popping up around them.
So how do you conduct website takedowns for malicious domains? Well, the short answer is not easily, especially if there are a lot of typosquat domains to contend with and you plan to do it manually. But let’s say you are ambitious and do try to take it on. Here’s how to take a malicious website down, the hard way. Keep in mind these steps are for just one individual website takedown. If you have multiple sites to take down, you’ll need to repeat these steps for every website takedown.
The 5 Not-So-Easy Manual Steps to Takedown a Malicious Website
Step 1: Discover malicious site
Sure, it’s the obvious starting point for this exercise before you can even begin conducting a website takedown, but finding a malicious site is not necessarily easy. Some compare it to trying to find a needle in a haystack. The best way to find a malicious site is by having a Domain Risk Management practice in place, to proactively discover and track the weaponization of a site that is now candidate for takedown. Without a practice in place, malicious sites will go undetected until they’re live and doing their damage. Either way, by finding it proactively (hopefully) or while under attack, you’ll need the URL (or set of URLs) to launch your investigation.
Step 2: Inspect URL
With URL in hand, the next step is to inspect it for signs of phishing or fraud. For this, do not simply open up a browser and key in the URL. Use a proper URL scanning tool like CheckPhish (www.checkphish.ai) to properly and safely inspect the URL. With CheckPhish you’ll get an instant verdict with detailed evidence, including all the network and hosting provider information, geo-location, plus a screenshot of the site. This information will serve as your critical evidence when building the case for a website takedown.
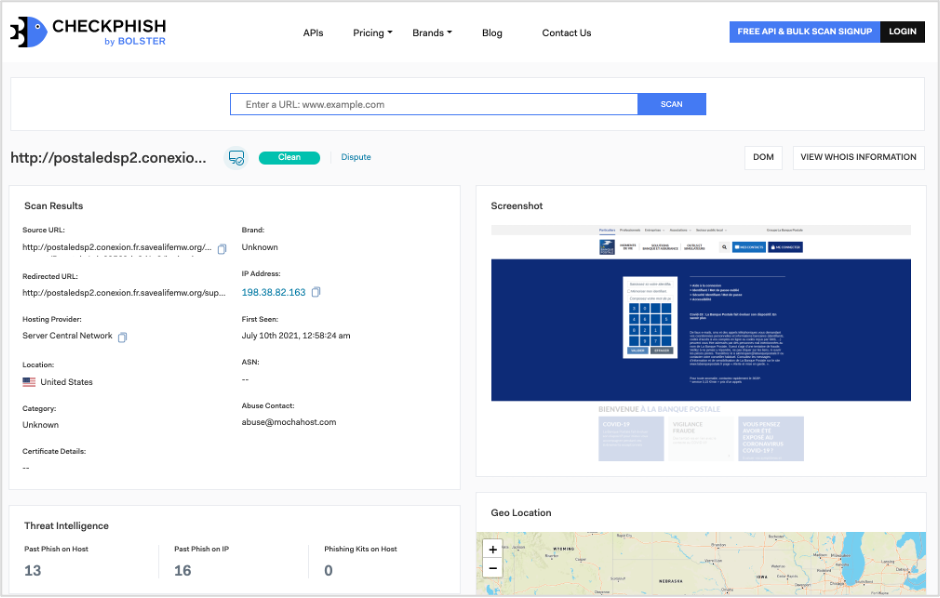
Step 3: Report abuse, submit evidence
With evidence collected, next step in the website takedown (the harder version) is to report abuse and pursue a site takedown. If you visited CheckPhish, or another phishing detection site, and did a URL scan you’ll see there is a field for “Abuse Contact”. You’ll need that to start the email process. It is important to use a tool that helps provide this contact information, or else the work might be harder on your internal team to track down the point of contact while knowing the malicious site is active and mimicking your domain.
Include in your email as much evidence as you can supporting the site takedown: signs of credential theft (login fields), logo abuse, invalid URL. Additional supporting evidence such as Passive DNS information, presence of phishing kits and more can be found as part of the CheckPhish scan results to help strengthen your case.

Step 4: Wait
With evidence submitted it’s now a waiting game. Action could occur within a few hours if you’re lucky, but chances are this step will take days.
Hosting providers will act the fastest and help conduct a website takedown when presented with phishing sites and solid evidence. But in many website takedown cases, and especially when evidence gets murky, the process can be quite drawn out. It’s not uncommon for this step to take a week or two, or even longer. Persistence will be the name of the game to see things through to a successful website takedown.
Step 5: Monitor takedown
If you’ve gotten to this point, and successfully taken a malicious website down, the next step is to monitor the Internet to make sure the site doesn’t simply reappear on another hosting provider’s network.
Many describe it as a potential game of whac-a-mole™—take a site down, see it pop back up somewhere else, take it down again, see it pop up yet somewhere else, take it down yet again. Without monitoring the takedown for reoccurrence, this game will persist, leaving you chasing your tail.
Step 6. Repeat for other malicious sites
Most likely, if you’ve come across a malicious site stepping on your brand and business, there are more. In the current digital economy, bad actors know how lucrative fake sites can be, so while you’re spending time taking down one site, it’s highly likely more are becoming active behind your back. For the ones you do find, repeat Steps 1-5 for a website takedown.
When Things Get Tricky: The Pain-Points of Manual Takedowns
The above steps will work for the most part with time and patience, but things can get tricky the more malicious sites pop up, and the harder it becomes to effectively conduct a website takedown. Here’s some pain points your cyber risk team might experience:
First, if you’re dealing with a brand or trademark infringement, or even counterfeit sales, the takedown process will invariably take longer, and reporting abuse alone will not be sufficient. In many of these cases you will need to enlist legal support to also issue ‘cease and desist’ notifications to various parties. This will invariably require more time, and of course more money. But don’t lose hope, these techniques can be successful in conducting website takedowns, just expect it to be time-consuming and most-likely costly.
Situations can also get tricky if you’re looking to takedown a site hosted in a not-so-friendly place in the world. Some countries are less stringent about enforcing abuses, making takedowns more challenging unless you know the ins and outs of various demographic regions. In some cases, you may need to work with country-specific anti-abuse authorities to report abuse and see a site through to takedown. Seeking professional assistance with the takedown, or set of takedowns, is highly recommended.
Website Takedown Support: What to do When You Can’t Get a Response
If the hosting provider is entirely unresponsive, you may go up the food chain to the registrar that issued the domain. Working with registrars will be time-consuming, especially if you have no prior relationships. The initial steps will be the same; gather evidence, report abuse. To get the abuse contact for the registrar, you can do a simple ‘whois’ on the malicious domain.
You may also ask about Uniform Domain-Name Dispute-Resolution Policy (UDRP) style takedowns, and whether that approach can be deployed. The short answer is ‘possibly’. UDRP takedowns are time-consuming and can be costly since they are resolved by agreement, court action, or arbitration before a registrar will cancel, suspend, or transfer a domain name. So, if you are under attack and have a lot of sites to contend with it will not be the fastest approach to employ.
And what about a Digital Millennium Copyright Act (DMCA) style takedown you may ask? Is that an option? Short answer here is ‘yes, but’. A DMCA Takedown Notice is a specific type of takedown for copyright infringements in the United States. DMCA takedowns are effective, but they are time consuming, and enforceable only in the United States. Some countries will comply based on copyright abuse, but there is no legal obligation. To start, you’ll need proof of the copyrighted content. Additionally, since a DMCA takedown notice is a legal notice, specific legal language and information is required, including location of the original copyrighted works, location of the infringing content, a “good faith belief” statement and “under penalty of perjury” statement.
Conducting a Website Takedown: The Right Way
Hopefully you’ve come to appreciate the steps and evidence required to conduct a malicious website takedown manually. With time and patience, it can be done. But, if you’re dealing with a lot of sites, or sites in geos where abuse is harder to enforce, or what is often the case, a combination of both, then you should really consider enlisting professionals.
We put together a guide for handling website takedowns the right way, which in our minds is the more efficient, cost effective, and reliable process businesses should take. Our Bolster technology automatically scans the internet daily for typosquat domains and brand infringement, and can conduct automatic website takedowns on your business’s behalf.
To learn more about about Bolster’s domain monitoring, read our whitepaper: Guide to Domain Monitoring and Remediation
Learn more:
Bolster Auto-Takedown solutions
Bolster Domain Protection solutions
Bolster Brand Protection solutions
Bolster Phishing & Fraud Protection solutions
Request a demo & free trial: Free trial









