Business Email Compromise
A preventative, proactive approach to stop BEC attacks at the source. Utilizing an AI-based BEC detection and defense engine, Bolster powers quick identification and takedown of attacks at the origin point.
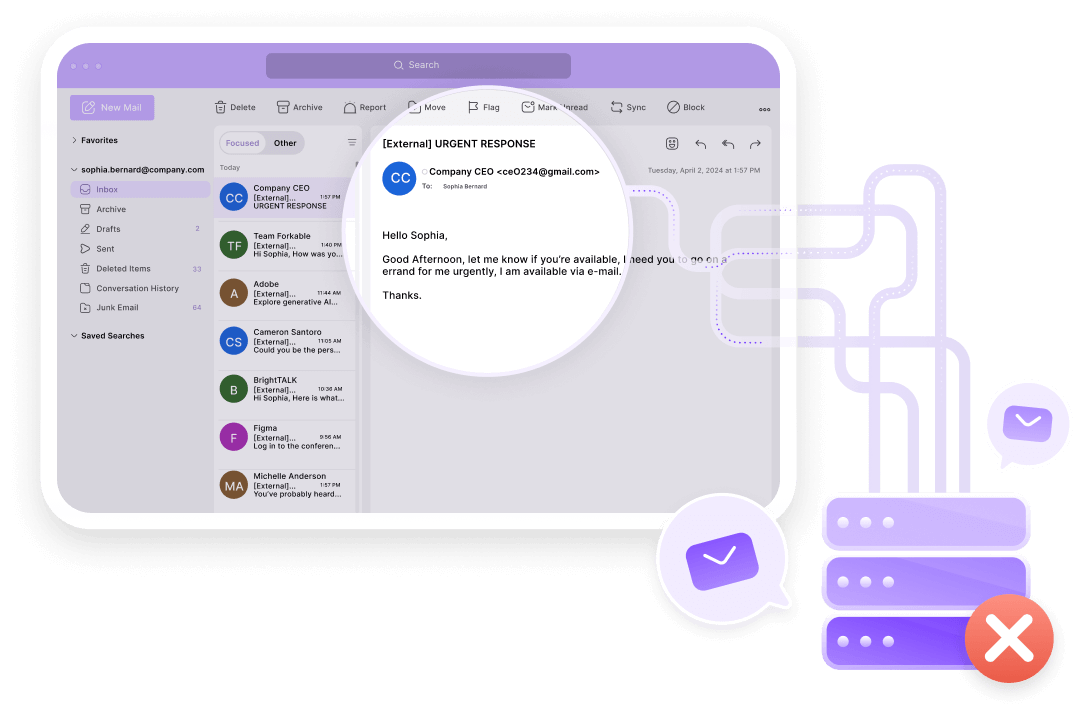
Business Email Attacks Are Easier to Launch with AI
AI is enabling attackers to register domains, add MX servers, and send out malicious emails and links at an alarming pace.
BEC was the top threat to businesses in Q1 2024, making up nearly half of all attacks, more than twice the previous quarter
Source: Bolster 2024 Phishing and Scam Report
BEC scam reported losses were over $2.95B in 2024
Source: Bolster 2024 Phishing and Scam Report
BEC makes up 40% of successful social engineering attacks
Source: Bolster 2024 Phishing and Scam Report
94% increase in unique phishing attacks since 2020
Source: Bolster 2024 Phishing and Scam Report

How to Better Protect Your Business from Evolving Email Attacks
BEC Prevention is more than just protecting your inbox; read our whitepaper to learn how to stop email attacks at the source.

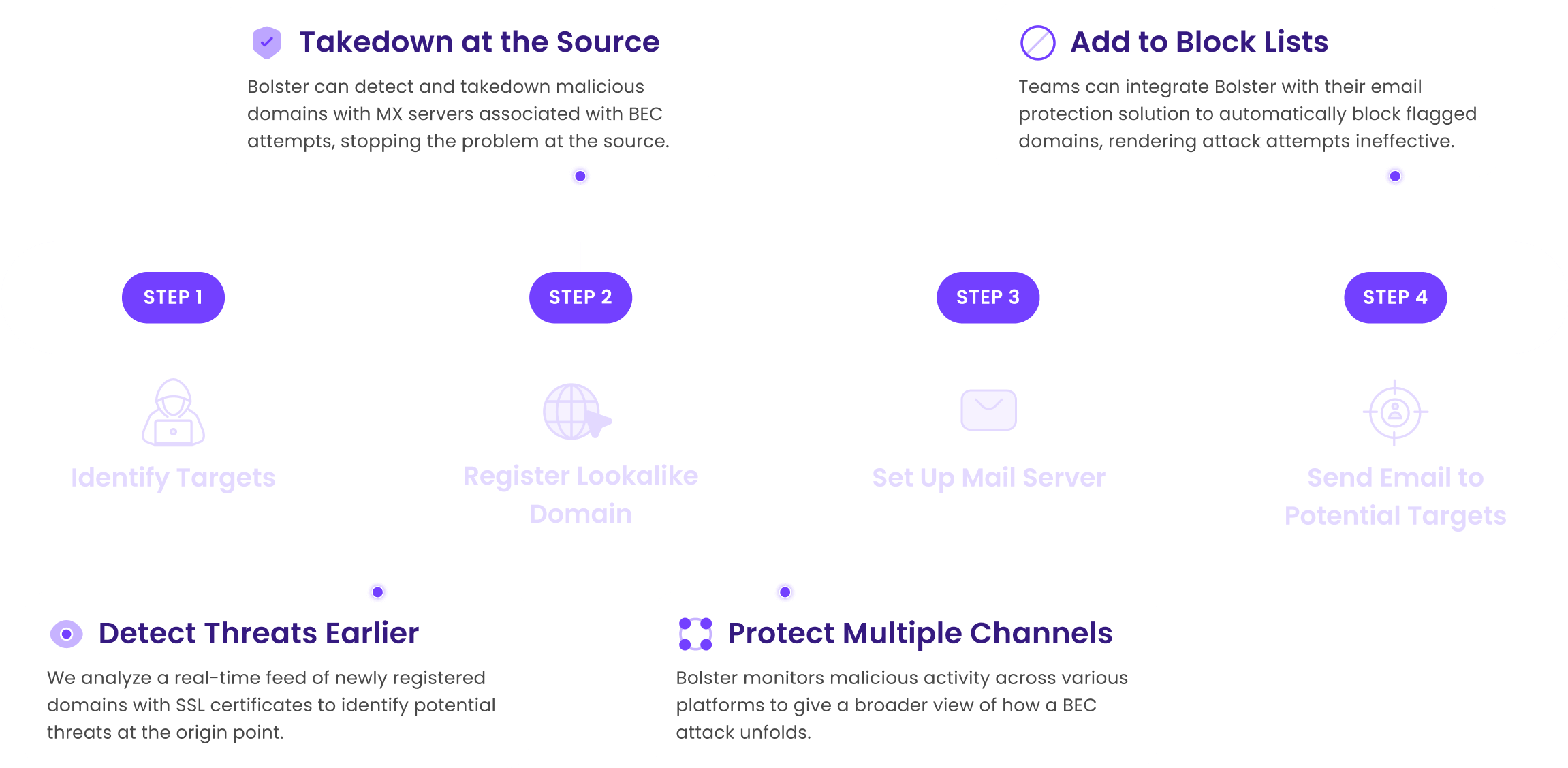
Bolster Proactively Stops BEC Attacks Early in the Attack Chain for Better Email Defense
Bolster’s AI-powered BEC monitoring, and defense solutions take at preventative, proactive approach, that stops BEC attacks at the source. Utilizing an AI-based detection engine to quickly identify malicious domains behind a BEC attack, Bolster takes down threats faster and where it has a bigger impact.
Bolster uses a combination of proactive approaches to BEC defense to protect customers from maturing email attacks.

Strengthen Your Email Protection Program with Bolster BEC Defense
Protect Employee and Customer PII
When BEC attacks are successful, it can mean your employee, customer, and partner data ends up in the wrong hands. Protect the PII of those that matter to your business with the right detection and takedown technology.
Maintain Your Status as a Trusted Brand
Fake accounts and messages targeting those close to your business can leave a sour taste in the mouth of potential customers, employees, and business partners. Maintain your brand reputation by quick identification of BEC threats.
Shield Your Organization from Financial Loss
With a focus on bank account and payroll data, the impact of BEC attacks can be truly detrimental to an organization’s finances. Provent costly attacks on your business with the right AI-powered BEC defense.
Stop Threats Earlier In the Attack Lifecycle to Reduce Total Impact
Stopping BEC campaigns at the source means that there is a smaller chance of a large-scale data breach and less exposure for your organization.
Guides and Resources
Bolster your digital risk protection program and learn more about industry trends and managing threats.
Ready to get started?
Explore what Bolster AI can do for you with a custom demo for your online business to understand existing online threats and how Bolster can take them down. Contact our sales team for pricing and packages today.
Get 24/7 Support
Our global team of highly skilled SOC experts work around the clock to provide high-quality assistance.
Easy Product Guides
Self-guided documentation gives you step-by-step support to quick integrations or issue resolution.
Frequently Asked Questions
What is a Business Email Compromise (BEC) Scam?
Business Email Compromise (BEC) scam is a type of cybercrime that aims to trick individuals or companies into making fraudulent payments, disclosing confidential information, or initiating unauthorized wire transfers. BEC scammers typically use email spoofing to appear as legitimate senders and trick their targets into performing actions that benefit the attackers. According to the FBI, BEC is one of the most financially costly crimes, resulting in more than $13 billion in losses globally from October 2013 to July 2019.
What is Account Takeover Protection?
Account takeover (ATO) protection is a type of cybersecurity solution that safeguards user accounts against unauthorized access by cybercriminals. ATO protection solutions use various authentication methods, such as two-factor authentication, artificial intelligence (AI), and machine learning (ML), to detect and prevent ATO attacks. By controlling access to sensitive information, ATO protection technology helps to prevent unauthorized changes, unauthorized monetary transactions and maintains the credibility and confidentiality of business information. In the context of BEC scams, ATO protection systems help to safeguard against attacks aimed at gathering login credentials to hijack email accounts and execute fraudulent payments.
How do BEC scams target your business?
BEC scammers use various techniques to target businesses, but the most commonly used technique is spear-phishing. Spear-phishing is a tactic that involves creating emails or websites that appear legitimate and trustworthy to the targeted users, making them more likely to click links, open attachments, and share confidential data. Sophisticated social engineering techniques are employed to convince a target of the legitimacy of these emails and sites. These emails and websites can be used to gather user login credentials, initiate fraudulent transfers or redirect financial data. The impersonation of high-level executives within an organization is also a recurrent strategy used by BEC actors.
How does Bolster protect against BEC scams?
Bolster is a digital risk protection platform that uses AI, ML, and natural language processing techniques to detect and prevent BEC scams. Bolster’s solution performs continuous, real-time internet scams across business domains and like domains, evaluates sender and domain reputations and risk levels, detects suspicious activity, and blocks potential fraud attempts. Bolster acts quickly to detect malicious account activity and misuse of your company or executive branding before fake accounts can actively deceive your audience. The solution can be deployed quickly to integrate with the business’ current workflow processes to provide extra security coverage where it is needed.
What attack vectors does Bolster integrate with?
Bolster protects against various attack vectors, including phishing emails, links, malvertising, social engineering tactics, domains, and mobile app threats, and threats across 18 of the major social media platforms. Bolster delivers real-time threat analysis and machine learning for customers to protect against the latest and most complex threats, ensuring that businesses remain protected from the latest scams even as they evolve.
How quickly can Bolster be implemented within our organization?
Enterprises worldwide reel under the challenge of brand impersonation, suffering monetary and reputational damages. Brand loss is driven by a proliferation of scams and counterfeit sites.
Bolster’s brand protection solution detects and takes down sites misusing your brand, including fake domains, third-party sites, unauthorized apps, and search engine results.
We use the most advanced AI technologies and automation to detect infringements in real-time to protect the sanctity of your brand identity.
Why do I need BEC scam protection?
BEC scam protection is necessary to help businesses safeguard themselves against cybercriminals and prevent financial losses. BEC scammers’ tactics are becoming more advanced and sophisticated, making it challenging for businesses to detect and prevent BEC attacks. According to the Federal Bureau of Investigation (FBI), BEC has resulted in global losses of over $12 billion since 2013. Investing in BEC scam protection solutions, such as Bolster, helps businesses detect and prevent BEC scams and stay ahead of these threats.