Fake App Monitoring and Takedowns
Stop App Store Threats From Mimicking Your Business and Damaging Your Reputation.
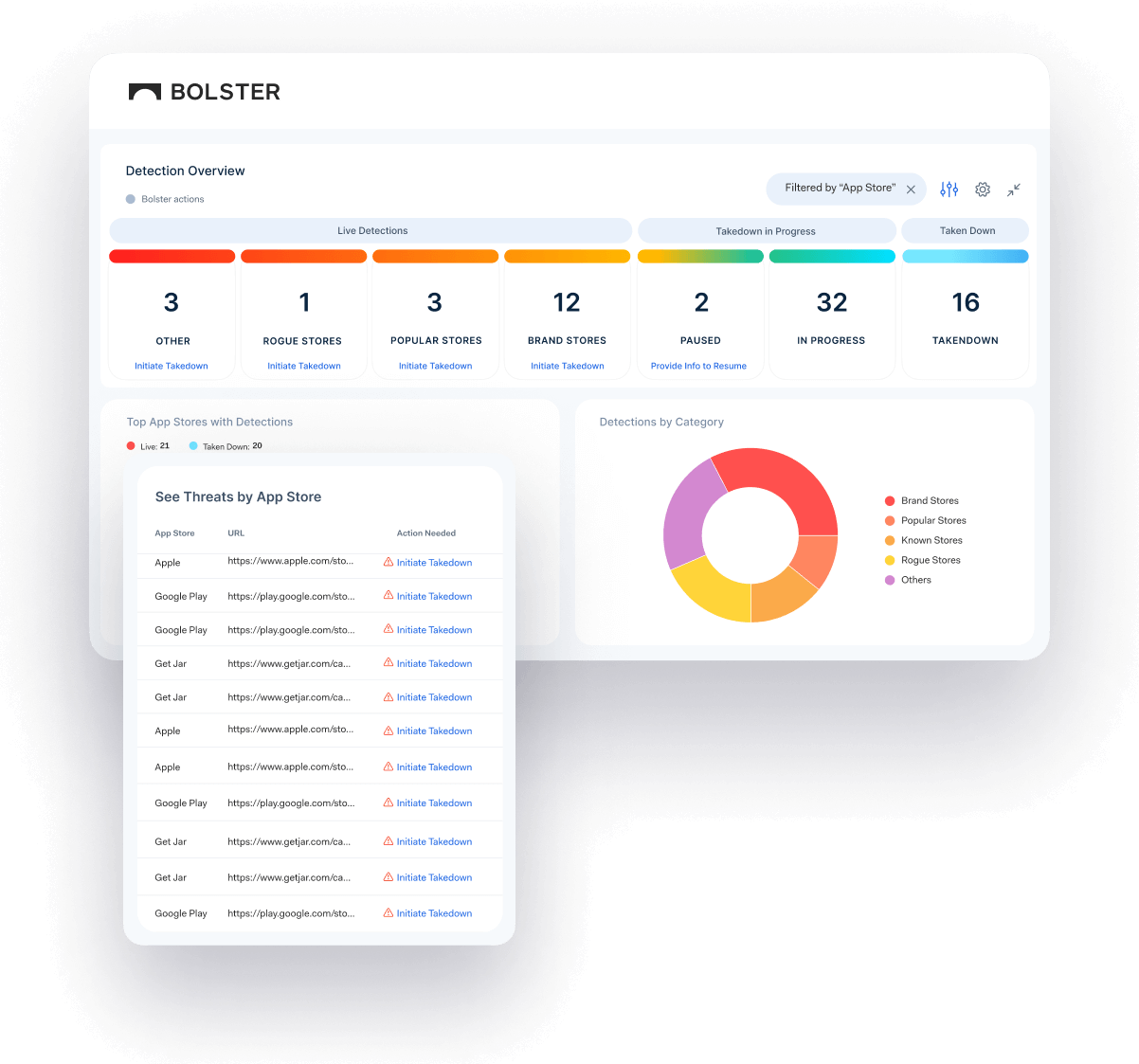
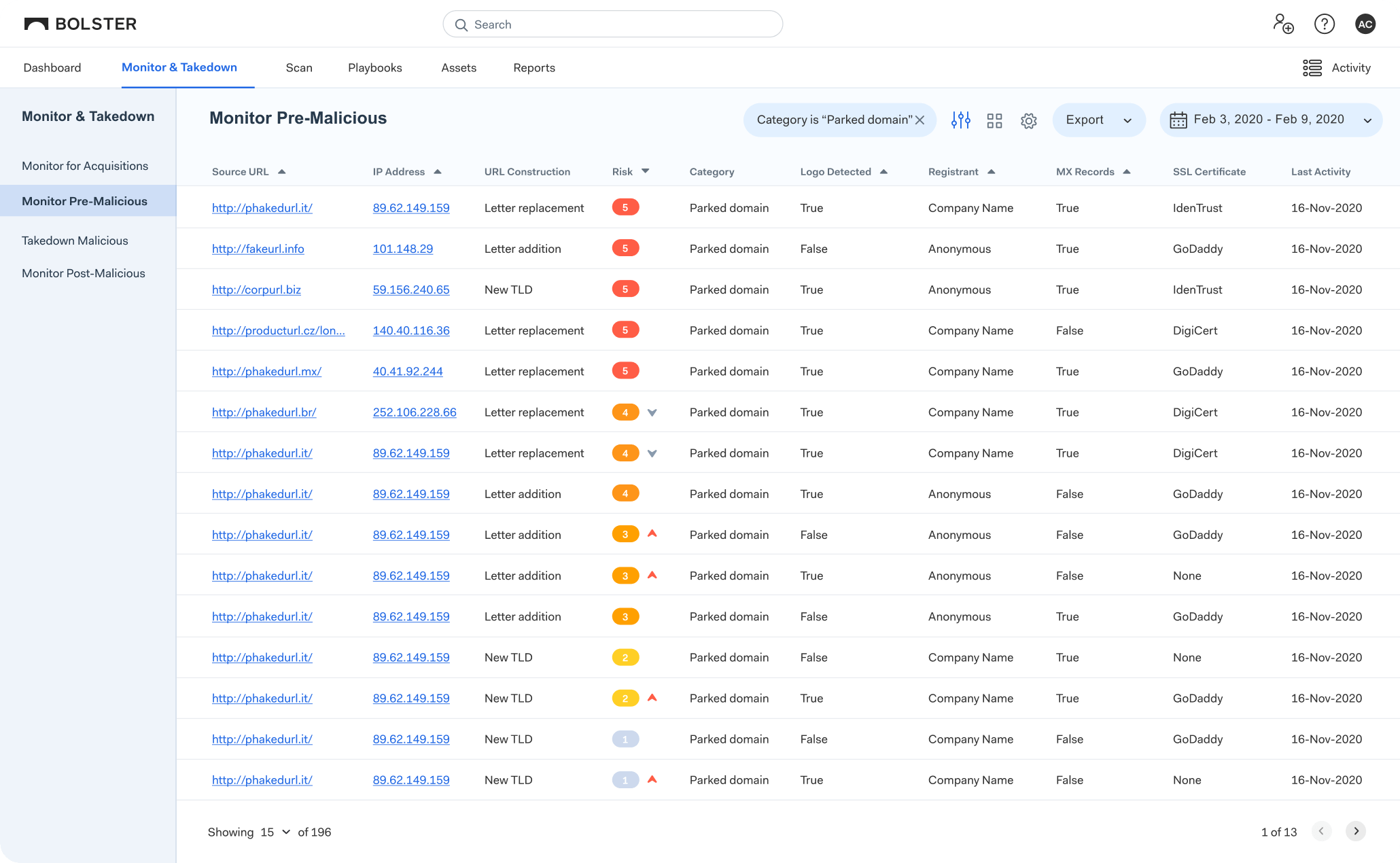
Continuous Fake App Monitoring and Takedown Across All Major App Stores
In today’s digital landscape, businesses are faced with evolving fake app threats on app stores. We’re talking fake and rogue apps created by hackers to mimic your legitimate app, using malware, phishing, intellectual property infringement, false or misleading advertising, all to gain unauthorized access to sensitive information and consumer data. The effects can be damaging to brand reputation and customer trust.
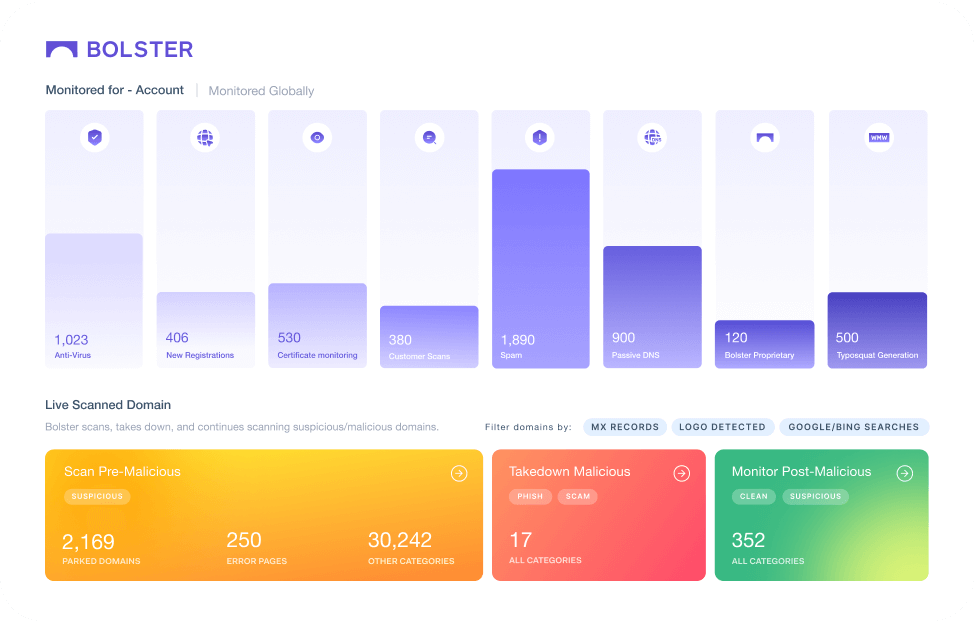
With Bolster App Store Monitoring, you’ll get immediate visibility and control. We actively monitor over 500 app stores for uses of your brand and fake app store postings that aren’t yours. And, we take down the fake apps immediately, stopping damage before it’s done.
Stop Fake Apps In Real-Time with Bolster App Store Monitoring & Takedowns
With Bolster App Store Monitoring you can trust that fake or rogue apps are taken down and stay down. Our technology applies deep learning and natural language processing to scour the Internet for app-related scam sites aimed at phishing and data theft.
When fake apps are detected, our systems will automatically collect comprehensive evidence of brand and trademark infringement and phishing credential theft used to then trigger complete fully-automated takedown and removal processes.
Our technology:
Scans 500+ stores
The Bolster platform monitors for threats across the traditional branded stores, known stores, and even rogue and unregulated stores to protect your brand from threats you might not even know to look for.
Automates takedowns
Our in-house machine learning tool automates the takedown process, removing unauthorized or fake apps & taking down scam sites globally in as little as 2 minutes.
Facilitates collaboration
With access to data-rich dashboards in the Bolster platform, your Brand, Legal, and Security teams can effectively work together on threat cases.
Continuously monitors
The Bolster platform monitors app store channels 24/7, including after a threat is removed to ensure future activity isn’t unnoticed.

Performance Metrics You Can Count On
With industry-leading fake app monitoring and takedown support, you can trust that Bolster will effectively defend against all fake app threats.
99.999% accurate
60 Seconds
6.5 Seconds
100ms

Guides and Resources
Bolster your digital risk protection program and learn more about industry trends and managing threats.
Identify Elusive Fake Apps With a Trusted Detection Tool
Protect Your Brand Reputation
Effectively Showcase Program Status
Protect Against Threats Beyond Common App Stores
Ensure Your App Store Monitoring and Fake App Takedown Program is Effective
Bolster’s expansive fake app store monitoring capabilities are a critical tool to add to your digital risk protection toolbox.
Identify Multitude of Fake Apps
Remove fake apps when detected on app stores, and stop unauthorized distribution & sale of your branded apps.
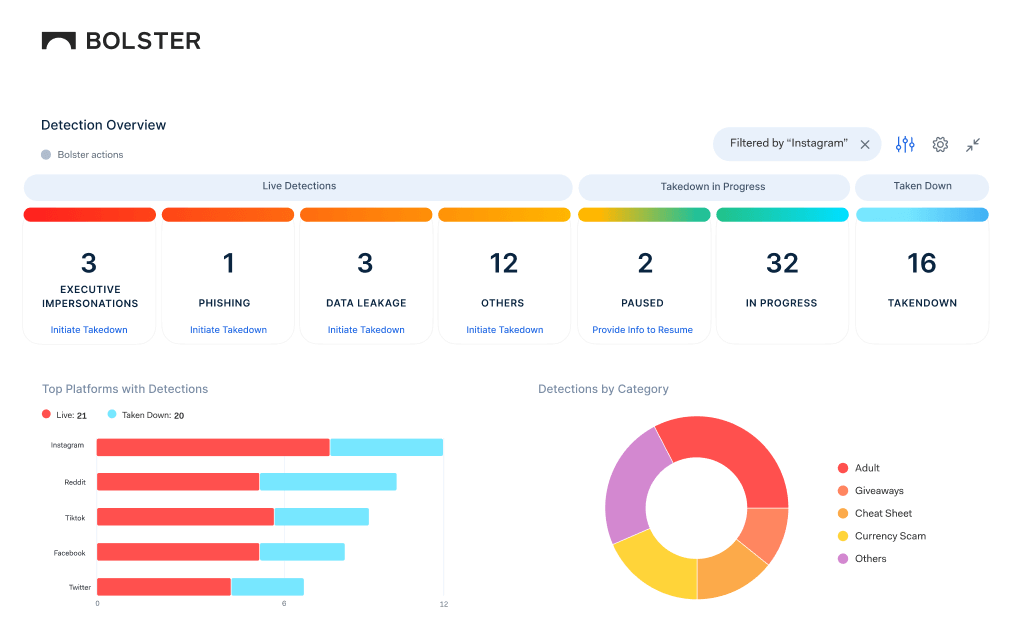
Visualize Threat Details for Better Defense
Continuous threat scans provide images of the detected threats, location data, IP addresses, and more.
Quickly Gather Evidence for Fake App Takedowns
Gather API and automated evidence-based submissions to send to hosting providers and registries to take down scam sites.
Continue Monitoring Post-Takedown
Once an fake app is taken down, continue to monitor for any indication of post-malicious activity.
How Bolster for App Store Monitoring Works
Our app store detection technology monitors for uses of your brand across hundreds of app stores, as well as fake app-related scams living on web domains.
Detect misuse & fake apps
Detect app-related scams
Next Generation
Fraud Prevention Platform
Remove fake & unauthorized apps
2Block & takedown malicious sites
App Store Detection
Domain Monitoring
Phishing Takedowns
Domain Takedowns
Ready to get started?
Explore what Bolster can do for you with a custom demo for your online business to understand existing online threats and how Bolster can take them down. Contact our sales team for pricing and packages today.
Get 24/7 Support
Start Your Integration
Frequently Asked Questions
What is app store monitoring?
App store monitoring involves using specialized tools and software to actively monitor and analyze app stores for unauthorized and fraudulent apps. It allows businesses to detect and identify fake, counterfeit, or malicious apps that may pose a threat to their brand reputation and customers. By conducting regular monitoring, businesses can take appropriate action to remove fraudulent apps from app stores and protect their users.
What cyber threats exist on app stores targeting businesses?
App stores are vulnerable to various types of cyber threats, including malware, phishing scams, data breaches, intellectual property infringement, false or misleading advertising, and unauthorized access to sensitive information. These threats can cause significant damage, such as compromising user privacy, tricking users into downloading fake apps, and even making fake purchases leading to financial losses, tarnishing your brand reputation, and even exposing users to malicious activities. Monitoring app stores helps businesses proactively identify and address these threats before they impact their customers or their business.
How can app store monitoring protect my business?
App store monitoring is essential for protecting businesses in several ways. First, it helps detect and remove fraudulent or unauthorized apps that impersonate a business, preventing brand reputation damage and customer deception.
Second, by identifying and eliminating malicious apps, businesses can safeguard their customers from malware, phishing attacks, and data breaches.
Additionally, app store monitoring ensures compliance with intellectual property rights, prevents false advertising that may misrepresent a business’s products or services, and promotes a safe and trustworthy app ecosystem for users.
How does Bolster monitor and takedown app store threats?
Bolster provides a comprehensive approach to monitor and takedown app store threats. Through advanced machine learning algorithms, Bolster’s platform continuously scans app stores, analyzing app metadata, user reviews, app colors and logos, and other indicators to identify suspicious or fraudulent use of customer branded assets.
Bolster combines automation with a team of expert analysts to gather threat data for quick takedowns. When a threat is confirmed, Bolster works closely with app store providers to report and take down unauthorized or malicious apps, ensuring a swift and effective response to protect businesses and their customers from app store threats.
Can fake apps be reported and taken down?
Yes, fake apps can be reported and taken down. App stores typically have a process for reporting fraudulent apps, and businesses can work with app store providers to submit reports and evidence of fake apps. Additionally, using specialized monitoring and takedown services can help businesses streamline this process and ensure timely removal of unauthorized apps.
What are the risks associated with fake apps?
Fake apps pose several risks for businesses and their customers. They can lead to financial losses through unauthorized transactions, expose users to malware or phishing attacks, collect personal information for fraudulent purposes, or damage a company’s brand reputation. By monitoring and removing these fake apps, businesses can protect their customers and maintain trust in their brand.