
Continuous Monitoring Throughout Entire Threat Lifecycle
Stay protected from phishing attacks, counterfeits, impersonations, and other malicious online activities at every stage – before and after detection and takedown. Get instant and continuous visibility into the threat in easy-to-use and intuitive analytics.
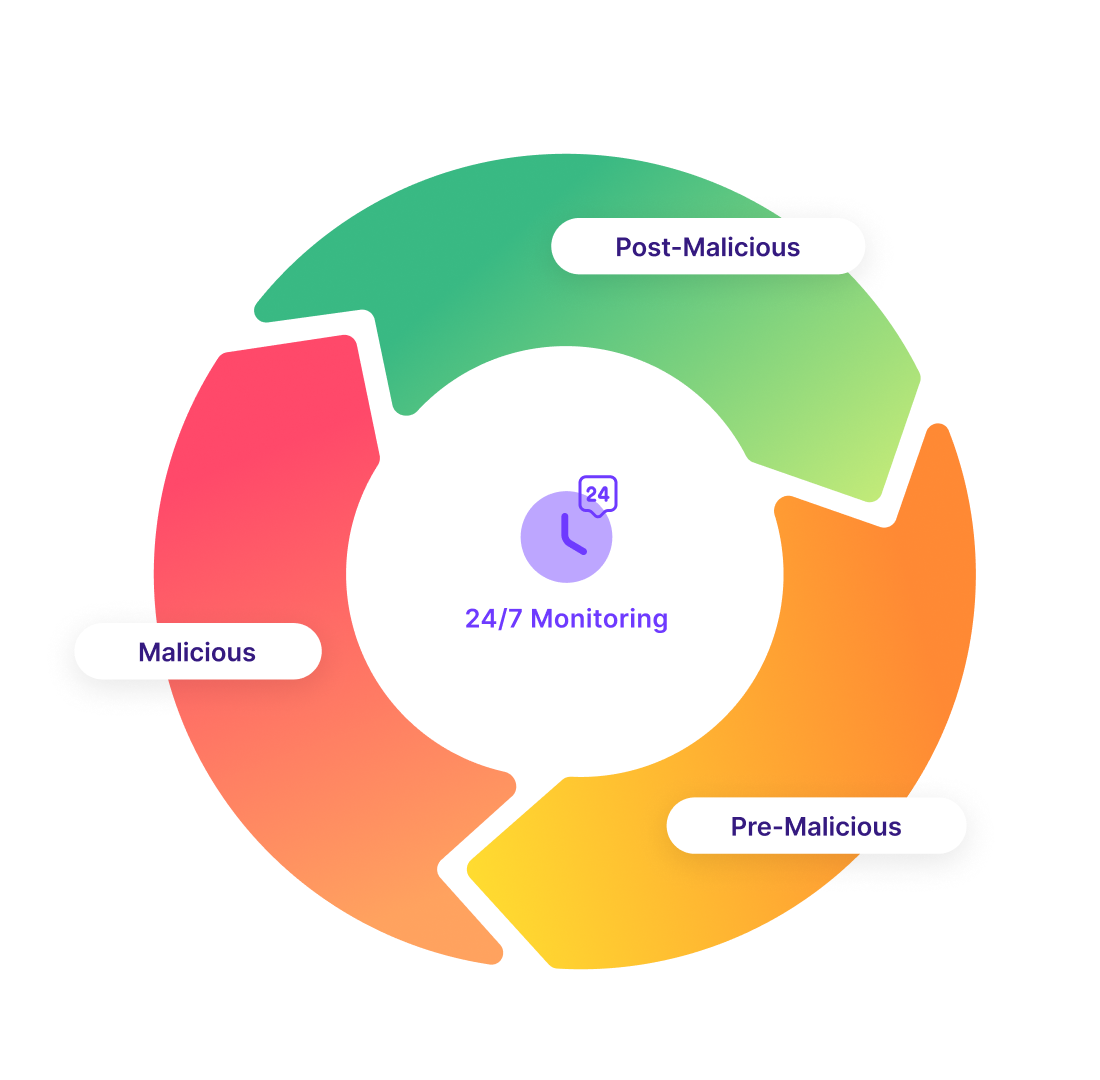
Widest Coverage for Threat Detection and Monitoring
With access to billions of data points, Bolster’s continuous monitoring provides an extensive scope to detect and analyze potential threats. With wide coverage, patented detection, and automated remediation technology, Bolster delivers coverage across a multi-channel digital ecosystem that most organizations do business in.
100+ Variants
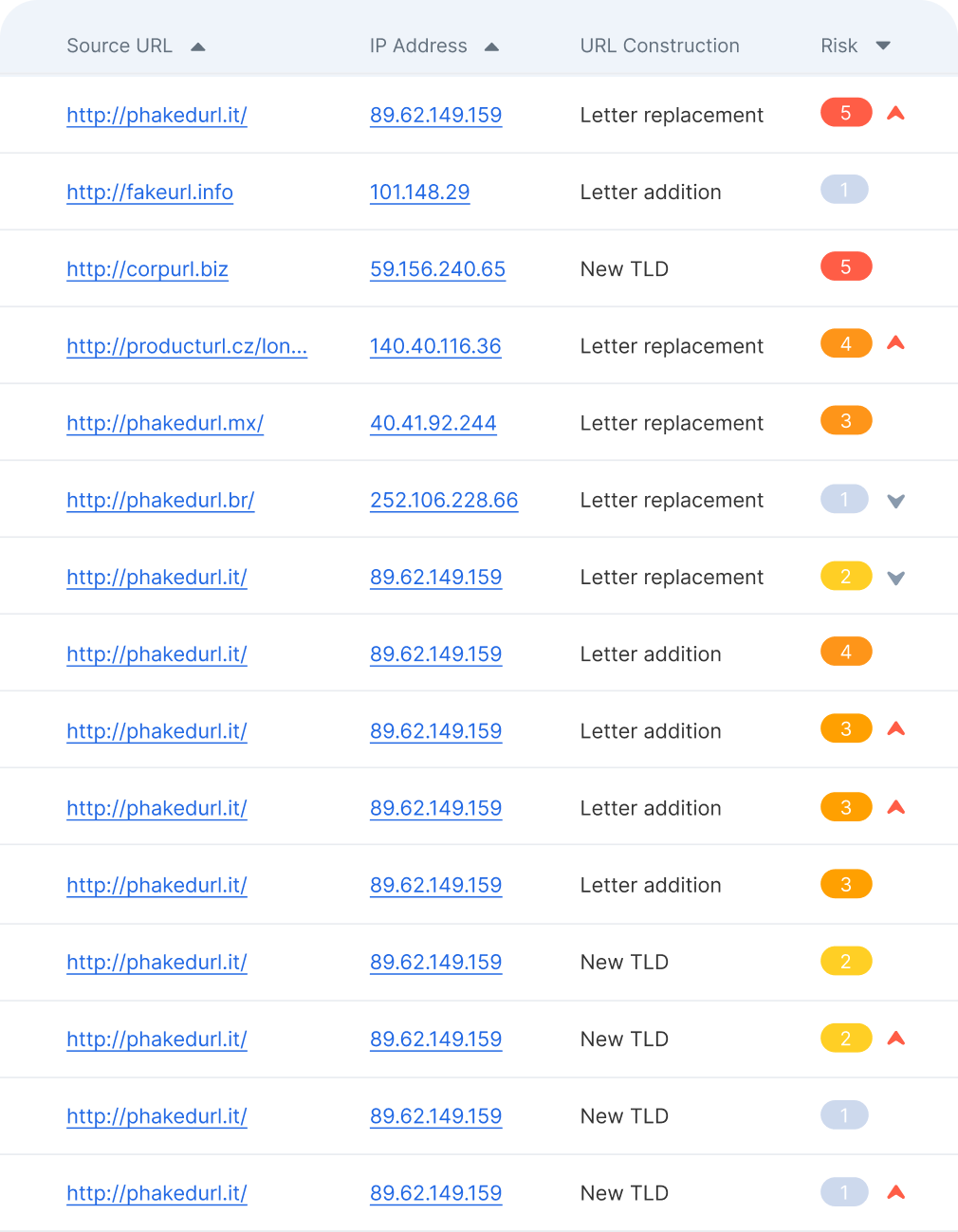
Typosquat variants surfaced for each domain, ranked by their level of risk to an organization
1200 TLDs Scanned
TLDs (Top Level Domains) supported per bulk scan by the industry’s leading URL scanner
15 Models used
Deep Learning models used for the highest confidence levels in detection of brand impersonations and scams
10 Billion+
Threat data points that have been trained on with deep learning since Bolster’s inception in 2017
Preventing Phishing Sites from Going Live
Bolster’s patented detection engine leverages threat algorithms and machine learning to detect typosquat variants before they go live, providing an extra layer of protection against phishing and scams attempts targeting your brand.

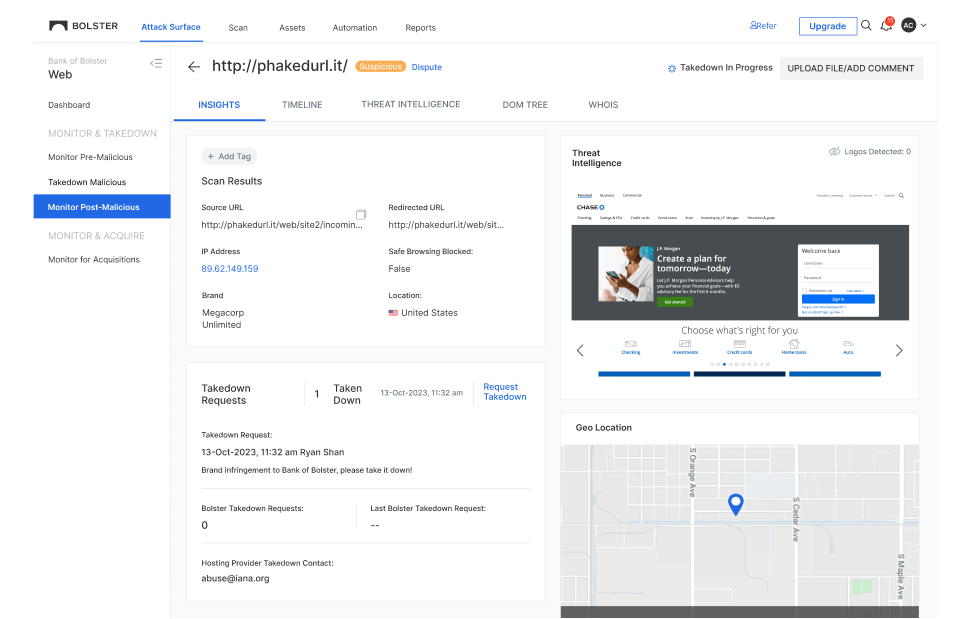
Continuous Post-Takedown Monitoring
Even after a phishing site is taken down, Bolster continue to monitor for any reoccurrences. Our proactive approach ensures that malicious online actor activities are swiftly identified and action is taken to prevent further attacks and re-emergence of sites, records, or accounts.
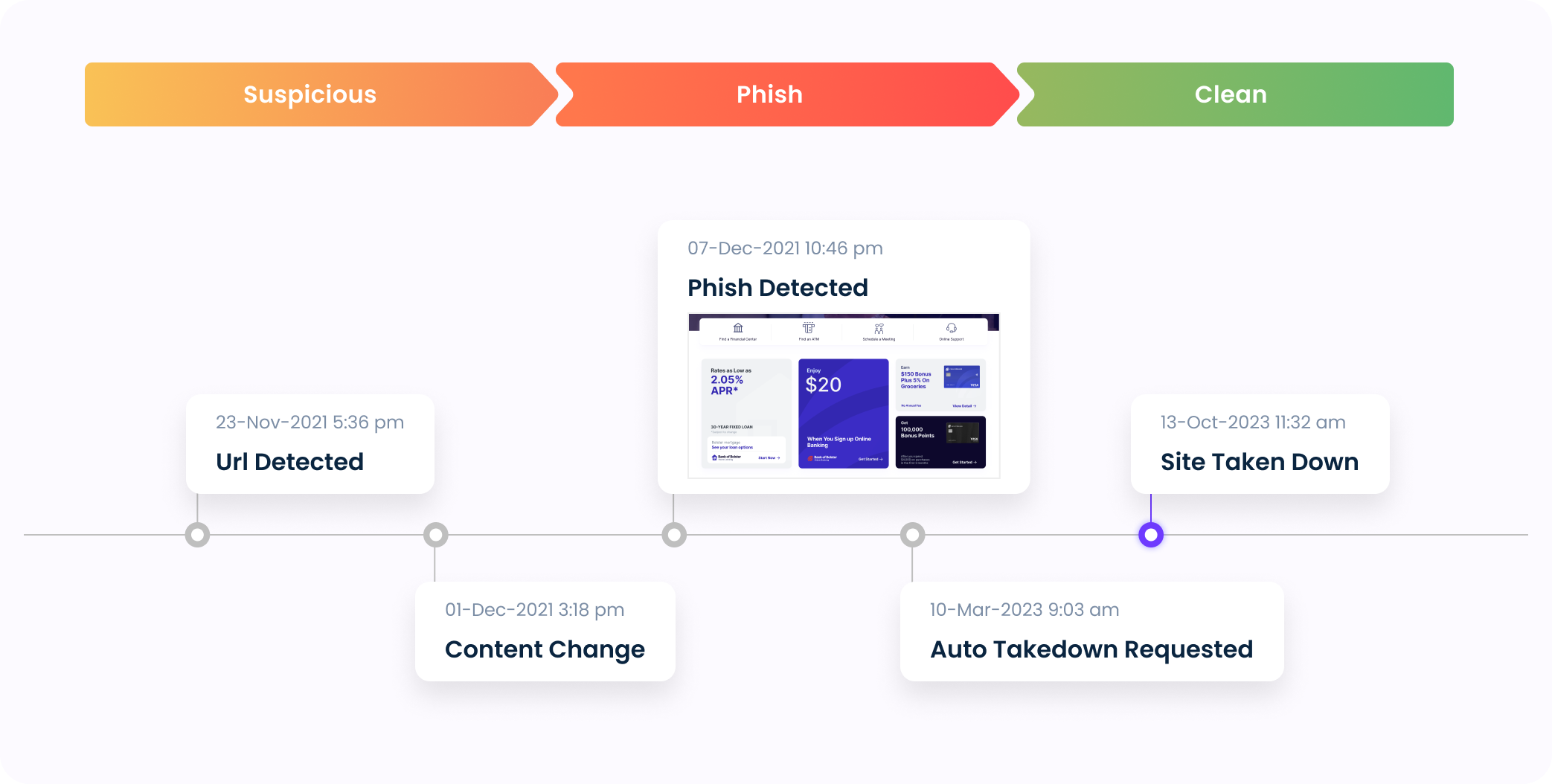
Actionable and Intuitive Visualization
Stay ahead of line threats with Bolster’s timeline view that the entire lifecycle from pre-malicious to post-malicious.
Bolster’s timeline view provides the most intuitive and visually engaging way to understand and address online threats. By presenting a chronological sequence of events, from the initial detection of typosquat variants to monitoring the record post takedown, the timeline view offers actionable visibility to identify patterns, track the progression of attacks, and quickly respond to mitigate risks. With Bolster’s timeline view, staying informed and taking decisive action against online phishing sites, impersonations, and scams has never been easier.

Let Bolster Protect You from Start to Finish
Bolster’s continuous monitoring provides ease-of-mind to the rapidly growing problem of phishing and scam activity across web, social, app stores, and even the dark web. With AI-powered detection and automated remediation, Bolster is the only platform that responds in real-time to identify threats and take them down without manual intervention. Here’s why Bolster’s continuous monitoring stands out:
Cover the Entire Internet
By constantly scanning the internet, Bolster ensures real-time detection of threats as soon as they emerge.
Identify Potential Risks
Bolster’s early warning detection system mitigates typosquat risks before they turn into a bigger problem.
Take Decisive Action
Take action where it matters the most, with continuous visibility into digital threats across websites, social media, app stores, and the dark web.
Keep Threats at Bay
Reduce future threats from resurfacing with continuous monitoring post-takedown and remediation.
Ready to get started?
Explore what Bolster can do for you with a custom demo for your online business to understand existing online threats and how Bolster can take them down. Contact our sales team for pricing and packages today.
Get 24/7 Support
Start Your Integration
Frequently Asked Questions
How does Bolster’s continuous monitoring work?
Bolster’s continuous monitoring works by leveraging deep learning and a live scanner to constantly monitor the internet, social media platforms, app stores, and the dark web for potential phishing and scam threats. It analyzes billions of data points and uses the industry’s most sophisticated techniques to detect and alert organization in real-time and automate the remediation of online threats. After take down of a threat, Bolster uses the same deep learning and scanner to monitor the internet for any potential re-emergence of the threat.
What makes Bolster’s continuous monitoring different from other solutions?
Bolster’s continuous monitoring stands out due to its wide coverage and comprehensive approach. With access to billions of data points and the ability to surface over 100 typosquat variants per domain, Bolster ensures that no potential threat goes unnoticed. Its use of the industry’s most advanced bulk URL scanner further enhances its capabilities, providing unmatched accuracy and agility. Lastly, Bolster emphasizes the important of usability and gives customers the most intuitive visualization of the lifecycle of the online threat through it’s online portal.
How quickly can Bolster detect threats with continuous monitoring?
Bolster’s continuous monitoring has an impressive mean-time-to-detect of 300 milliseconds, making it one of the fastest in the industry. This quick detection allows organizations to respond promptly and mitigate potential risks before they can cause significant damage.
Does continuous monitoring cover all types of online threats?
Yes, Bolster’s continuous monitoring is designed to detect a wide range of online threats, including phishing attempts, scam activities, brand infringement, typosquats, impersonations, and more. Its comprehensive approach ensures that organizations have complete visibility into their online presence and protection against a variety of online threats – irreverent to the digital channel that it conducts business.
Can Bolster’s continuous monitoring integrate with existing security systems?
Bolster understand the importance of seamless integration with existing security systems. Its continuous monitoring solution is built with flexibility in mind, allowing easy export into popular security platforms, threat intelligence feeds, and other security tools. In addition, Bolster does not need to sit in a customer environment and online needs approved texts, images, and logos to train on to start the detection and remediation process.





